Spoof mail attack is implemented by a hostile element the try to spoof sender identity.…
What is so special about Spoof mail attack? |Part 3#9
The unique character of the spoofing attack is – that the “spoof action”, serves as a spearhead for most of the other mail attacks.
In other words – the Spoof mail attack is accompanied by an additional type of mail attacks such as Phishing mail attack or spam mail.
Table of contents
Spoof mail attack, what is good for?
The main purpose of the “spoof phase” is – to cause the destination recipient to trust the sender identity.
The “trust,” is the first building block in the “mail attack building.”
After the hostile element manages to build the bridge of “trust” between him and his victim, there is a high chance that the next step in the attack will complete successfully.
The Spoof E-mail attack does not exist by itself, but instead, serve as the first phase (the trust phase) that leads to the next step, in which the hostile element asks from his victim to “do something.”
For example
Case 1 – E-mail message + malware
The hostile element presents himself as a trustworthy sender and asks from the destination recipient to open the attachment (the malware) in the E-mail message.
Case 2 – Spam mail
The hostile element presents himself as a trustworthy sender and asks from the destination recipient to purchase a specific product or specific service.
Case 3 – Phishing mail attacks
The hostile element presents himself as a trustworthy sender and asks from the destination recipient to “do something” such as – reset his password, access a specific website, deposit money to a particular bank account and so on.
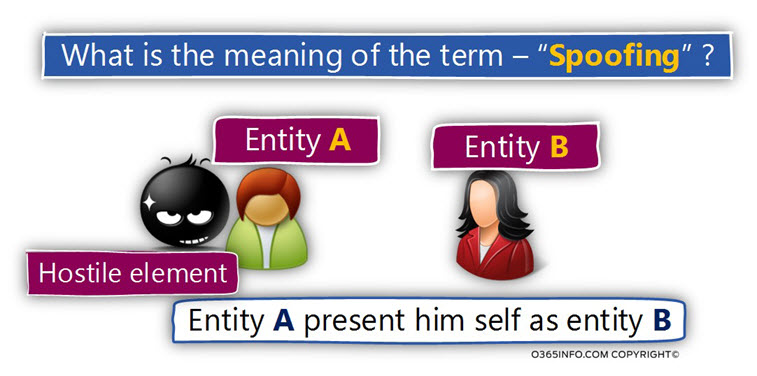
What is the meaning of Spoofing, Spoof E-mail, spoof attack and all the rest?
The simple explanation for the term “spoofing” is, a scenario in which entity A is masking his true identity, and present another identity such as the identity of entity B.
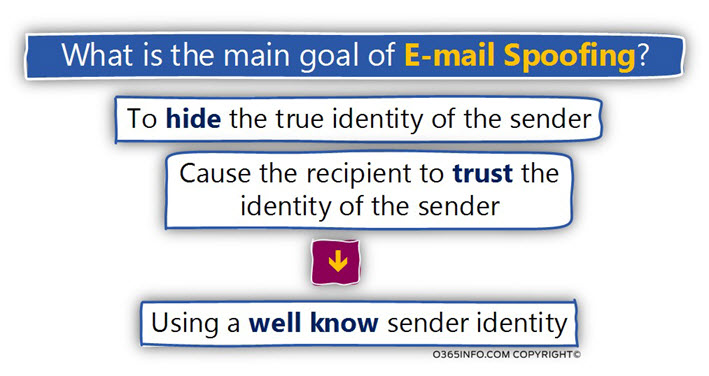
The primary purpose of the element that uses the option of spoofing his identity is to “buy the trust” of his victim by using an identity that the victim can trust.
The “spoofed identity” can be an identity of a sender who “belong” to a well-known organization or in some cases, the attacker provides the identity of a sender whom the destination recipient knows such as someone from his organization.
The purpose of Spoof mail attack
As mentioned, the purpose of the “spoof mechanism” is to serve as the tool by hostel element for – “opening the gate” of the victim fortress.
If the attacker manages to bypass the “trust obstacle,” the attacker executes the rest of the attack steps such as – social engineering, Phishing website, malware and so on.

Exploiting the “victim trust”
The type of identities that can be used by the hostile element.
