The current articles and the next three following articles are dedicated to the subject of…
Internal spam in Office 365 – Introduction | Part 3#17
In the article, we will review:
- What are the possible reasons that could cause to our mail to appear as spam/junk mail?
- Who or what are this “elements”, that can decide that our mail is a spam mail?
- What are the possible “reactions” of the destination mail infrastructure that identify our E-mail as spam/junk mail?
Table of contents
Why is my mail identified as spam?
In a scenario in which our mail is recognized as a spam/junk mail, besides of the unpleasant feeling (nobody wants that the term: “junk” will be associated with him in any way), the major question is: Why is my mail identified as spam?
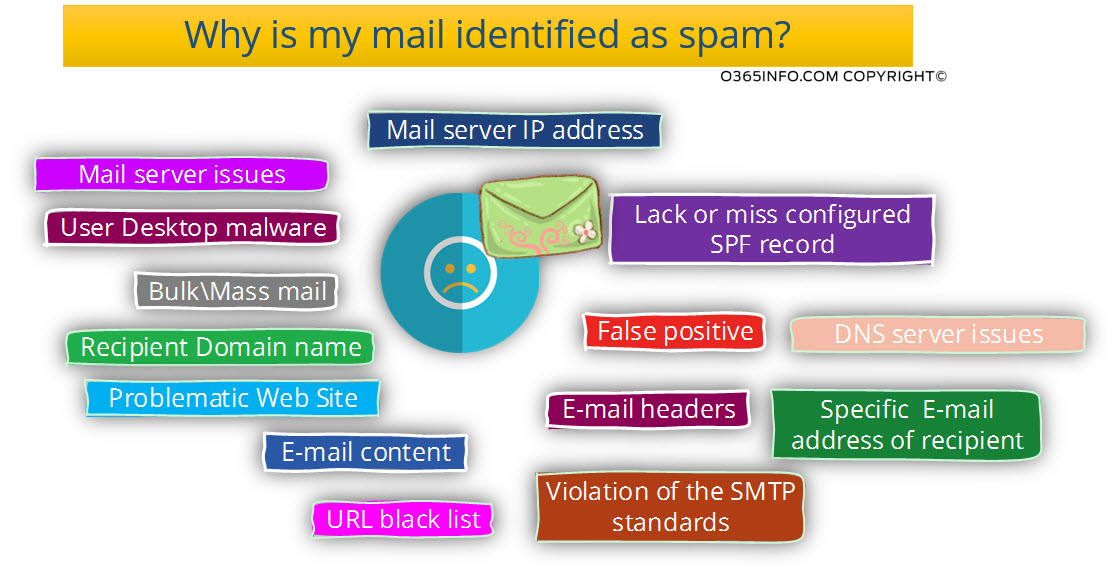
The answer is that there could be many elements and “causes: for this problem and that many times it’s not so easy to “point at” the particular target that is “guilty” for our problem.

Our mission should be:
- Learn to know each of the “elements” could lead us into a scenario in which our E-mail will be recognized as a spam/junk mail by another recipient.
- Ensure that our organization users implement the best practices and, avoid actions that could lead to a scenario in which organization mail will be classified as spam.
- Monitor our organization mail flow looking for a “problematic mail items” or, event that could lead to a scenario in which our mail will be classified as spam.
- In the worst-case scenario in which the event of “organization mail is classified as
“spam/junk mail” implement the required actions to solve this issue.
Who could decide that my mail is a spam mail?
