Some things can only be done in Exchange Online using PowerShell. With Exchange Online PowerShell,…
How to simulate spam mail
After you set up a third-party spam filter in your organization or configure adjustments in Exchange Online, you want to check if the spam detection works. The best way to test your existing mail security infrastructure is to send spam mail and analyze the content. In this article, you will learn how to simulate spam mail.
Table of contents
Introduction to simulating spam mail
In a modern mail environment, it is important to implement some security mechanism that will protect your mail infrastructure from spam mail and other threats.
Exchange Online Protection (EOP) is a cloud-based filtering service that protects your organization against spam, malware, and other email threats. EOP is included in all Microsoft 365 organizations with Exchange Online mailboxes.
If you want to implement a mail security gateway, you need to know if your mail security gateway is functioning correctly and what will happen otherwise.
So we will define a specific rule where our mail security gateway recognizes spam mail and sends a notification to a designated recipient.
How to simulate spam mail
We will show an example where user A (outside organization) sends a spam email message to recipient B (inside organization).
In our case, a user with a Gmail account will send spam mail to a recipient (Stephen.Hunter@m365info.com) in our organization.
Stephen has a user mailbox hosted in Microsoft 365 (Exchange Online server).
Note: To simulate the scenario of spam mail, the sender and the recipient must be recipients from different organizations. So you can’t test the spam mail option if the sender and the destination recipient belong to the same Microsoft 365 tenant, because the verification check is not implemented by the EOP server.
1. Send spam mail
You can easily create an email message that our system will identify as spam, and the implementation of simulating spam mail is straightforward.
All you need to do is create an email message that includes a predefined text string and send it to the destination recipient, which is protected by the mail security gateway.
The Apache SpamAssassin organization has developed a special procedure to implement this clever trick.
Follow the steps below to send spam mail:
- Copy the following text string below
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X- Paste the text string in the mail body
- Send the email message to the recipient (Stephen.Hunter@m365info.com)
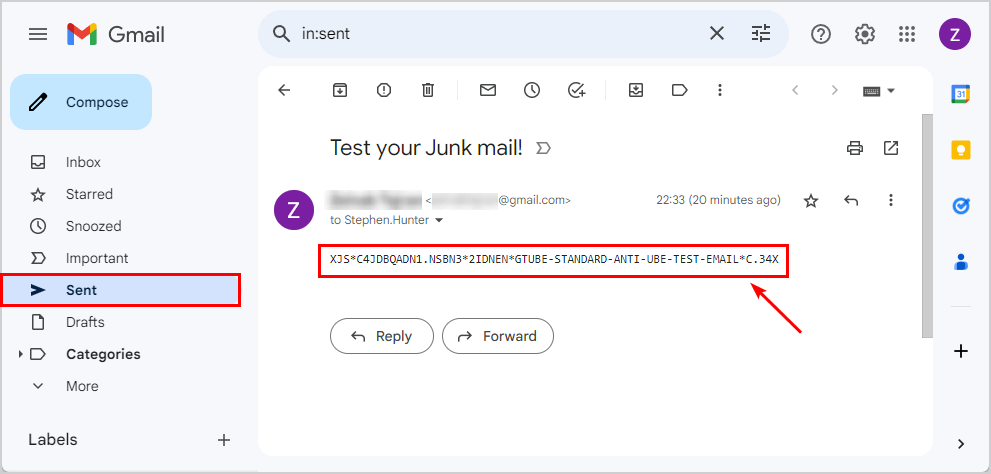
2. Receive spam mail
In the below picture, you can see the Outlook mail of Stephen.Hunter@m365info.com. When you open the Junk Email folder, you can find the email message you sent.
In a Microsoft 365 environment, the component that serves as a mail security gateway is the EOP (Exchange Online Protection) server. The EOP server examines and checks each email message sent to a Microsoft 365 recipient.
When the email message reaches the recipient’s mailbox, it will automatically be sent to the Junk Email folder because of the high value of the SCL.
