The organization name is what the users will see on the sign-in page. If your…
Export all Microsoft 365 users MFA status report
You can check the Microsoft authentication methods status per user in the Microsoft Entra admin center (Azure AD). The disadvantage is that it will not show you detailed information. To get a list of all the users MFA status in a single CSV file, you need to run a PowerShell script. In this article, you will learn how to export all Microsoft 365 users MFA status report to a CSV file with PowerShell.
Table of contents
Microsoft 365 Azure user MFA status
Each user has a password to sign in, but that doesn’t mean they have Multi-factor authentication enabled. You can check which user in your organization has MFA enabled and which authentication methods they use. To get an overview of all the Microsoft 365 Azure users MFA status, it’s best to export it to a CSV file report with PowerShell.
In the Microsoft Entra admin center, you can view and download a list of the MFA status for all users. It shows which authentication methods are registered and the default MFA method for each user.
The difference is that you can’t easily find which users have configured a specific authentication method. To get a structured overview of the MFA status of all users, you need to use a PowerShell script and export it to a CSV file.
Microsoft MFA authentication methods
The PowerShell script will show an overview of which of the registered authentication methods are enabled for all Azure AD users.
| Authentication method | Description |
|---|---|
| Use an email address as part of the Self-Service Password Reset (SSPR) process. | |
| Fido2 | Use a FIDO2 Security Key to sign-in to Azure AD. |
| Microsoft Authenticator | Use Microsoft Authenticator to sign-in or perform multi-factor authentication to Azure AD. |
| Phone | The user can use a phone to authenticate using SMS or voice calls (as allowed by policy). |
| SoftwareOath | Use Microsoft Authenticator to sign in or perform multi-factor authentication to Azure AD. |
| TemporartAccessPass | Temporary Access Pass is a time-limited passcode that serves as a strong credential and allows onboarding of passwordless credentials. |
| WindowsHelloForBusiness | Windows Hello for Business is a passwordless sign-in method on Windows devices. |
Connect to Microsoft Graph PowerShell
Before you run the Export-MFAstatus.ps1 PowerShell script, you need to install the Microsoft Graph PowerShell module.
Run the below command to install the Microsoft Graph module.
Install-Module Microsoft.Graph -ForceNote: We also suggest you install the Microsoft Graph Beta module, or the script will not work.
Run the below command to install the Microsoft Graph Beta module.
Install-Module Microsoft.Graph.Beta -AllowClobber -ForceDownload MFA status PowerShell script
You can export the MFA status for all users to a CSV file. You need to create a folder named scripts if you don’t have it already.
Download the Export-MFAstatus.ps1 PowerShell script and save it in the C:\scripts folder.
Another method is to copy and paste the below code into Notepad. Give it the name Export-MFAstatus.ps1 and place it in the C:\scripts folder.
