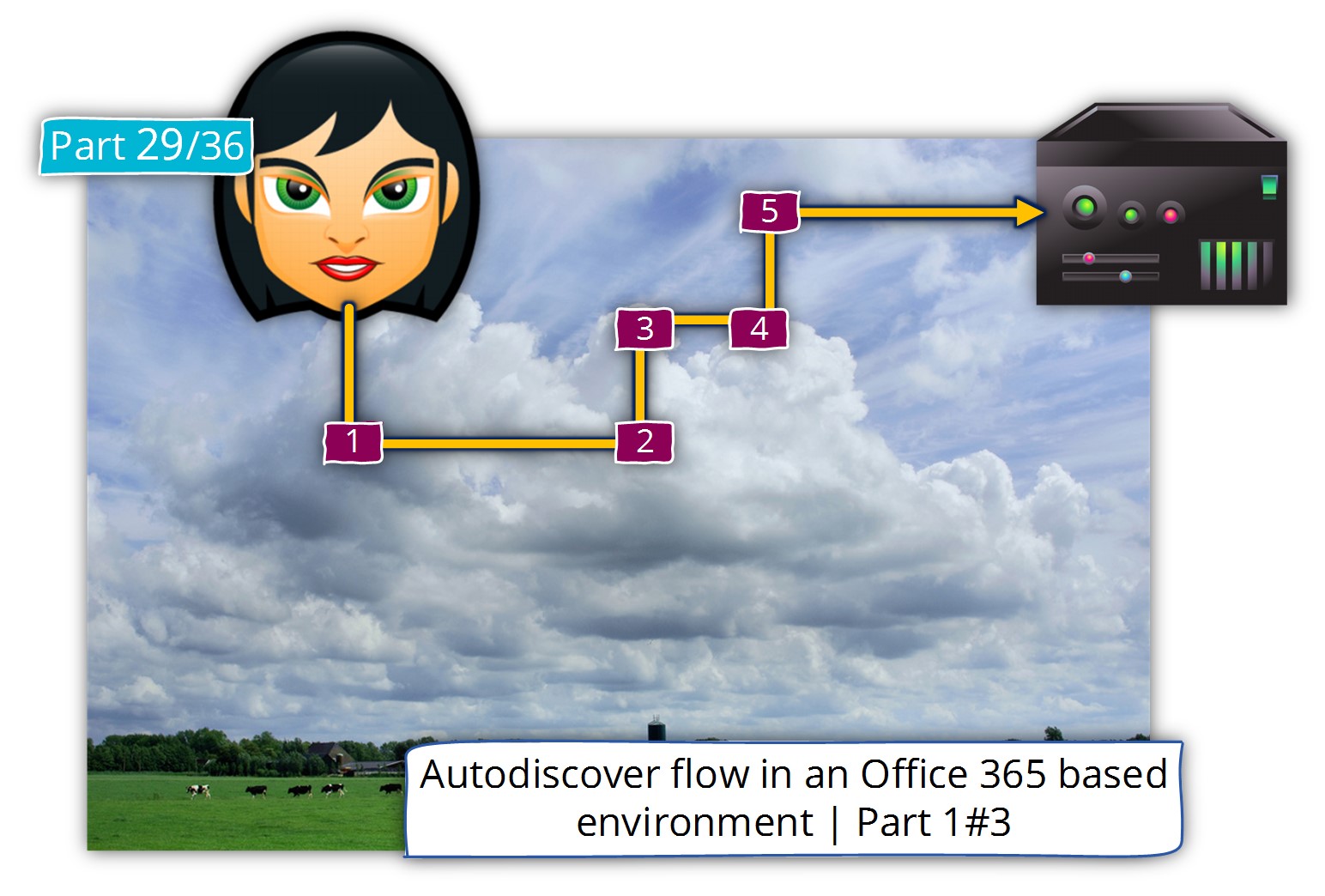
Autodiscover flow in an Exchange on-Premises environment | non-Active Directory environment| Part 3#3 | Part 28#36
The current article is the continuation of the previous article, in which we review the Autodiscover flow implemented in Autodiscover flow in a non-Active Directory environment. In this article, we will inspect the Autodiscover flow using the Microsoft web-based tool,…