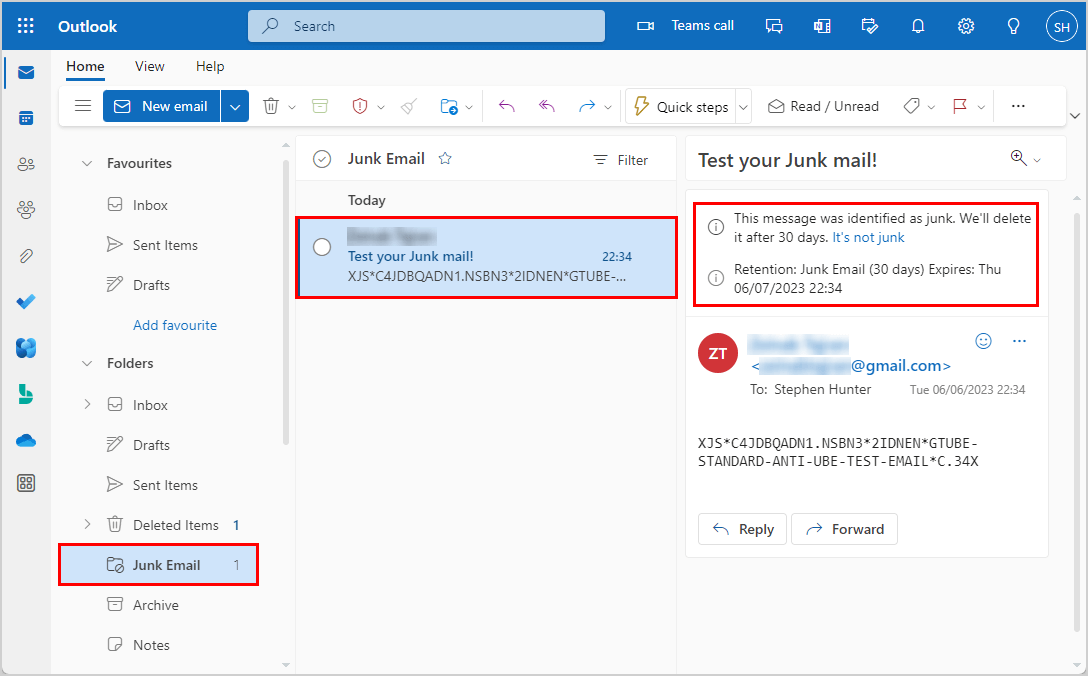
3. View mail message header content
You need to understand how the Microsoft 365 EOP server stamps specific email messages as spam mail. In an Exchange based environment, the method for classifying email messages as spam is by defining a particular value in the SCL parameter.
EOP recognizes the text string in the email message and classifies the email message as spam mail by setting the value of the SCL (Spam Confidence Level).
See the below table that explains the SCL.
| SCL | Definition |
|---|---|
| -1 | Skipped spam filtering. |
| 0, 1 | Spam filtering determined the message wasn’t spam. |
| 5, 6 | Spam filtering marked the message as spam. |
| 8, 9 | Spam filtering marked the message as high confidence spam. |
| 2, 3, 4, and 7 | Not used by spam filtering. |
When the email message reaches the recipient mailbox, because of the high value of the SCL, the mail will be sent to the Junk Email folder.
View the information of the mail header
To be able to see the information that is included in the email message, we will be using the OWA mail client. We will fetch the content of the mail header of the spam mail sent to Stephen.
- Open the specific email message
- Click on the three dots to open a selection pane
- Select View > View message details
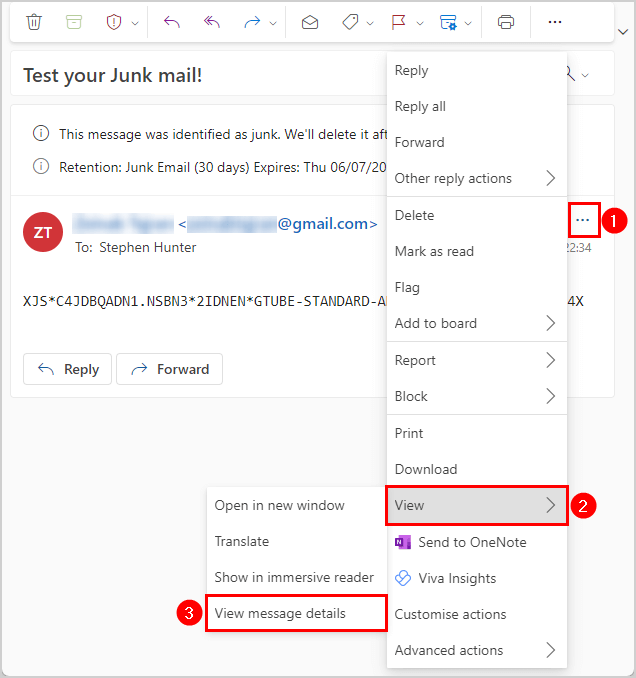
It shows the content of the specific mail header.
