You get an error when you force delete a Microsoft 365 mailbox from the recycle…
Configure Conditional Access policy in Microsoft Entra
Microsoft recommends to set up an MFA with a Conditional Access policy when you have Microsoft Entra ID P1 or P2 license. This means you need to disable the security defaults and per-user MFA first so there will be no issues. In this article, you will learn how to configure a Conditional Access policy in Microsoft Entra admin center and with PowerShell.
Table of contents
What is Conditional Access policy
Conditional Access allows you to enforce access requirements when specific conditions occur.
A Conditional Access policy is an if-then statement of Assignments and Access controls. For example, If a user wants to access an application or service like Microsoft 365, then they must perform multifactor authentication to gain access.
See the table below for some Conditional Access policies examples:
| Conditions | Controls |
|---|---|
| If a user is outside the company’s network IP address. | The user is required to sign in with multi-factor authentication (MFA). |
| If a user in the group “Sales” signs in. | The user is required to be an Intune compliant. |
Conditional Access policies allow you to build conditions that manage security controls that can block access and require multifactor authentication.
Use Conditional Access policies to apply the right access controls when needed to keep your organization secure.
License requirements
You need one of the following requirements to configure Conditional Access:
- Business Premium license
- Microsoft Entra ID P1 license
- Microsoft Entra ID P2 license
Disable security defaults
Before implementing Conditional Access policies in your organization, you must disable security defaults.
Microsoft protects every tenant and enables security defaults. This is a problem if you want to configure a Conditional Access policy because once you want to create the CA policy, you will get the below error.
Error: Failed to create ‘Require multifactor authentication for admins’
An unexpected error occurred, please try again later
To prevent this error, you need to disable the security defaults for your organization before you configure a Conditional Access policy.
Disable Security defaults in Microsoft Entra ID
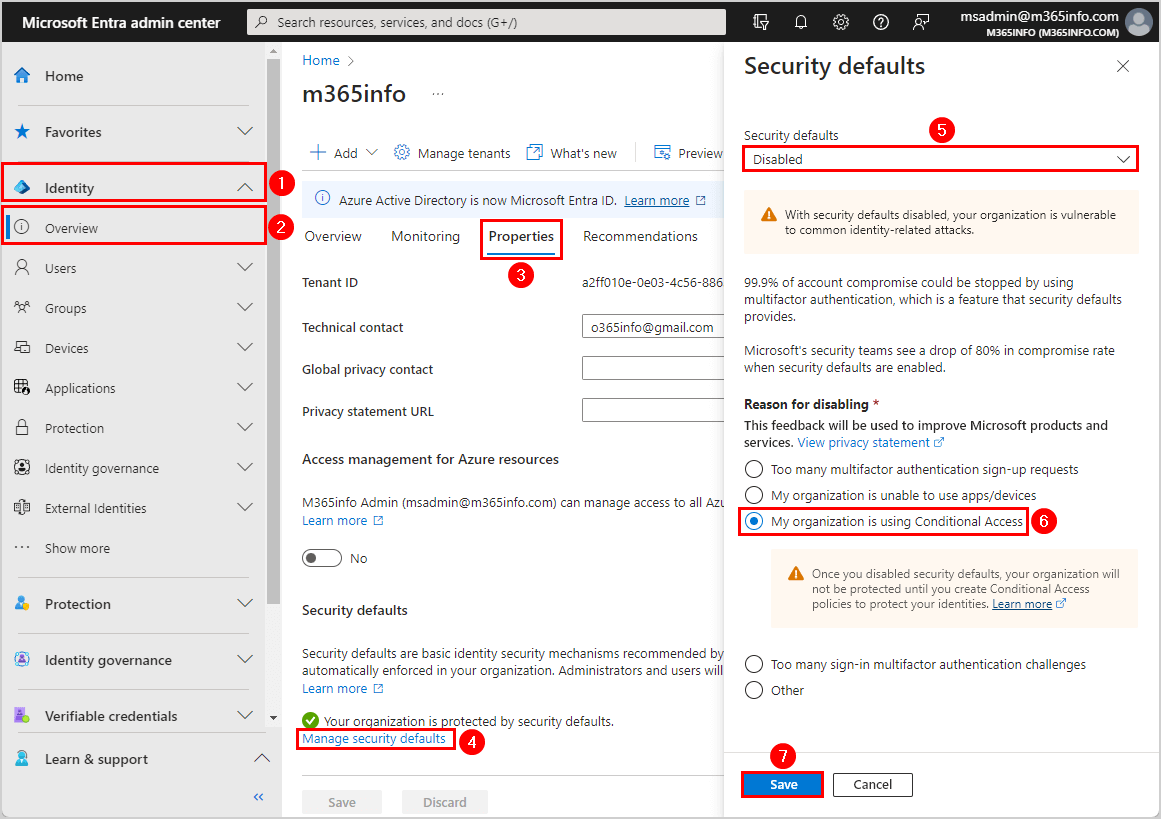
Disable security defaults for your organization in the below steps:
- Sign in Microsoft Entra admin center
- Click Identity > Overview
- Click Properties tab
- Scroll down > Click Manage security defaults
- Select Disabled
- Select My organization is using Conditional Access
- Click Save
- Click Disable
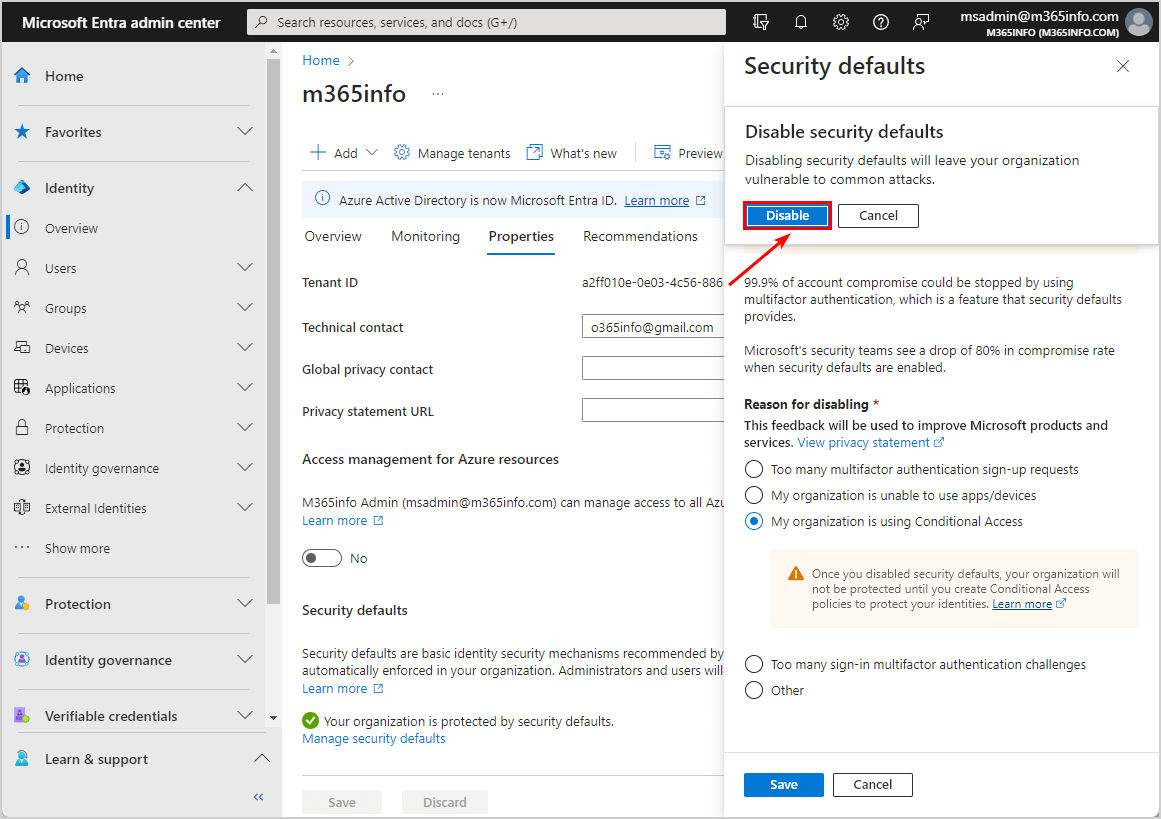
You did successfully disable security defaults.
Disable security defaults with Microsoft Graph PowerShell
You can also disable security defaults with Microsoft Graph PowerShell for your organization, by following these steps:
- First, you need to install the Microsoft Graph module.
