The Exchange Online provides a rich set of tools and options for: “Dealing with SPAM.”…
Office 365 spam mail report using PowerShell | Introduction | 1#3
The current article is the first article in a three-article series. The Purpose of this article series is to Show you a relatively new PowerShell cmdlet named – Get-MailDetailSpamReport, that was created for Exchange Online and Office 365 administrator that need to view and export information stored in Exchange Online spam mail log file.
Table of contents
Article series | Using Get-MailDetailSpamReport | View and export spam mail report
- Office 365 spam mail report using PowerShell | Introduction (this article)
- Using Get-MailDetailSpamReport PowerShell cmdlet | View and export spam mail report
- How to use the spam mail report PowerShell script
The syntax of the Get-MailDetailSpamReport PowerShell cmdlet is quite simple. In the next article, we review some basic example syntax example of the Get-MailDetailSpamReport PowerShell cmdlet and in addition we also review more advanced PowerShell syntax that will help us to “squeeze more juice” from the Get-MailDetailSpamReport PowerShell cmdlet
The real challenges of using the Office 365 spam mail report
Associatively the task of reading spam mail reports looks like and easy and simple task for the average Exchange Online administrator.
My arguments are that:
- Although the term “spam mail” like quite an obvious term, in Office 365 and Exchange Online based environment this term is not so obvious because the term “spam mail” can relate to many different types of “problematic emails” (Spoofing or Phishing mail, bulk mail and more).
- Analyzing the data in the spam mail report
Given that we can get the Office 365 spam mail report via the web admin interface or by using PowerShell command. The real question is – what do we do with this information?
And again, although it looks like a simple task, in reality, the conclusions we can draw the “raw data” are not so clear.
The little secret that is not known for most of us is that the “data” in the spam mail report can be very interesting and useful data that can help is to identify security risks that are “hidden” in the “spam mail report data”.
For example, by viewing the information in the spam mail report we can Identify in advance and prevent “events such as –
- Identify event in which hostile element try to spoof the E-mail address of our legitimate organization user\s.
- Identify event in which an organization user account was comprised and it used by hostile element for distributing spam mail.
- Identify event in which a legitimate granitization user is implemented Improper use of mail and for this reason his mail stamped as “spam mail”.
General review of spam mail concepts in Office 365 (Exchange Online)
Before we begin with the technical description of the how to use the Get-MailDetailSpamReport PowerShell cmdlet, it is important that we get familiar with the basic concept of the term: “spam mail” in “Microsoft based environment” and especially, in Office 365 (Exchange Online) based environment.
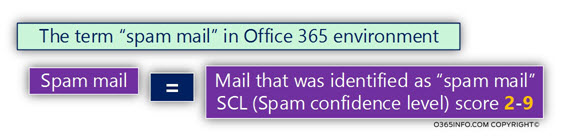
Spam mail and SCL score
The basic technical definition of the term – “spam mail” in the Exchange Online environment is mail item, which his SCL score is a value between 2 and 9.
This leads us to the next question – what is SCL?
The term SCL stands for – Spam Confidence Level.
SCL is a method, which is used in an Exchange server environment to define the “trust level” of specific mail items.
An SCL value of “-1,” defines a mail item that is fully trusted. The higher the SCL score/value, the meaning is that the specific mail item is less trusted.
In other words, the higher the SCL score/value, the more likely it is to assume that the E-mail message is definitely “bad mail” (spam mail).
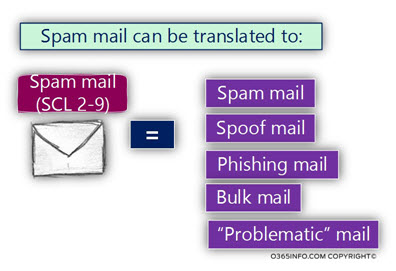
What is the meaning of spam mail?
The term “spam mail” is quite vague because, in real life, the meaning of this term can be realities to – spam mail (as the name imply) but at the same time, to another type of “problematic mail” such as – spoof mail, Phishing mail, Bulk mail and more.
Bottom line – in Exchange Online and Office 365 environment, we should understand that spam mail can be related to many types of “unwanted” mail items.
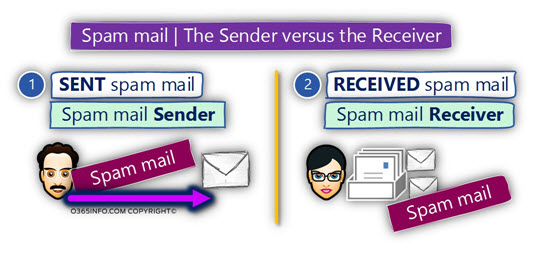
Spam mail | The Sender vs. the Receiver
Another classification of “spam mail” that we should know is the definition of “Sender” vs. the “Receiver” of the spam mail.
- Spam mail Sender – this is the entity that is responsible for “distributing” the spam mail.
- Spam mail Receiver – this is the entity that “suffer” from the spam mail.
