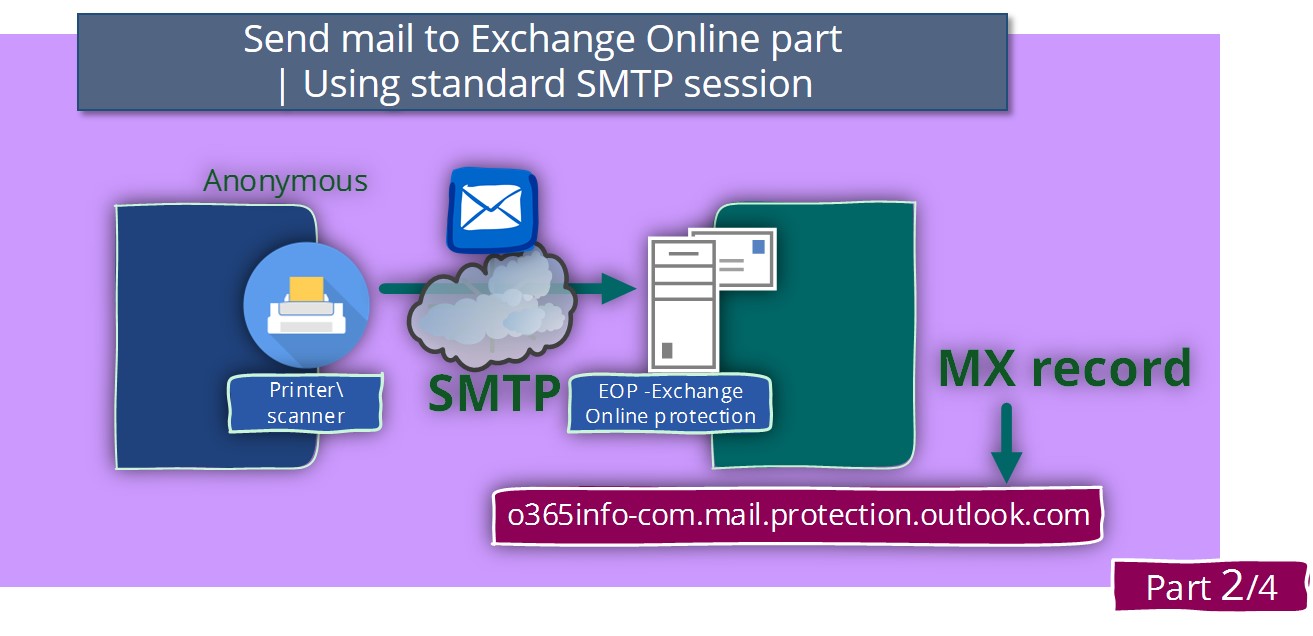
Send mail to Exchange Online using standard SMTP session | Part 2#4
In the current article, we will review the mail flow scenario in which external hosts such as web application or mail-enabled devices to address Exchange Online server by using a standard SMTP session. Send mail to Exchange Online – Article…