Install-Module Microsoft.Graph -Force- Connect to Microsoft Graph with the below scopes.
Connect-MgGraph -Scopes "Policy.Read.All", "Policy.ReadWrite.ConditionalAccess"- Disable the security defaults with the below PowerShell command.
Update-MgPolicyIdentitySecurityDefaultEnforcementPolicy -IsEnabled:$false- Run the below PowerShell command to check if you disabled the security defaults
Get-MgPolicyIdentitySecurityDefaultEnforcementPolicy | ft DisplayName, IsEnabled- The PowerShell output shows the Security Defaults value set to False.
DisplayName IsEnabled
----------- ---------
Security Defaults FalseCreate Conditional Access policy in Microsoft Entra
There are two methods to create a Conditional Access policy:
- Create new policy from templates
- Create new policy manually
Create new Conditional Access policy from templates
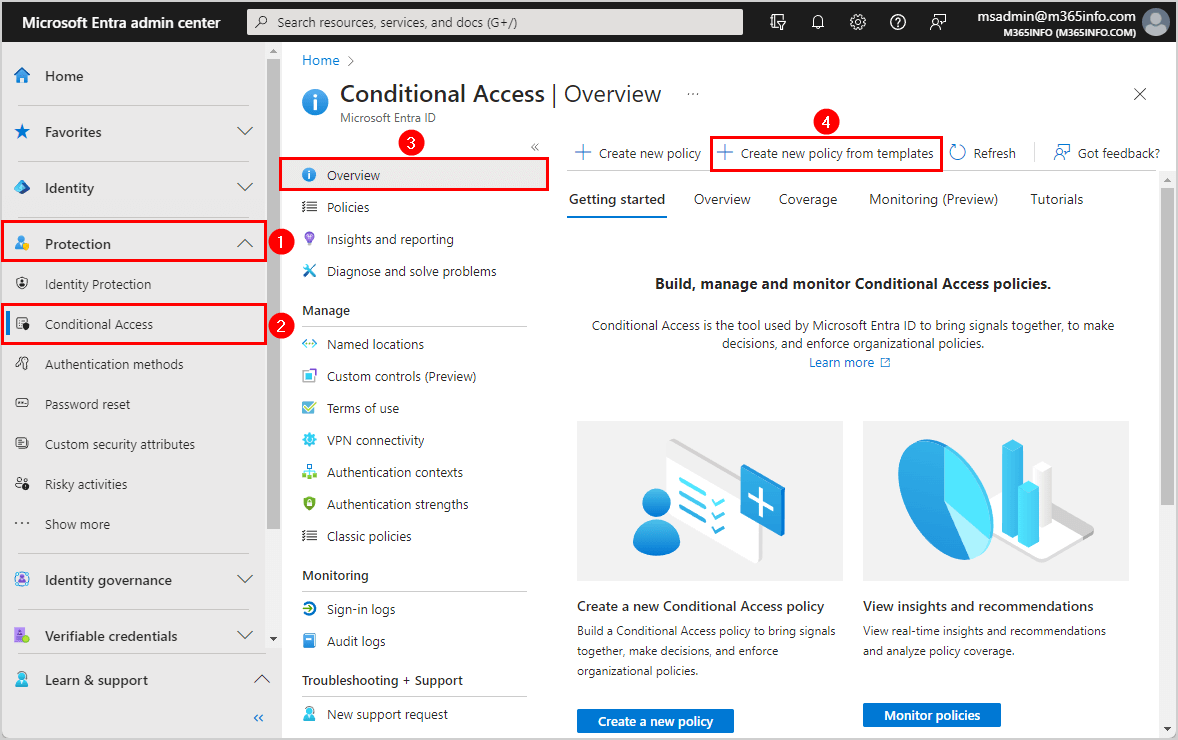
To create a new CA policy from a template, follow these steps:
- Sign in Microsoft Entra admin center
- Click Protection > Conditional Access
- Go to Overview
- Click Create new policy from templates
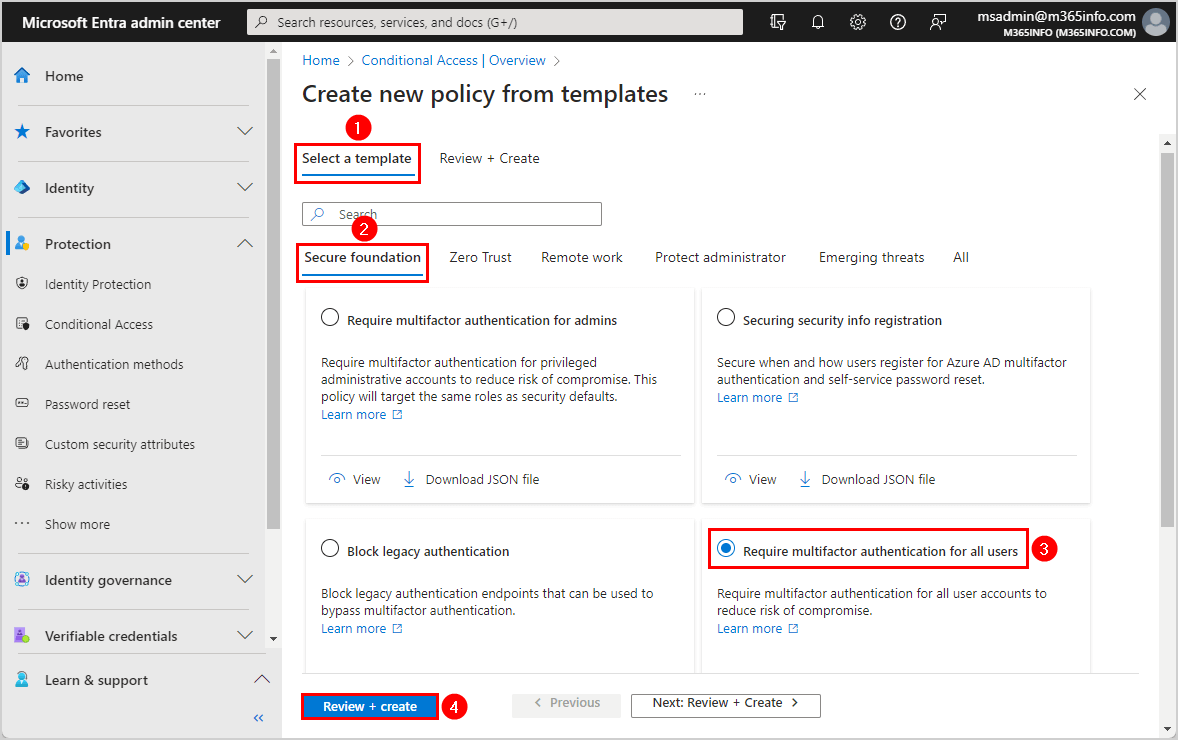
- Go to Select a template
- Go to Secure foundation
- Select the template Require multifactor authentication for all users
- Click Review + Create
- Select Policy state On
- Click Create
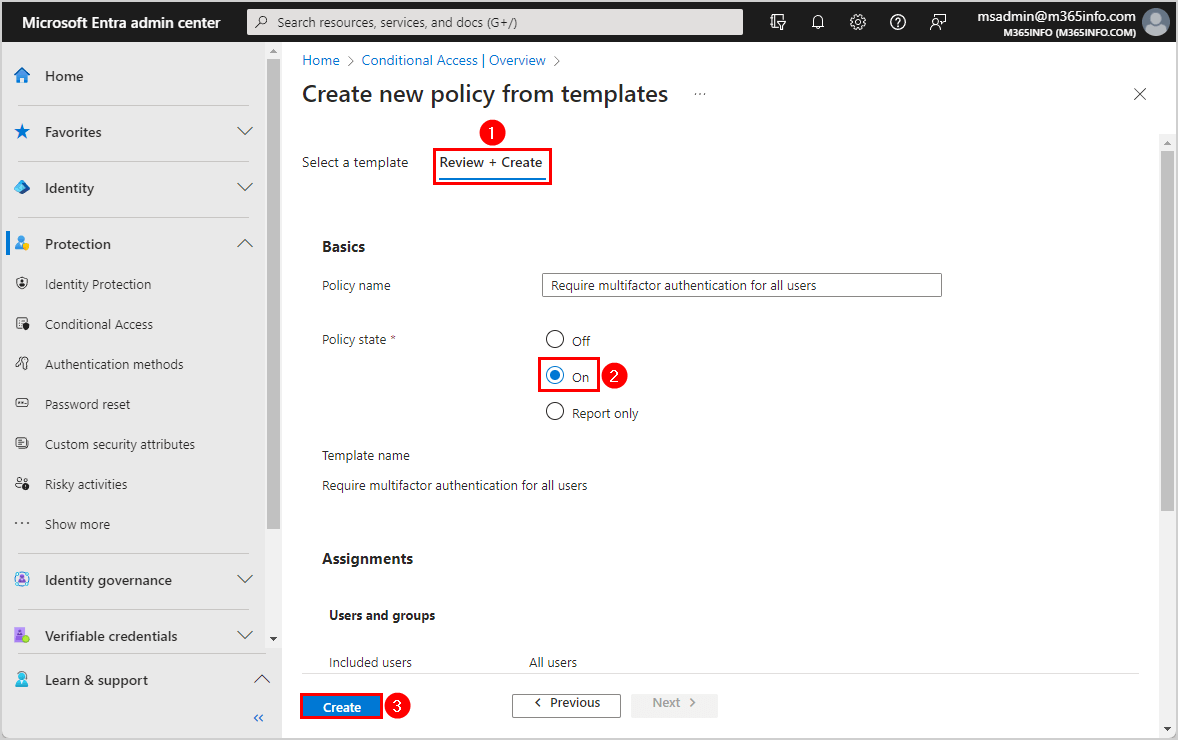
A notification appears that it successfully created the CA policy: Require multifactor authentication for admins. The policy will be enabled in a few minutes if the Policy state is set to On.