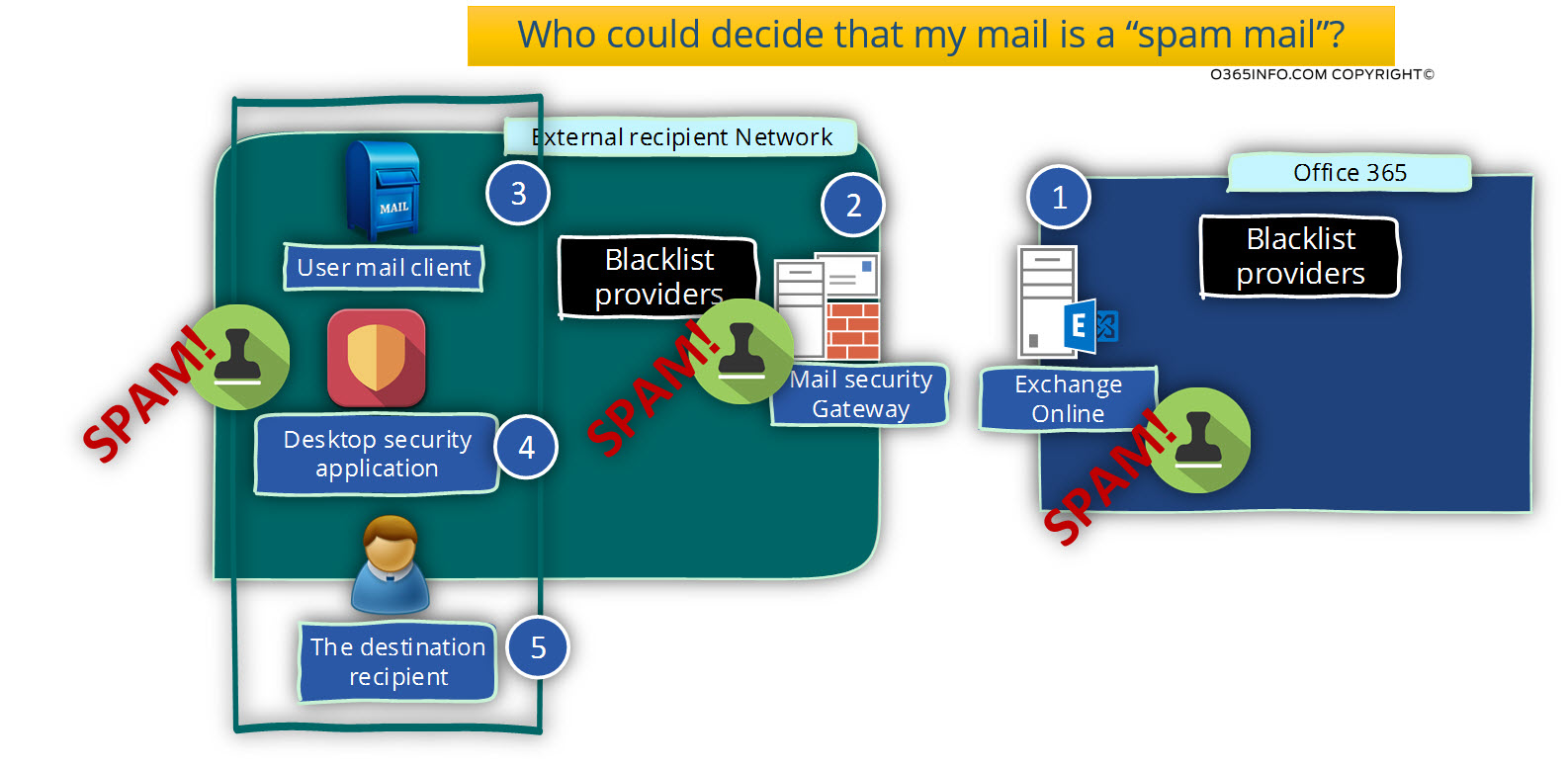
1. Exchange Online
In the Office 365 environment, the first element in the “mail flow” that could identify Office 365 user E-mail message as a spam/junk mail, is the Exchange Online by himself.
If we want to be more accurate, the element the scan the sent E-mail is the component named: Exchange Online Protection.
At first look, this “behavior” look a little strange because most of the time, we are used to a scenario in which the destination mail server can identify our mail as spam/junk mail and not “our mail server.”
The reason for using internal/outbound spam filtering mechanism in Office 365 and Exchange Online environment is the Exchange Online infrastructure is a “shared mail infrastructure”, that serve at the same time many Office 365 customers (tenants) beside of our organization.
Office 365 Infrastructure, is taking extra care to avoid very unwanted scenarios in which, a problematic organization that hosted at Office 365 will “damage” the reputation of other organizations that hosted at the same Office 365/Exchange Online infrastructure.
Exchange Online include a built-in mechanism in which he checks every outbound mail that is sent by Office 365 users to another Office 365 users or external recipient.
In case that Exchange Online “decides” to classify E-mail messages as spam mail, he doesn’t block or delete the E-mail and doesn’t update the SCL value of the E-mail, but instead, route the E-mail to a dedicated Exchange Online mail server named: High Risk Delivery Pool.
We will discuss in more details the subject of- High Risk Delivery Pool in the articles:
- High Risk Delivery Pool and Exchange Online | Part 9#17
- High Risk Delivery Pool and Exchange Online | Part 10#17
2. Destination mail infrastructure | Mail Security Gateway
The “destination mail infrastructure” could be realized as a device that examines each incoming mail and decides whether to pass the E-mail message, block or increase the SCL value.