# Connect to Microsoft Graph API
Connect-MgGraph -Scopes "User.Read.All", "UserAuthenticationMethod.Read.All"
# Create variable for the date stamp
$LogDate = Get-Date -f yyyyMMddhhmm
# Define CSV file export location variable
$Csvfile = "C:\temp\MFAUsers_$LogDate.csv"
# Get all Azure users using the Microsoft Graph Beta API
$users = Get-MgBetaUser -All
# Initialize the results array
$results = @()
# Initialize progress counter
$counter = 0
$totalUsers = $users.Count
# Loop through each user account
foreach ($user in $users) {
$counter++
# Calculate percentage completion
$percentComplete = [math]::Round(($counter / $totalUsers) * 100)
# Define progress bar parameters with user principal name
$progressParams = @{
Activity = "Processing Users"
Status = "User $($counter) of $totalUsers - $($user.UserPrincipalName) - $percentComplete% Complete"
PercentComplete = $percentComplete
}
Write-Progress @progressParams
# Create an object to store user MFA information
$myObject = [PSCustomObject]@{
DisplayName = "-"
UserPrincipalName = "-"
MFAstatus = "Disabled" # Initialize to "Disabled"
Email = "-"
Fido2 = "-"
MicrosoftAuthenticatorApp = "-"
Phone = "-"
SoftwareOath = "-"
TemporaryAccessPass = "-"
WindowsHelloForBusiness = "-"
}
$myObject.UserPrincipalName = $user.UserPrincipalName
$myObject.DisplayName = $user.DisplayName
# Check authentication methods for each user
$MFAData = Get-MgBetaUserAuthenticationMethod -UserId $user.UserPrincipalName
foreach ($method in $MFAData) {
Switch ($method.AdditionalProperties["@odata.type"]) {
"#microsoft.graph.emailAuthenticationMethod" {
$myObject.Email = $true
$myObject.MFAstatus = "Enabled"
}
"#microsoft.graph.fido2AuthenticationMethod" {
$myObject.Fido2 = $true
$myObject.MFAstatus = "Enabled"
}
"#microsoft.graph.microsoftAuthenticatorAuthenticationMethod" {
$myObject.MicrosoftAuthenticatorApp = $true
$myObject.MFAstatus = "Enabled"
}
"#microsoft.graph.phoneAuthenticationMethod" {
$myObject.Phone = $true
$myObject.MFAstatus = "Enabled"
}
"#microsoft.graph.softwareOathAuthenticationMethod" {
$myObject.SoftwareOath = $true
$myObject.MFAstatus = "Enabled"
}
"#microsoft.graph.temporaryAccessPassAuthenticationMethod" {
$myObject.TemporaryAccessPass = $true
$myObject.MFAstatus = "Enabled"
}
"#microsoft.graph.windowsHelloForBusinessAuthenticationMethod" {
$myObject.WindowsHelloForBusiness = $true
$myObject.MFAstatus = "Enabled"
}
}
}
# Add user object to results array
$results += $myObject
}
# Export user information to CSV
$results | Export-Csv -Path $Csvfile -NoTypeInformation -Encoding UTF8
Write-Host "Script completed. Results exported to $Csvfile." -ForegroundColor CyanExport MFA status report to CSV
Before you export, you need to create a folder named temp in the (C:) drive if you don’t have it already.
To export the MFA status report for all users, you need to run PowerShell as administrator.
Run the Export-MFAstatus.ps1 PowerShell script.
C:\scripts\.\Export-MFAstatus.ps1It will connect to MS Graph, where you must sign into your admin account.
- Enter password
- Click Sign in
Permission is requested to verify the consent.
- Enable Consent on behalf of your organization
- Click Accept
The PowerShell output shows a progress bar and lets you know when the script completes. It will find and export the MFA status for all the users in your organization.
Welcome To Microsoft Graph!
Script completed. Results exported to C:\temp\MFAUsers_202309191236.csv.You can find the CSV file in the C:\temp folder. Open the CSV file with an application like Microsoft Excel to see the results.