Create new Conditional Access policy manually
To create a new CA policy from manually, follow the below steps:
- Sign in Microsoft Entra admin center
- Click Protection > Conditional Access
- Go to Overview
- Click Create new policy
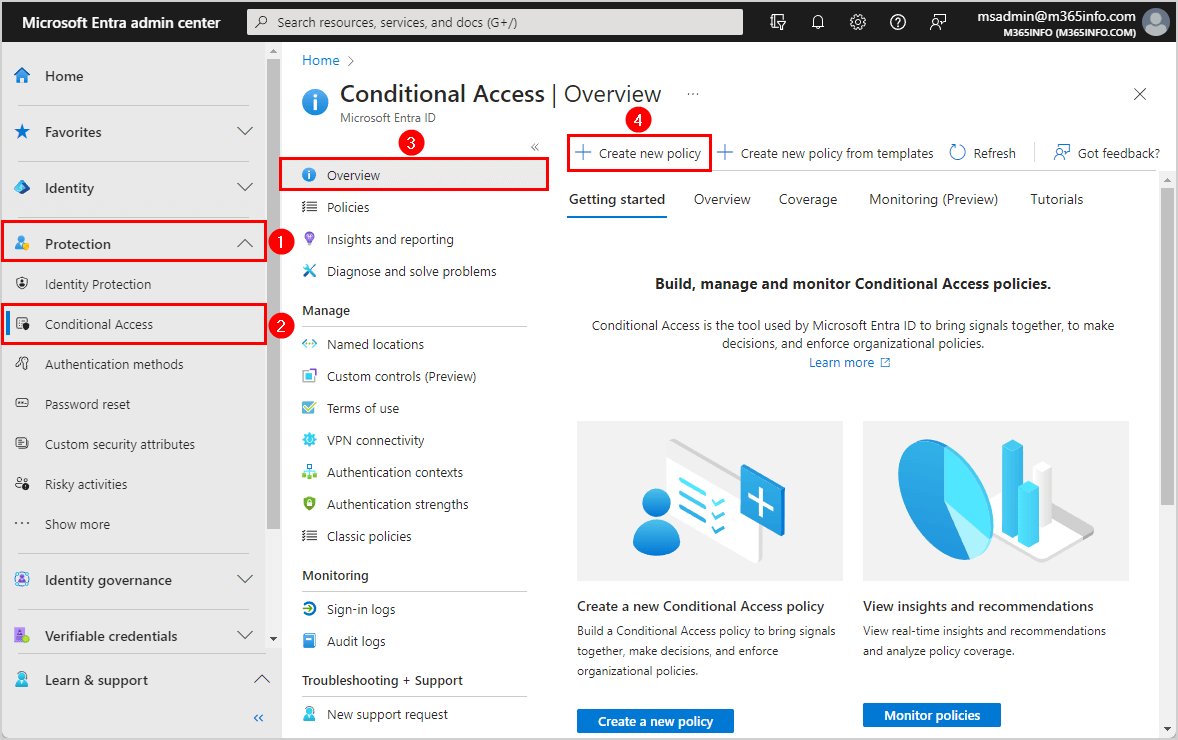
- Type the name MFA all users
- Click Users
- Click Include