In a scenario in which we notified that E-mail that sent from organization consider as – a spam/junk mail, the typical case is that our organization appears as blacklisted (registered at some Blacklist provider).
In the modern mail environment, every organization uses some “security mechanism” (mail security gateway or other security solutions) that scan each of the connection requests that sent to the organization’s mail server.
The “requester” (source mail server) is checked and, only if the connection request considers as “legitimate” to “mail session” is approved.
The “verification process” that implemented by the mail security gateway implemented by using different methods. One of the most basic security checks is executed by accessing a database of “blacklist provider”, and verifies that the recipient domain name or the IP address of the mail server doesn’t appear as listed in a blacklist.
3. User mail client
Mail clients such as Outlook, include built-in security engine that can classify incoming mail as a spam/junk mail. For example, we can deal with a scenario, in which E-mail that sent from our users identified as spam/junk mail by the Outlook client and not by the external recipient mail server.
Another option could be a scenario in which the external recipient uses the option of block senders and adds the E-mail address of particular organization users to the list.
4. The destination recipient
The “person” that our mail sent to his mailbox can decide to form some reason to report our E-mail message as a spam/junk mail.
For example, recipient register to your mailing list in the past, forget that he registered and, when he get E-mail from your organization, he relates to the E-mail as spam/junk mail.
5. Desktop security application
Antivirus or other desktop security application can be configured to scan incoming E-mail and decide to classify E-mail messages as spam/junk mail.
What could happen in the case that my mail recognizes as spam/junk mail?
In a scenario in which our E-mail recognizes as spam/junk mail by a destination server, there is considerable importance for the external mail server response.
In case that the external mail server responds by – sending a “reply” in a form of NDR message, which informs us that our mail is blocked because our mail is spam/junk mail, we can be aware of the problem and respond respectively.
In a scenario in which the external mail server decides “not to respond,” technically, we have no way to know that there is some problem with E-mail that sent from our organization.
The only way that we can be aware of the problem is – in a scenario in which the external mail server “forward” the E-mail message to the destination recipient and because the email server increases the SCL value, the E-mail sent to the junk mail folder.
Only if the “target recipient” find the E-mail in the junk mail folder and, only if he is “kind enough” to inform us, only then, we can know that we have a problem with mail that sent from our organization.