1. The identity of a sender of a famous or well-known company that has a good reputation.
For example, the identity of a recipient from a well-known company such as PayPal or a leading bank.
2. The identity of a sender of the same organization of the victim.
This is the classic scenario of the CFO and CIO, the scenario of “manager and assists,” the scenario of people from the Helpdesk that address an organization’s user and so on.
In this type of scenario, the attacker abuses the natural tendency of people to trust someone from their organization, and especially if this person (the spoofed identity that used by the attacker) considers as VIP, manager or identity with power or authority.
3. Anonymous identity
Less professional attackers, could use an E-mail account (E-mail message) that created on the major mail, provide such as – Gmail, Hotmail, Yahoo and so on. In this case, the “trust factor” is reduced because the destination recipient is not tempted to believe that the sender is a “known sender.”
A common two misconceptions about Spoof E-mail attack
In this section, I would like to talk about two misconceptions that most of us have regarding the subject of Spoof E-mail attack.
Misconception 1#2 – Spoof E-mail are executed by a professional hacker.
The most common misconception about Spoof E-mail attack is that executing Spoof E-mail attack can be implemented only by a professional or, by a super doper cyber-criminal!
Most of us have an image in our head of a guy with thick glasses, sitting in a dark room full will computer screen, print in rage strange computer language commands, trying to attack our systems.
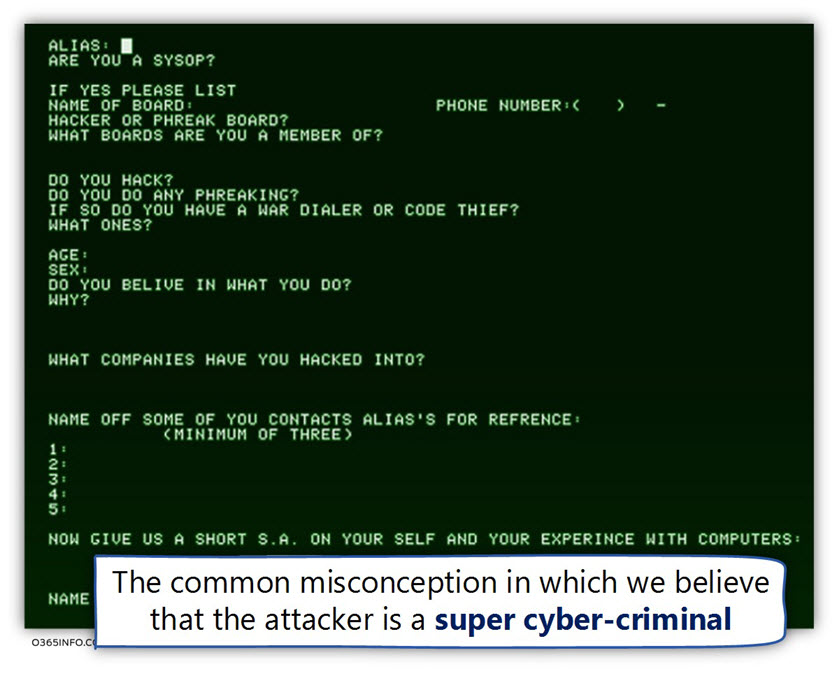
The truth is much simpler, in nowadays, the ability to send anonymous E-mail or to spoof the identity of the sender is very straightforward and easy.
No need to be a super cyber-criminal!