- Select the content of the mail header
- Copy the content by right-clicking and choose Copy (CTRL + C)
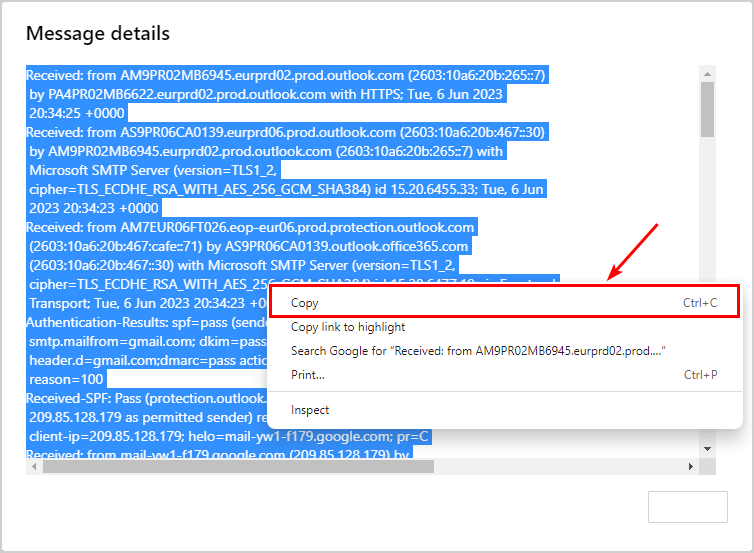
In the next step, we will use the copied content to analyze it.
4. Check with Microsoft Message Header Analyzer
We want to show how to use the Microsoft Message Header Analyzer for analyzing the mail header content. Of course, there are a couple of other free web-based tools that we can use to analyze a mail header.
- Go to Message Header Analyzer
- Paste the copied email header content
- Click Analyze headers
In the below picture, you can see the different mail fields included within the mail header.
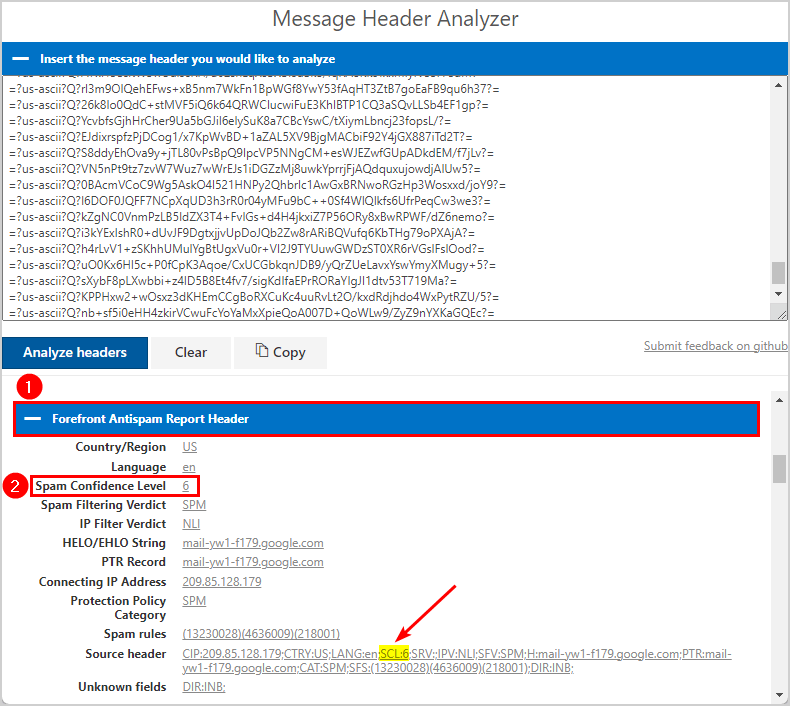
- Go to the specific mail field header > Forefront Antispam Report Header
- Look for the Spam Confidence Level
In this field, the Spam Confidence Level value of the email message is in our example 6. Indicating that the EOP (Exchange Online Protection) server has classified the email message as spam.
You can also find the SCL:6 in the Source header.
That’s it!
Read more: Enable reply all storm protection in Exchange Online »
Conclusion
You learned how to simulate spam mail to test your organization’s spam filter. After you send and receive the spam mail, you can analyze it in the Microsoft Message Header Analyzer. The email message will display the Spam Confidence Level (SCL) classified as spam.
Did you enjoy this article? You may also like Reset MFA for Microsoft 365 user. Don’t forget to follow us and share this article.


I love how in depth this is. Thanks teach.
Thanks!