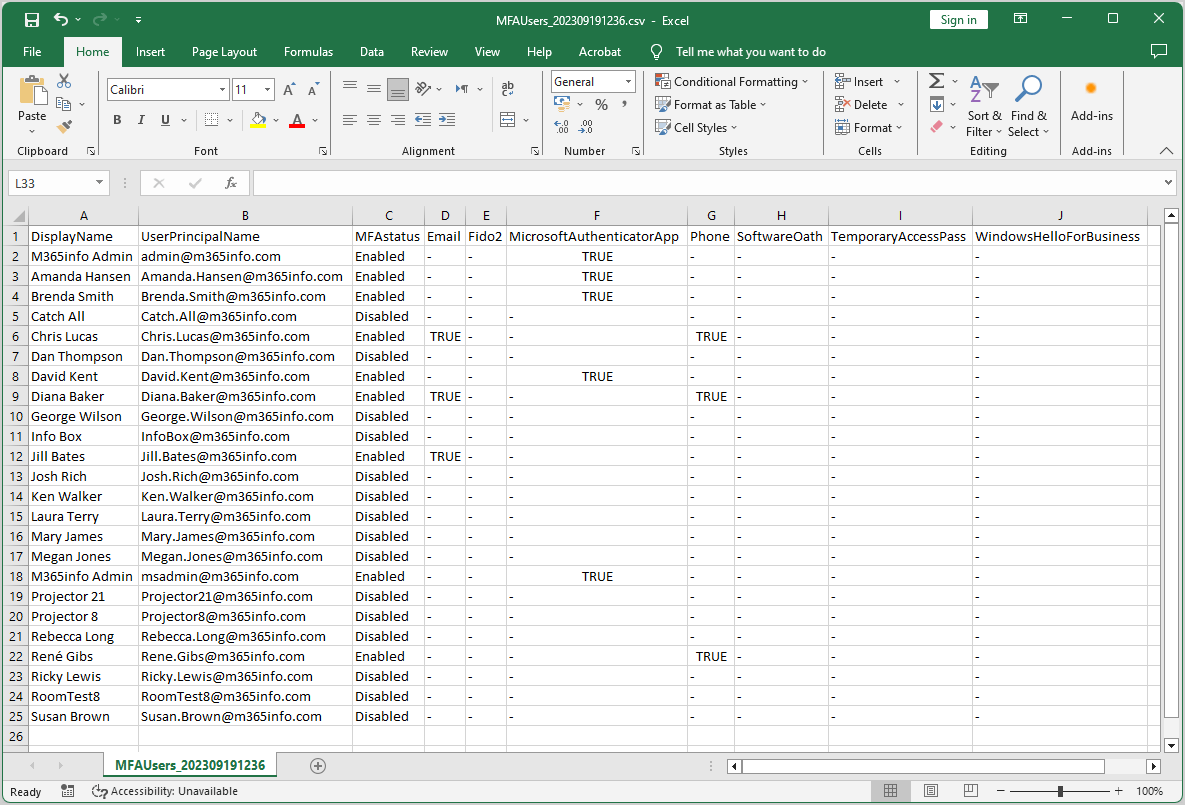
This is the final result of all Microsoft 365 users MFA status in our organization. If a user has MFA status Disabled, they only have a password to sign in without any other authentication methods.
- Enabled: MFA is set up for the user account
- Disabled: MFA is not set up for the user account
Note: Remind the user accounts that have MFA status Disabled in the list to configure MFA.
Did you manage to export all Microsoft 365 users MFA status with Microsoft Graph PowerShell?
Read more: Reset MFA for Microsoft 365 user »
Conclusion
You learned how to export all Microsoft 365 users MFA status report. With Microsoft Graph PowerShell, you can run the Export-MFAstatus.ps1 PowerShell script to export the MFA status of each user to a CSV file. This report shows which users have MFA enabled and which authentication methods they use.
Did you enjoy this article? You may also like Bulk create Microsoft 365 users with CSV file. Don’t forget to follow us and share this article.

Exactly what I was looking for. Unfortunately it errors out.
Get-MgBetaUser : One or more errors occurred.
At line:11 char:1
+ $users = Get-MgBetaUser -All
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Get-MgBetaUser_List], AggregateException
+ FullyQualifiedErrorId : System.AggregateException,Microsoft.Graph.Beta.PowerShell.Cmdlets.GetMgBetaUser_List
You must install the Microsoft Graph Beta module (as shown in the article).
This script get all users with MFA even if the policy was not enabled in the admin side.
For my part, I wanted to get only the users where the admin enabled in the admin panel, and for this, you must use the Get-MgBetaReportAuthenticationMethodUserRegistrationDetail with the -Filter parameter set to “IsMfaCapable eq true”.
That was the command I wanted, but didn’t know existed. Thanks, Tristan!