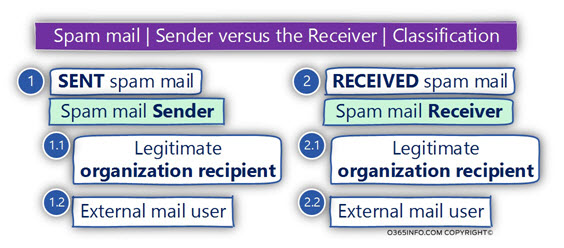
Apparently, the definition of “spam mail sender“ vs. “spam mail Receiver,” look quite obvious.
But in reality, things can get a little complicated because this classification of “bad guy” vs. “good guy” is not always so clear.
For example, the “spam mail sender“ can be a “bad guy” (external user), which bothers some of our organization’s users (Exchange recipients), but at the same time, the “spam mail sender” can be a legitimate organization recipient.
The same logic can be implemented regarding the “entity” that gets (receive) the spam mail.
It is true that most of the times, the recipients who get the spam mail are, our organization recipients, but in some scenario in which – organization user is sending spam mail, the recipient who “suffer” from the spam mail could be external recipients (non-organization recipients).
Spam mail events vs. what happened to spam mail
In this part, I would like to emphasize the difference between the concept of the “information about spam mail events” vs. what the mail infrastructure (Exchange Online in our scenario) is “doing” with the spam mail.
Each mail that is sent or received by EOP (Exchange Online Protection), and “stamped” as spam mail, will appear on the spam mail report. In other words, the documentation of the “spam mail events” is written to Log file.
The “action” taken on mail that is identified as – “spam mail,” is implemented by a different mechanism, such as – the Exchange Online spam policy filter or Exchange Online Transport rules.
In other words, the information that appears in the spam mail report doesn’t include information about “what happened” to the spam mail.
Instead, the information in the spam mail log, include a documentation about “spam mail event” meaning, an event in which a specific E-mail message is “stamped” as a spam mail.

What is our mail focus when analyzing the spam mail report?
Assuming that we already get the “spam mail report.” The questions that can appear now are:
Q1: What can I do with this information?
Q2: Can I benefit from the information that appears in the spam mail report?
Q3: Should I need to generate different spam mail reports, that emphasizes different spam mail events aspects?
Q4: What should be my mail focus – the sender of the spam mail, the receiver of the spam mail?
Q5: Should I look for specific events that relate to my organization recipient or should I put my main focus on “external entities” that try to attack my organization users?
The answer is, that there is no one “right answer.” Our main challenge is to take the “dry data,” and see what’s hiding behind is the “boring numbers.”
When I wrote the current spam mail reports PowerShell script, my aim was to simplify the process. The PowerShell script will give you the option to export spam mail reports, that “light” different aspects of the event that we should observe, and analyze for the purpose “reacting” with the needed security and administrative steps.
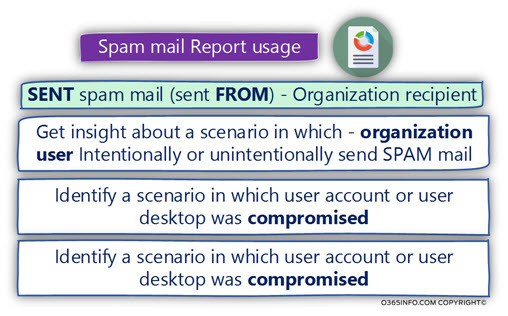
Spam mail report usage
In the following section, I would like to give you a couple of examples of “security event’s scenarios,” that we can “fetch,” by looking over the data stored in the spam mail reports.
Spam mail sender
When we decide to focus on the “spam mail sender,” in some scenario, we can identify events in which the “spam sender” entity, appears to be the entity of a legitimate organization user (an E-mail address of organization user or E-mail address that has our domain name suffix).
Despite the underlying premise that our organization users are the “good guys,” in reality, we can reveal scenarios, in which one of our organization recipients (deliberately or on purpose), is involved in sending mail that is recognized as “spam mail” (in the Exchange Online environment these phenomena described as – internal spam).
Another possible explanation to such a scenario could be – a scenario in which the organization user account was comprised, and now it is used by hostile elements for distributing spam mail.
An additional optional scenario could be, a hostile element that tries to “present himself” as a legitimate organization user, by spoofing the E-mail address (the identity) of a specific organization user.
Spam mail receiver
When we decide to focus on the element that “gets the spam mail” (most of the time our organization users), we should look at the “spam mail report data,” and try to understand if we can locate specific “trends” hidden within the row data.
For example, locate a trend in which specific “attacker” (specific E-mail address or specific E-mail address with a specific domain name suffix), is trying to attack our organization users.
In other words, is there a specific Identifiable “element” that targets our users?
Another scenario could be a hostile element that uses many types of E-mail addresses, but when we take a closer look at the data, we can see that he tries to attack specific organization users (such as scenarios of – spear phishing).