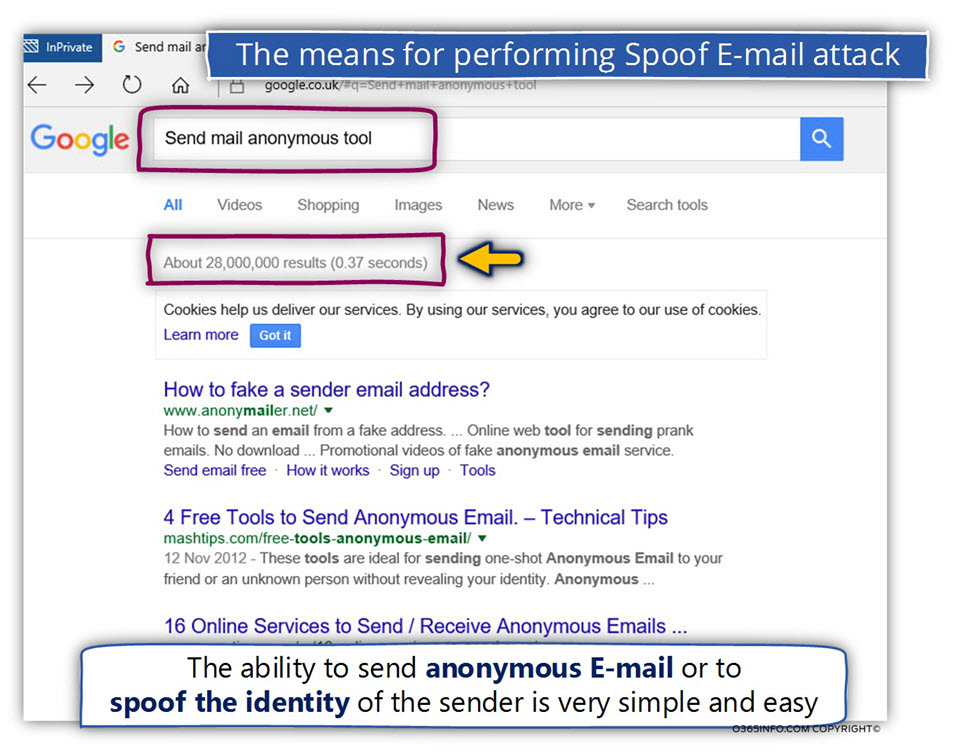
The option of sending Spoof E-mail is very simple, and if we want to make even easier, there are many online web-based tools that can help us to accomplish this task.
In the following screenshot, we can see an example of the search result for the search string “send anonymous mail tool.”
As we can see, there are 28,000,000 results for this specific search term.
You are most welcome to try out yourself and realize, how easy and straightforward is the process is spoofing your E-mail address identity.
If you want to read more information about the way of simulating Spoof E-mail attack, you can read the article – How to Simulate E-mail Spoof Attack |Part 11#12
Misconception 2#2 – my mail server “know” how to identify and block Spoof E-mail.
The simple truth on the assumption in which our mail infrastructure includes a protection mechanism that will protect us from Spoof E-mail attack, most of the time this assumption is wrong!
In other words, most of the existing mail infrastructures don’t deal so not handling well or not handling at all scenarios of Spoof E-mail and Phishing mail attacks.
Spoof E-mail is not a virus and not a spam mail!
Most of the mail infrastructure includes some kind of anti-virus protection and some kind of anti-spam filter, and this protestation mechanism provides not bad protection.
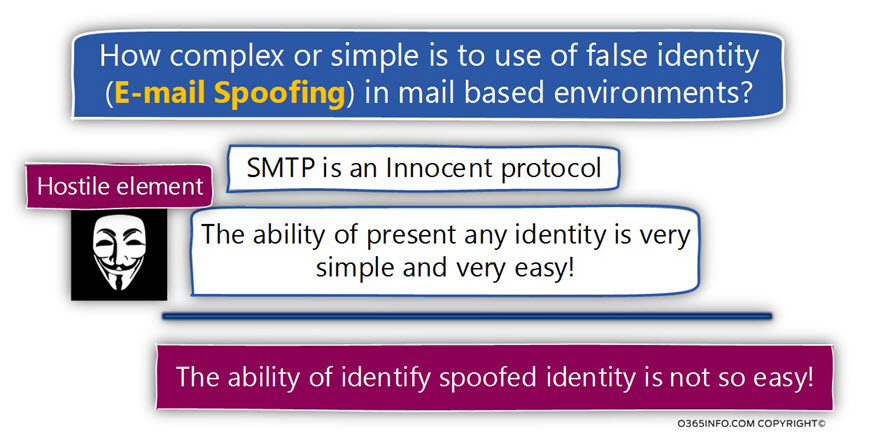
The strange answer to the declaration of the fact that most of the mail infrastructure is not handling well scenarios of Spoof E-mail is because of an Inherent weakness of the SMTP mail protocol.
The SMTP protocol can be described as a “naive protocol” or “innocent protocol” because the SMTP protocol was not created with an awareness of a scenario in which hostile elements will try to spoof their identity.