- Select All users
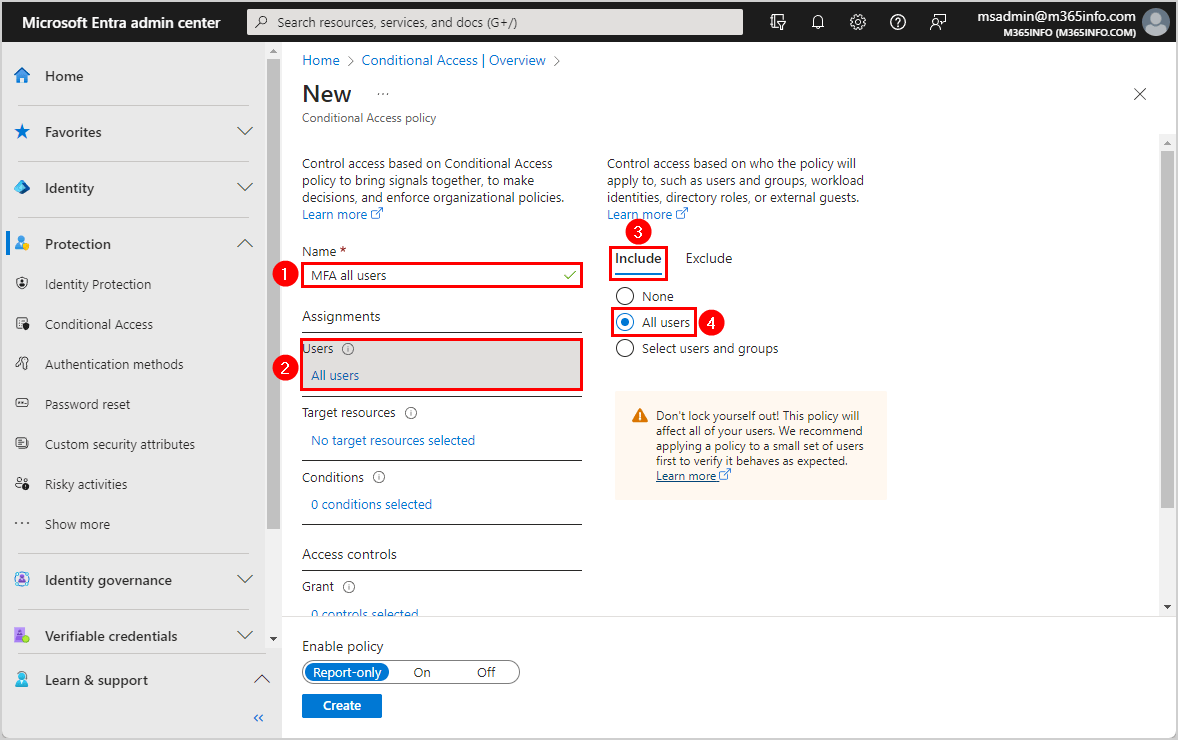
- Click Exclude
- Select Users and groups
- Select the users and groups
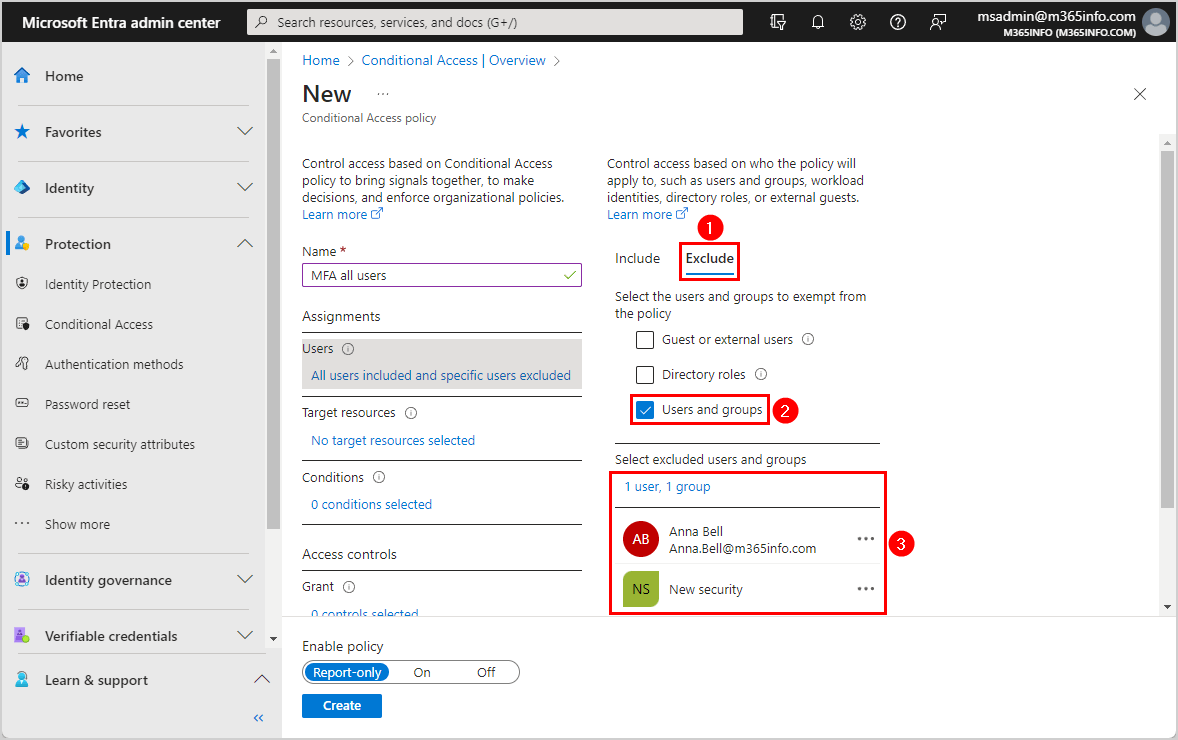
- Click Target resources
- Select Cloud apps
- Click Include
- Select All cloud apps
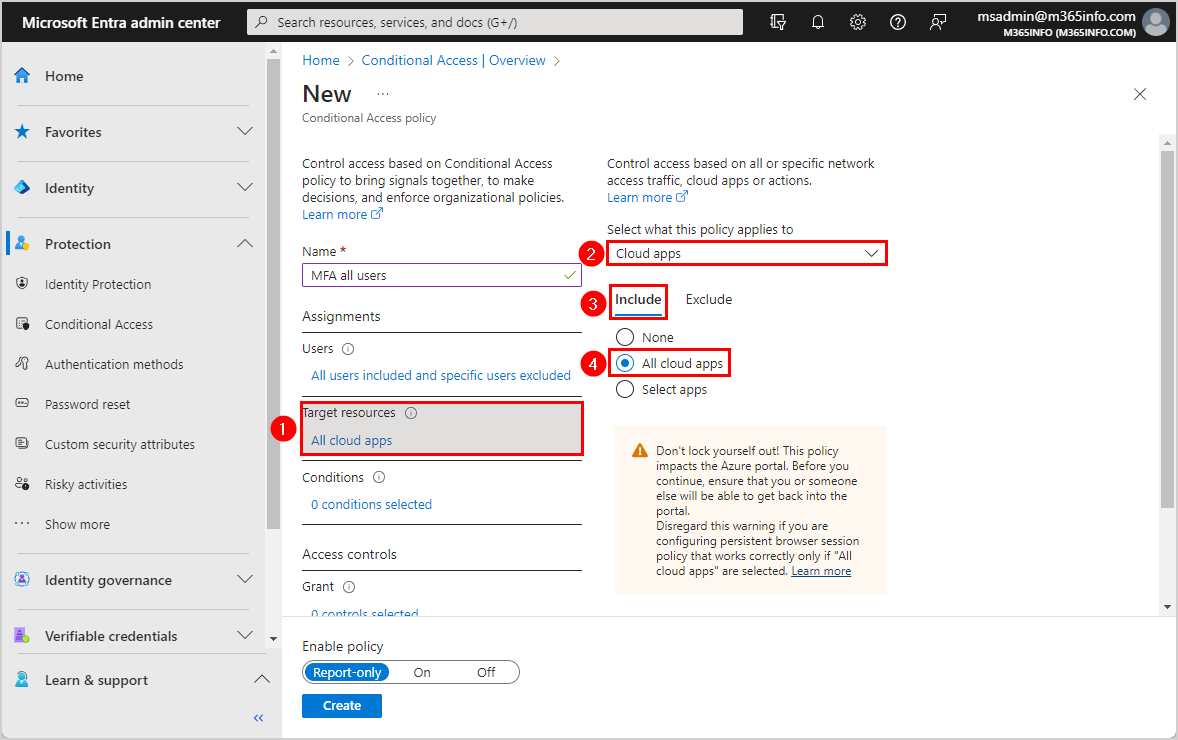
- Click Conditions
- Click Locations
- Configure > Select Yes