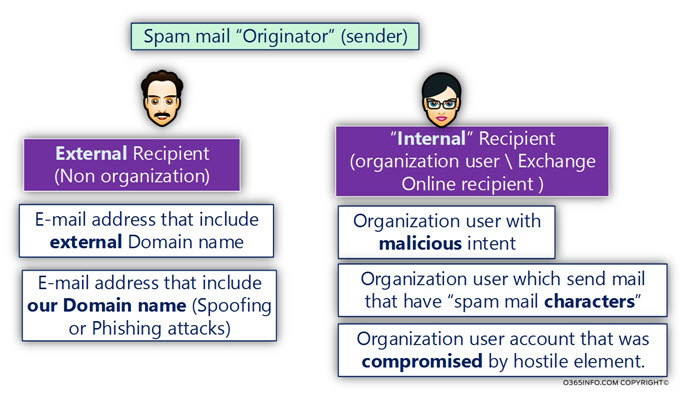
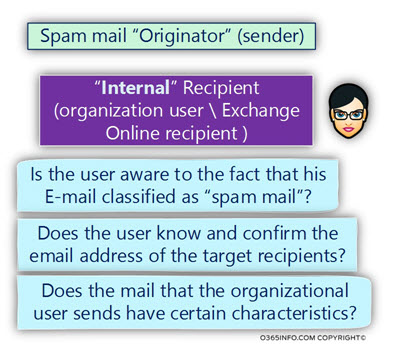
Spam mail “Originator” (sender)
In this section, I would like to view in more details the subject of “spam mail sender.”
As mentioned, the term “spam mail sender” is associatively associated with “bad guy” that plotting evil, and trying to hurt our Innocent organization user but the reality is more complex.
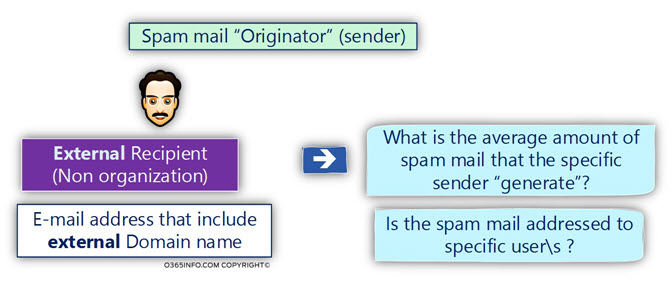
Spam mail sender | External entity
The “spam mail sender” can be indeed, “external entity” that uses non-organization identity meaning – external E-mail address.
At the same time, this “external entity” could try to appear as a – legitimate organization user, by using the identity of a specific existing organization user (existing organization E-mail address) or by using an E-mail address that includes our organization domain name (our organization domain name suffix).
Notice that the “spam mail report” can not help you to identify “spoofed E-mail address,” but only “point” on a specific events, in which a specific organizational identity (organization E-mail address) is involved in spam mail activity.
When we identify such as scenario, in which a specific external recipient is involved in sending a lot of spam emails to our organization users, we should review the information and try to answer such as:
- What is the average amount of spam mail that the specific sender “generate”?
- Is the spam mail addressed to a specific user\s?
Spam mail sender | Legitimate organization user
In this scenario, the “spam mail originator,” is indeed legitimate organization user.
There could be many reasons for such a scenario. For example:
Scenario 1 – Bulk mail
Organization user who sends E-mail to hundreds or thousands of recipients, and “stamped” by EOP as “bulk mail” (translated into an email message that has an SCL value of 2-9).
Scenario 2 – Compromised E-mail client.
A scenario in which malware is using existing mail client such as – Outlook, for distributing spam mail.
Scenario 3 – Compromised Office 365 user account
A scenario in which hostile element, manage to get the credentials of a legitimate Office 365 user, and use these credentials for sending spam mail.
In a scenario in which the spam mail sender appears as one of our organization users, the questions that we can ask could be:
- Is the user aware of the fact that his E-mail classified as “spam mail”?
- Does the user know and confirm the email address of the target recipients?
- Does the mail that the organizational user sends have certain characteristics?
In the next article, we will look into Using Get-MailDetailSpamReport PowerShell cmdlet | View and export spam mail report.

Where is the download link for the scripts ???
Thank you very much for this very relevant article. Please send me the download link.
Regards
Hi,
Can’t find the download link for the powershell. Can you provide?
Thanks
Hi
left a notice on the download page (technet) but leave it here too.
What i can see when running the script, it doesnt count quarantine mail as spam so that user/users that got mail in quarantine non released during the timeframe specified in script doesnt get included in the report created by the script.
is that by design or something missing?
Regards
Conny
Hello Conny,
Regarding your question:
The simplest approach to the Office 365 spam mail report can be described as – WYSIWYG (what you see is what you get).
The meaning is that the PowerShell cmdlets – Get-MailDetailSpamReport, supposed to “dump” the information stored in the Exchange Online spam mail report log file.
You (as Exchange Online administrator), can manipulate the “data” (such as the information stored in the CSV file) by – filtering the data, sorting specific columns, looking for a specific value, and so on.
As far as I know, there is no special reference to spam mail that was sent to quarantine.
The spam mail report just “report” about incoming and outgoing mail items, that was “stamped” as spam mail.
In other words, the spam mail report doesn’t “know” what happened to the spam mail (rejected, quarantined, deleted, etc.) but instead, just know that the specific mail items were classified as spam mail.