The primary goal of the people who created the SMTP protocol was to enable the delivery of
E-mail message from point A to point B quickly and efficiently.
The mail server that represents the sender addresses the mail server that represents the destination recipient and asks him to deliver the E-mail message to the particular recipient\s.
Very easy and very straight forward.
The mail server that represents the destination recipient (the receiving mail server) was not configured to suspect or, to doubt the information about the sender identity.
If the senders claim that his identity is X, as long as the E-mail address format is correct, the destination mail server will “believe” the information about the sender identity.
Let’s assume that we have improved the awareness of the target mail server to the fact that some of the senders could be hostile elements.
How can we verify the sender identity, so we will be able to trust him?
The good news that in nowadays, we have a couple of mail sender authentication standards such as SPF, DKIM, and DMARC, that can help is to verify the sender identity.
The less good news is that the implementation of this protocol is not so simple because of many reasons that we will review later in the article – The questions that we will need to answer before we start the project of – building a defense system that will protect us from Spoof mail attacks | Part 7#9
The two major flavors of Spoof E-mail attacks
A paramount subject that I would like to emphasize is that when we use the term – “Spoof E-mail attack,” the term can be translated into two major scenarios:
Scenario 1 – Spoof mail attack that directed towards “other users” (not our users) but the attacker uses our organizational identity when performing the Spoof mail attack.
Scenario 2 – Spoof mail attack in which the attack directed towards our users.
The attacker can use a false sender E-mail address which includes our domain name or use an “external E-mail address” (an E-mail address that includes other domain names that represent other organizations with a good reputation that considers as a trusted organization.
The common association that appears in our mind regarding the Spoof mail attack is related to “scenario 2” in which our users become the victim of Spoof mail attack.
Although this type of attack is more “viable” and more tangible, it’s important to emphasize that the other scenario, in which hostile is Stealing our organizational identity and abuse it by attacking another organization is also a “problematic situation” which could lead to unwanted results that can harm our organization’s reputation.
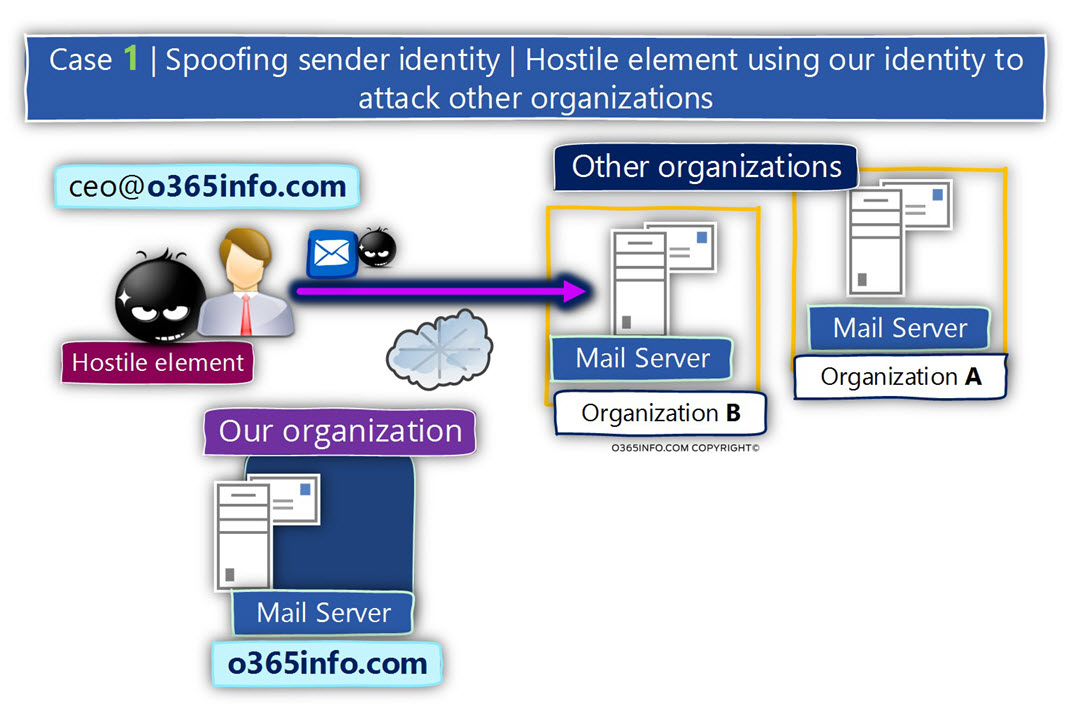
Scenario 1 – Spoof mail attack that is directed towards “other users” (not our users).