- Click Include
- Select Any location
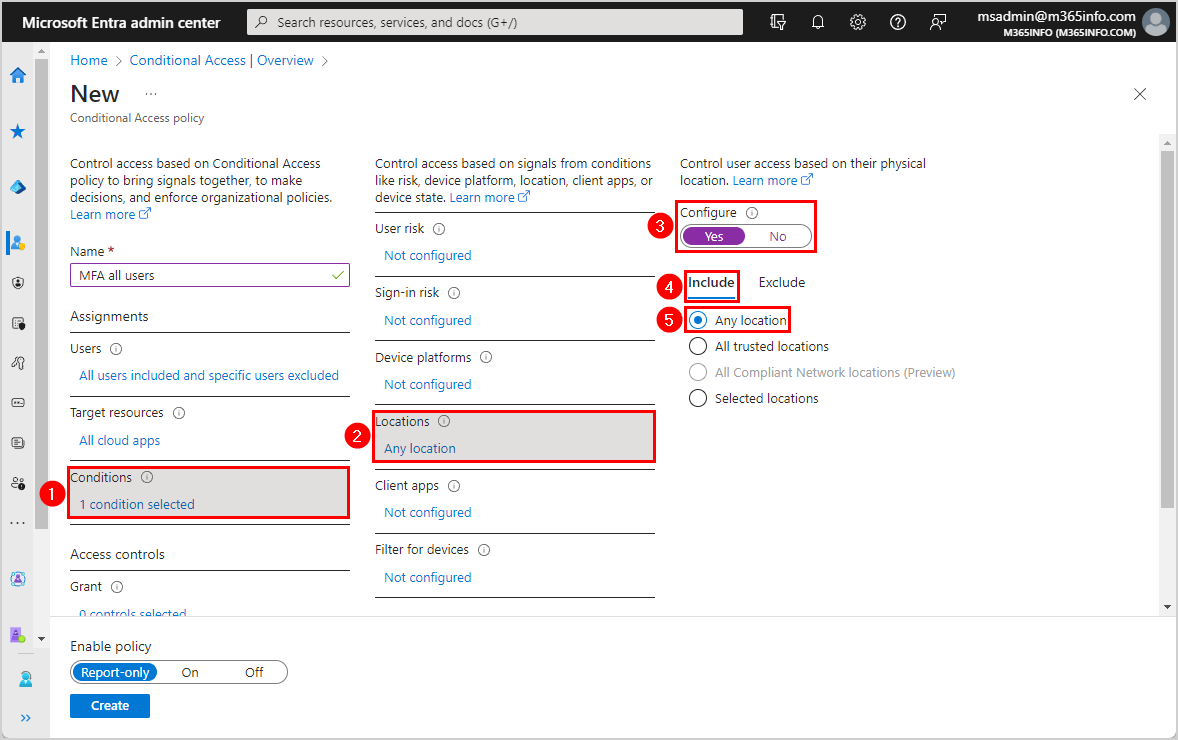
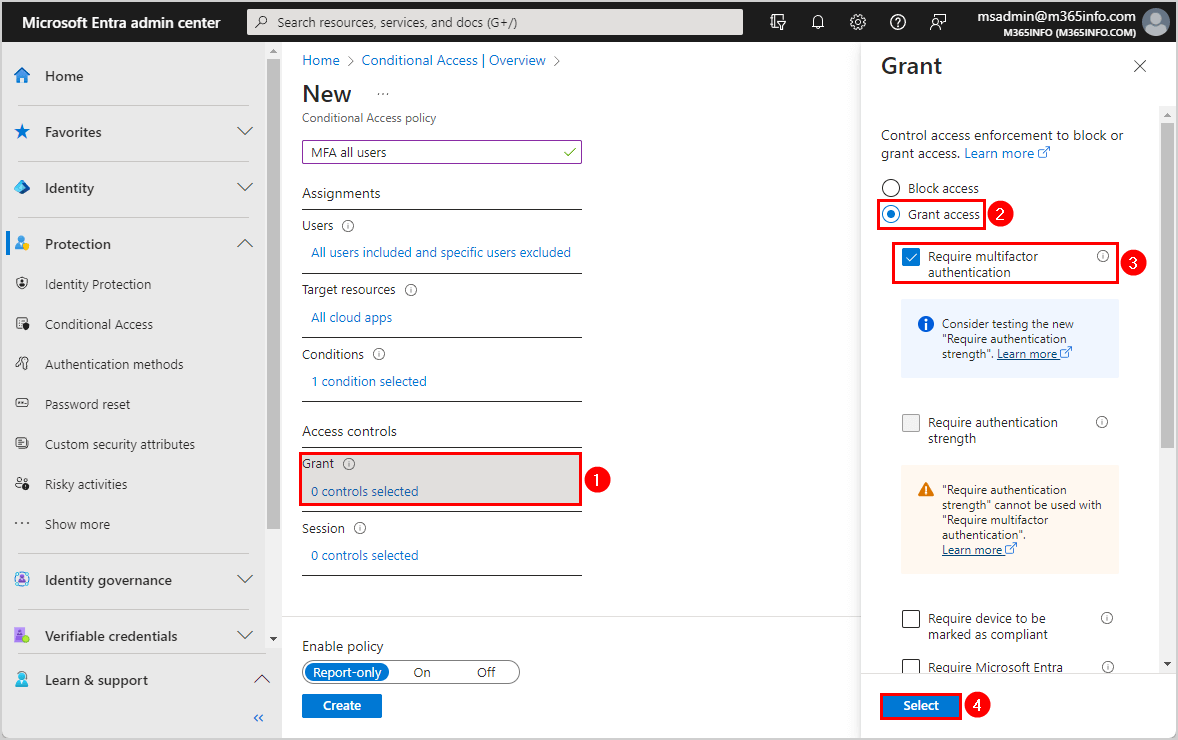
- Click Grant
- Select Grant access
- Select Require multifactor authentication
- Click Select
- Enable policy > Click On
- Select I understand that my account will be impacted by this policy. Proceed anyway.