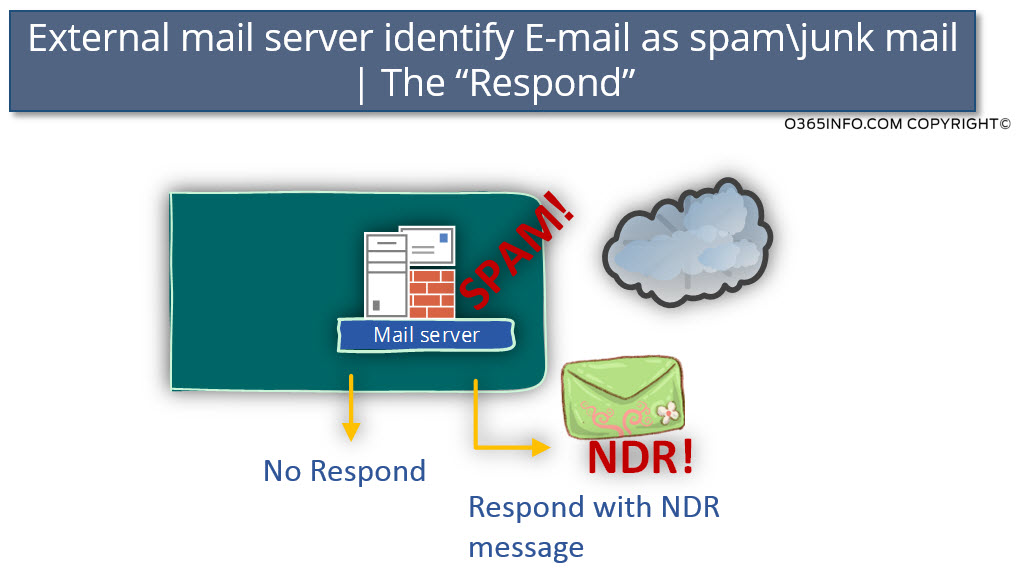
When our E-mail is accepted by an external mail server and, the external mail server identifies our mail as “spam/junk mail,” the external mail server could implement one of the following options:
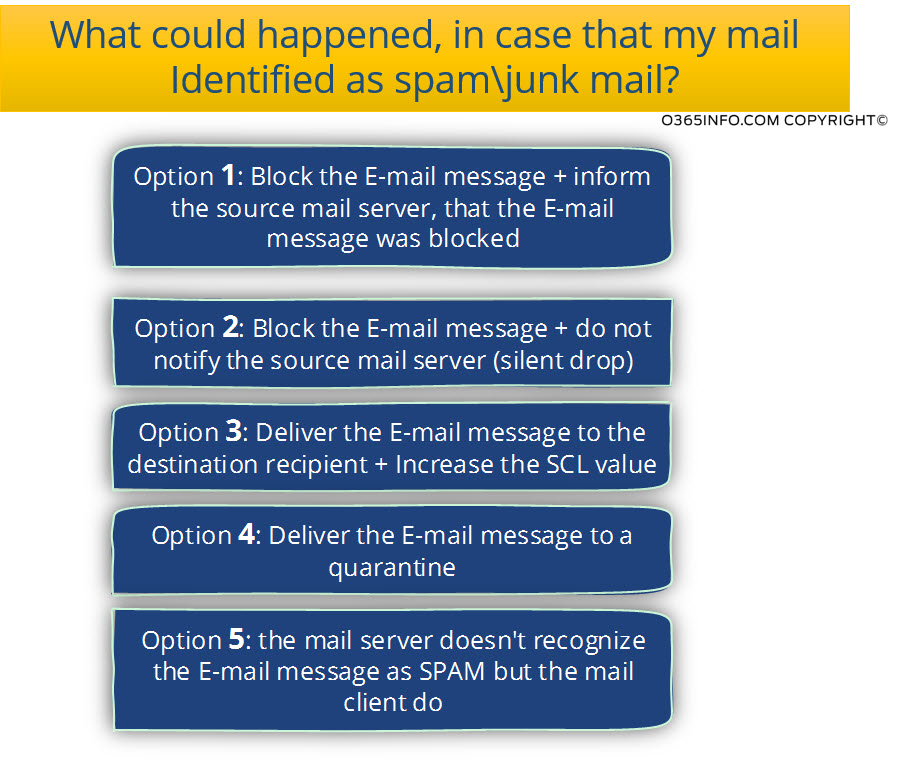
Option 1: Block the E-mail message + inform the source mail server that the E-mail blocked.
This scenario makes our life easier. Is truth that the Office 365 recipients E-mail didn’t get to his destination but, we have a “clear indication” for the failure of the mail delivery.
Now, our mission will be: to find what was the reason for classifying our E-mail message as spam/junk mail.
Option 2: Block the E-mail message + do not notify the source mail server (silent drop)
A scenario in which the “destination mail server” ranks the E-mail as spam/junk mail and, just deletes the E-mail without sending any notification or update to the “source” that sends the E-mail.

Option 3: Deliver the E-mail message to the destination recipient + Increase the SCL value
This type of scenario is the “standard” or the default behavior in Exchange Online environment.
In case that the E-mail recognized as a spam mail, and the “spam level” is “reasonable,” Exchange Online will not block or delete the spam mail. Instead, Exchange Online “stamp” the E-mail with a high value of SCL (spam confidence level) and, deliver the E-mail to the destination recipient.
The destination recipient” will have to decide “what to do with the E-mail message.”
In this scenario, the E-mail will get to the user “Junk mail folder”, and most of the time; users do not tend to look at the junk mail folder.
In this scenario, the “destination recipient” will usually reports, that he didn’t get the E-mail message, but the E-mail is “hidden” in his Junk Mail folder.
Option 4: Deliver the E-mail message to a quarantine queue
A scenario that is similar to the previous situation. The difference is that the Mail server delivers the E-mail message that identified as spam to an individual store named: quarantine.
Option 5: The mail server doesn’t recognize the E-mail message as spam but, the mail client does.
Many mail clients such as Outlook, considers as a sophisticated mail client and has built-in options for recognizing spam mail, create a block sender list, etc.
In this scenario, there is a chance that the mail client will decide that a specific E-mail message can be considered as – a spam E-mail message.
Exchange Online and SCL
In the current article series, we will mention from time to time the term: SCL
Q: What is the meaning of SCL?
A: The term SCL, stand for Spam Confidence Level
In simple words, the SCL is a value that is “attached” to the mail server (usually Exchange server) to E-mail item and define the “trust level” of the E-mail item from the perspective of – spam.
An SCL value such as: “-1” is “saying” that the E-mail item can be fully trusted and a high SCL value such as – 5, “say” that the E-mail item considers as spam mail.

This Post Has 0 Comments