A scenario in which the attacker is “stealing” our organization identity.
For example, our organization domain name is – o365info.com
A hostile element, present himself by using a sender E-mail address, that includes our domain name such as – ceo@o365info.com
The reason that the attacker chooses to use our domain is – probably because our organization considered as an organization with a good reputation that can be trusted.
In this case, the primary purpose of the attacker is – persuade the victim (the recipients from the other organization) “believe him” because his identity (his E-mail address that uses our domain name) can be trusted.
In this case, the hostile element is using “our organization good reputation” for abusing recipient from other organizations.
Scenario 2 – Spoof mail attack in which the attack is directed towards our users.
A scenario in which the hostile element attacks our organization recipients by presenting false sender identity.
The false sender identity which the attacker is using can be implemented in two ways:
Scenario 2.1 – the attacker attacks our organization, using a “well know” E-mail address.
In this scenario, the attacker uses a false identity that based on E-mail messages that include a domain name of a company that is well known or, considered as a trusted organization.
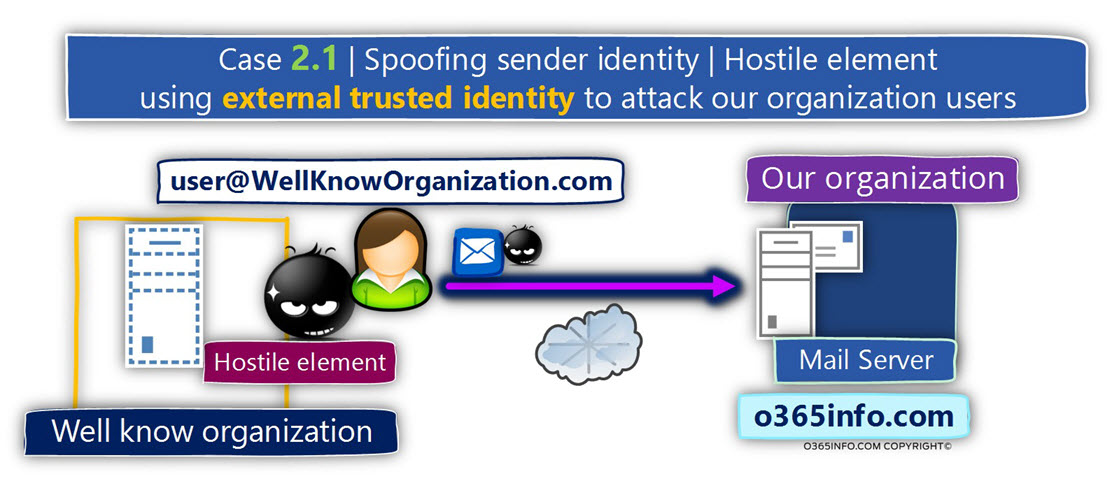
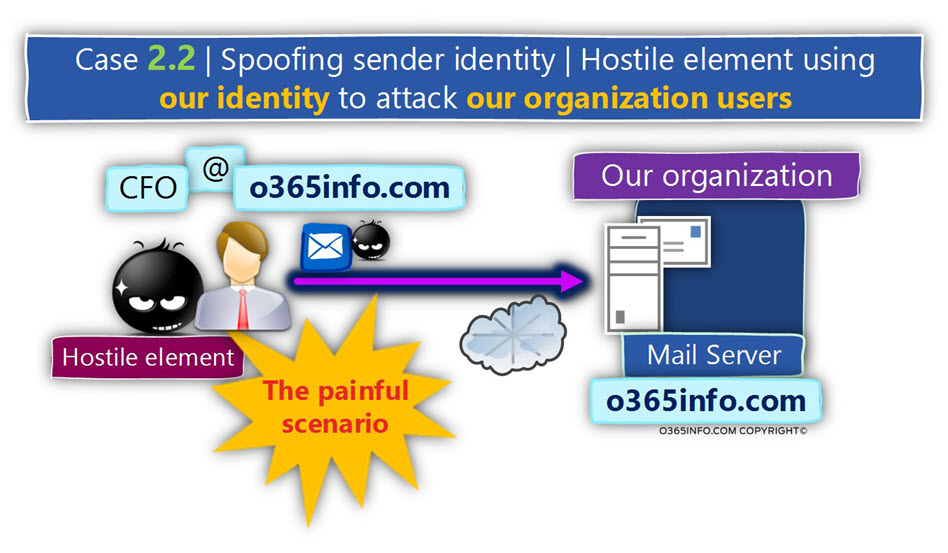
Scenario 2.2 – the attacker attacks our organization, using an E-mail address that includes our domain name.