- Click Create
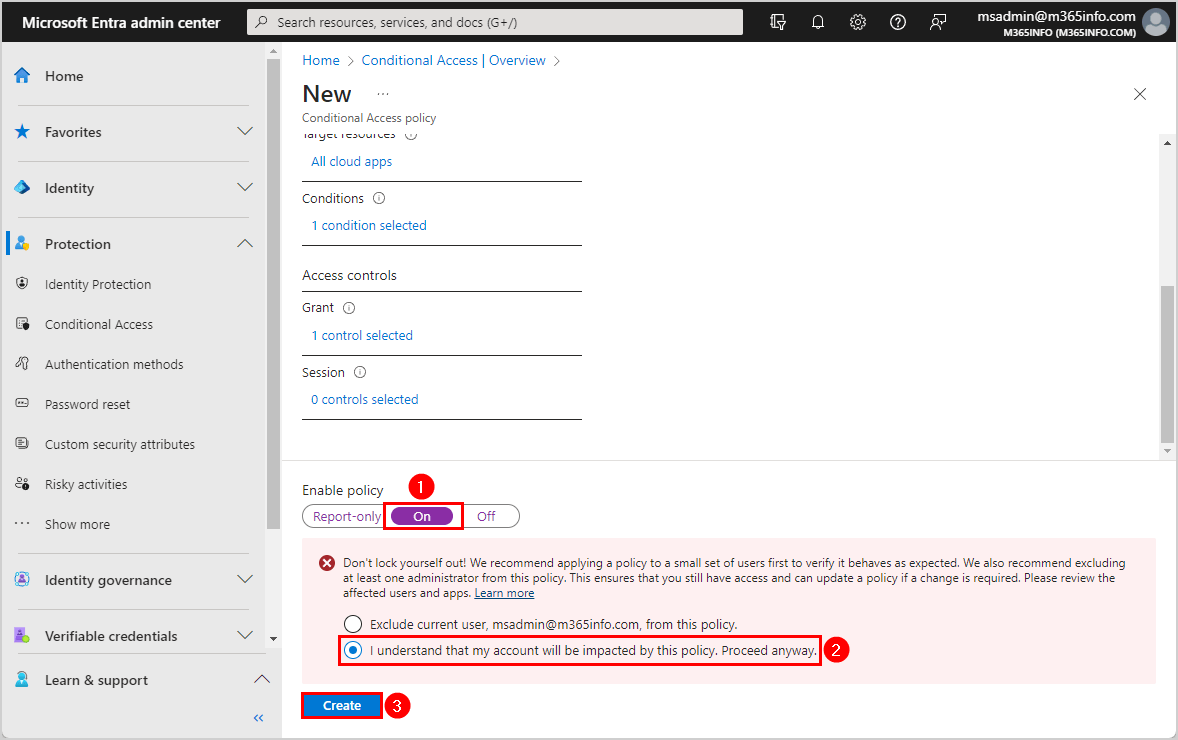
The notification appears that it successfully created the CA policy: MFA all users. The policy will be enabled in a few minutes.
Verify Conditional Access policy in Microsoft Entra
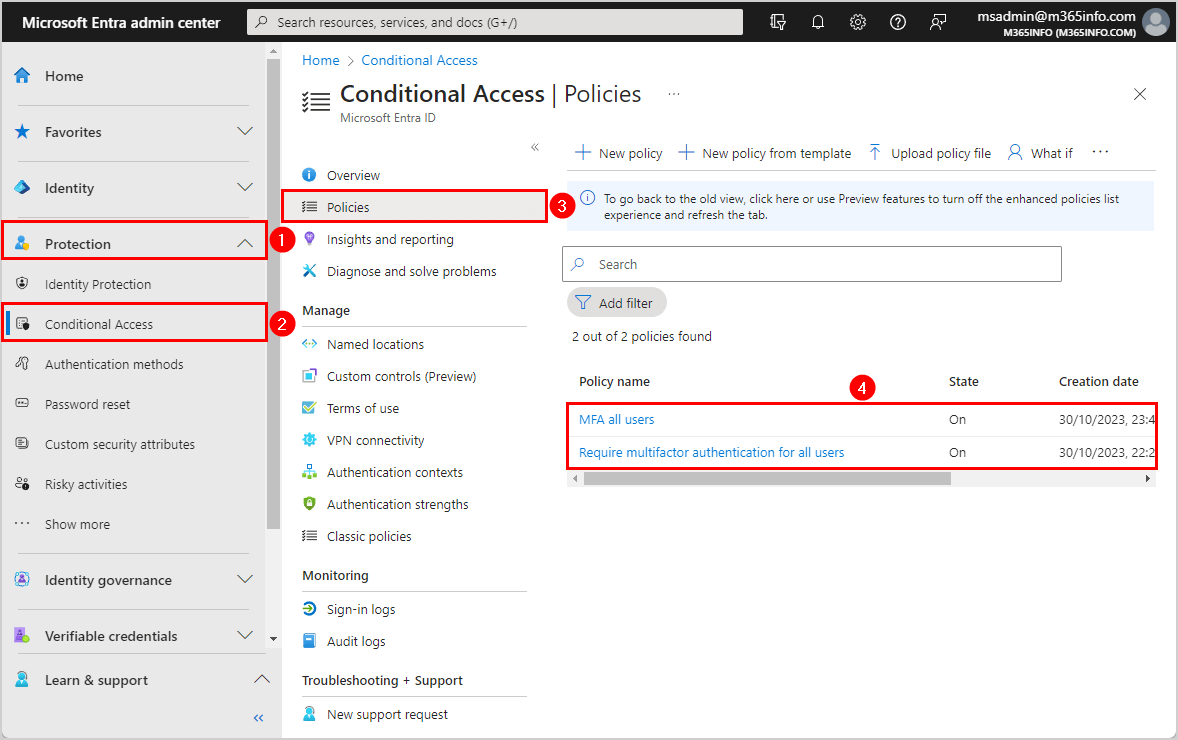
Check the CA policy you created in the Microsoft Entra admin center:
- Click Protection > Conditional Access
- Click Policies
The two policies we created show up in the Conditional Access policies list.
Configure Conditional Access policy with PowerShell
Configure the Conditional Access policy with PowerShell by following the below steps.
Install Microsoft Graph PowerShell
Before you start, you must Install the Microsoft Graph module and Microsoft Graph Beta module.
Run the below commands to install the Microsoft Graph modules.
Install-Module Microsoft.Graph -Force
Install-Module Microsoft.Graph.Beta -AllowClobber -ForceConnect Microsoft Graph PowerShell
You need to Connect to Microsoft Graph PowerShell with the below scopes.
Connect-MgGraph -Scopes "Policy.Read.All", "Policy.ReadWrite.ConditionalAccess"Now, you are all set to use the Microsoft Graph PowerShell commands.
Get list of Conditional Access policy templates
To get a list of the conditional access policy templates, we will use the New-MgBetaIdentityConditionalAccessPolicy PowerShell cmdlet.
Run the below PowerShell command.
Get-MgBetaIdentityConditionalAccessTemplate | select Id, Name, DescriptionThe PowerShell output result is shown below.
Id Name Description
-- ---- -----------
c7503427-338e-4c5e-902d-abe252abfb43 Require multifactor authentication for admins Require multifactor authentication for privileged administrative accounts to reduce risk of compromise. This p…
b8bda7f8-6584-4446-bce9-d871480e53fa Securing security info registration Secure when and how users register for Azure AD multifactor authentication and self-service password reset.
0b2282f9-2862-4178-88b5-d79340b36cb8 Block legacy authentication Block legacy authentication endpoints that can be used to bypass multifactor authentication.
a3d0a415-b068-4326-9251-f9cdf9feeb64 Require multifactor authentication for all users Require multifactor authentication for all user accounts to reduce risk of compromise.
a4072ac0-722b-4991-981b-7f9755daef14 Require multifactor authentication for guest access Require guest users perform multifactor authentication when accessing your company resources.
d8c51a9a-e6b1-454d-86af-554e7872e2c1 Require multifactor authentication for Azure management Require multifactor authentication to protect privileged access to Azure management.
6b619f55-792e-45dc-9711-d83ec9d7ae90 Require multifactor authentication for risky sign-ins Require multifactor authentication if the sign-in risk is detected to be medium or high. (Requires an Azure AD…
634b6de7-c38d-4357-a2c7-3842706eedd7 Require password change for high-risk users Require the user to change their password if the user risk is detected to be high. (Requires an Azure AD Premi…
c26a510a-3b8b-4023-8c44-d4f4c854e9f9 Require compliant or hybrid Azure AD joined device for admins Require privileged administrators to only access resources when using a compliant or hybrid Azure AD joined de…
4e39a309-931e-4cb1-a371-e2beea168002 Block access for unknown or unsupported device platform Users will be blocked from accessing company resources when the device type is unknown or unsupported.
62e51ccc-c9c3-4554-ac70-066172c81007 No persistent browser session Protect user access on unmanaged devices by preventing browser sessions from remaining signed in after the bro…
6acdf4c3-6815-485c-a57d-2c349d517ba0 Require approved client apps or app protection policies To prevent data loss, organizations can restrict access to approved modern auth client apps with Intune app pr…
927c884e-7888-4e81-abc4-bd56ded28985 Require compliant or hybrid Azure AD joined device or multifactor authentication for all users Protect access to company resources by requiring users to use a managed device or perform multifactor authenti…
81fd2072-4876-42b6-8157-c6000693046b Use application enforced restrictions for O365 apps Block or limit access to O365 apps, including SharePoint Online, OneDrive, and Exchange Online content. This p…
76c03f19-ea37-4656-a772-a183b4ddb81d Require phishing-resistant multifactor authentication for admins Require phishing-resistant multifactor authentication for privileged administrative accounts to reduce risk of…
6364131e-bc4a-47c4-a20b-33492d1fff6c Require multifactor authentication for Microsoft admin portals Use this template to protect sign-ins to admin portals if you are unable to use the "Require MFA for admins" t…
16aaa400-bfdf-4756-a420-ad2245d4cde8 Block access for users with Insider Risk (Preview) Configure insider risk as a condition to identify potential risky behavior (Requires an Azure AD premium P2 li… It shows a list of all the Conditional Access policy templates.
Create Conditional Access policy from template
You can create a Conditional Access policy from a template. See the above list of all the templates and choose one of them.
- Type the template Id number in line number 1
- Run the below PowerShell script
$CAtemplate = Get-MgBetaIdentityConditionalAccessTemplate -ConditionalAccessTemplateId "a3d0a415-b068-4326-9251-f9cdf9feeb64"
$policyParams = @{
TemplateId = $CAtemplate.Id
DisplayName = $CAtemplate.Name
State = "enabled"
}
New-MgIdentityConditionalAccessPolicy @policyParamsSee the below PowerShell output result.
Id CreatedDateTime Description DisplayName ModifiedDateTime State TemplateId
-- --------------- ----------- ----------- ---------------- ----- ----------
a09f03f4-235c-4dfc-ab7e-f05b50e8206f 31/10/2023 12.02.42 Require multifactor authentication for all users enabled a3d0a415-b068-4326-9251-f9cdf9feeb64It creates the Conditional Access policy with the template you chose.
Create Conditional Access policy
To create a Conditional Access policy, we will use the New-MgIdentityConditionalAccessPolicy PowerShell cmdlet.
Run the below PowerShell script.
Connect-MgGraph -Scopes "Policy.Read.All", "Policy.ReadWrite.ConditionalAccess"
$params = @{
displayName = "MFA all users"
state = "enabled"
conditions = @{
clientAppTypes = @(
"All"
)
applications = @{
includeApplications = @(
"All"
)
}
users = @{
includeUsers = @(
"All"
)
excludeUsers = @(
"f034e5cd-4abb-47ca-895a-48560ec30787"
)
excludeGroups = @(
"99db26ab-a3c8-4eba-a853-de022efa0021"
)
}
locations = @{
includeLocations = @(
"All"
)
}
}
grantControls = @{
operator = "OR"
builtInControls = @(
"mfa"
)
}
}
New-MgIdentityConditionalAccessPolicy -BodyParameter $paramsIt creates the new Conditional Access policy.
Get all Conditional Access policies
You can get a list of all the Conditional Access policies you created using the Get-MgIdentityConditionalAccessPolicy PowerShell cmdlet.
Run the below PowerShell command.
Get-MgIdentityConditionalAccessPolicy | ftSee the below PowerShell output.
Id CreatedDateTime Description DisplayName ModifiedDateTime State TemplateId
-- --------------- ----------- ----------- ---------------- ----- ----------
5abe02d2-ff3f-4d31-8b20-7e7c58903462 31/10/2023 10.58.08 MFA all users enabled
a09f03f4-235c-4dfc-ab7e-f05b50e8206f 31/10/2023 12.02.42 Require multifactor authentication for all users enabled a3d0a415-b068-4326-9251-f9cdf9feeb64That’s it!
Read more: How to export Conditional Access policy »
Conclusion
You learned how to configure Conditional Access policy for your organization in Microsoft Entra admin center and with PowerShell. First, you need to disable the security defaults for your organization. Then, you can proceed and configure a Conditional Access policy.
Did you enjoy this article? You may also like Export Microsoft 365 users licences. Don’t forget to follow us and share this article.


Is there any script which can be used to get the sign in logs of particular conditional access which is report only.
I do not see any options for that, only option is Log Analytics, but it is subscription based, if there is script it will be very helpful