This type of scenario is the most “painful” situation because, in this case, the attacker Disguises himself using the identity of a person from the same organization as the person that he attacks
(the victim).
An example to such as scenario could be a spear phishing, a particular type of Phishing mail attack, in which the attacker uses an identity of a “well know” person from our organization such as the E-mail address of the company CFO.
The attacker uses this identity for attacking Key People in the organization.
Because the victim sees a familiar sender’s identity, he is easily tempted to trust the “sender E-mail.”
Note: Technically speaking, regarding the scenario in which the Phishing mail attack is pointed toward our organization users, there could be an additional variation on this scenario in which the hostile element does not bother to “cover his real identity” using a “good fake identity” and instead, uses a general identity or public mail provider such as Yahoo, Hotmail, Gmail, etc.
Spoof E-mail attacks | What are the possible damages?
Let’s briefly review the most obvious damages in the case that the attacker manages to execute his Spoof E-mail attack.
As mentioned before, in reality, that hostile element is not satisfied with Spoof E-mail attack because he cannot gain anything by succeeding the complete this type of attack.
The attacker uses the Spoof E-mail attack as an “appetizer” for the “main course.”
The optional damage in case that the hostile element manages to complete the attack (such as Spoof E-mail attacks and Phishing E-mail attacks) is the harm that will realize from the particular attack that executed.
For example – in a scenario of an E-mail that includes malware, the damage that we will experience, depending on the malicious activity that the malware was programmed to do.

Another question that can appear in our mind could be – is this is the only damage that can happen? Is there a possibility of additional and further damages?
The damages of the “attack” could be minor damage but on the other side, can cause tremendous damage.
For example, let’s assume that the attacker executes Phishing E-mail attacks (that include a Spoof E-mail attack) in which he persuaded the company CEO to transfer to his bank account the amount of money worth 500, 000$.$.
What could be the damage of this attack beside the financial loss?
The damage could be a “CEO rage attack,” which can lead to a scenario in which we need to update our CV because we need to look for a new job (the politically-correct term is – looking for a new challenge).

A scenario in which the attacker uses our organizational identity for attacking other victims.
Now, let’s talk about the possible damages in a scenario, in which the hostile element uses our organization identity and attacks another organization.
Let’s assume that the attacker manages to complete the attack, and let’s assume that we don’t care what is the damage caused by another organization.
So what do we care if a hostile element uses our organizational identity?
The answer is that we should care!
The fact that the attack was executed using “our identity” is awful for our reputation.
In many scenarios, the “other organization” that was the victim of the Spoof E-mail attack, will reward us be reporting this information to blacklist providers.
The process in which our domain name registered in the email blacklist is quite simple (because there is real evidence for the fact that our organization “attack” other organizations).
The process of “delist,” in which we recognize that our domain name appears in a well know blacklists, and we ask to remove our name from this “respectable list,” is not so simple and in many cases, could be a long, exhausting process.
Meanwhile, while our domain name appears on a blacklist, the outcome could be that many of the outgoing E-mail messages that sent by organization users to external recipients, will be blocked or rejected by the mail destination infrastructure because our domain name appears as a problematic domain.

The next article in the current article series
What is the meaning of mail Phishing attack in simple words? | Part 4#9



This Post Has 0 Comments