Each time a Microsoft 365 user opens or composes an email in Outlook on the…
Configure Exchange Online to accept SMTP connection only from specific mail security gateway
You need to change the default Exchange Online incoming mail flow when your organization adds a mail security gateway (third-party service). In this article, you will learn how to configure Exchange Online inbound mail flow to accept SMTP connection only from a specific mail security gateway IP address.
Table of contents
Exchange Online default incoming mail flow
When your organization’s mail infrastructure uses Exchange Online, Microsoft 365 automatically creates an MX record that manages all incoming mail. All incoming emails for that domain are routed to Microsoft’s Exchange Online servers for filtering and processing before being delivered to the organization’s Microsoft 365 mailboxes.
By default, you add the MX record of your organization’s domain name to your public DNS, so it points to Exchange Online Protection (EOP).
The below picture shows the procedure when a person sends mail to your Exchange Online mailbox. The Exchange Online Protection (EOP) will filter the email message before delivering the message to your Exchange Online mailbox.
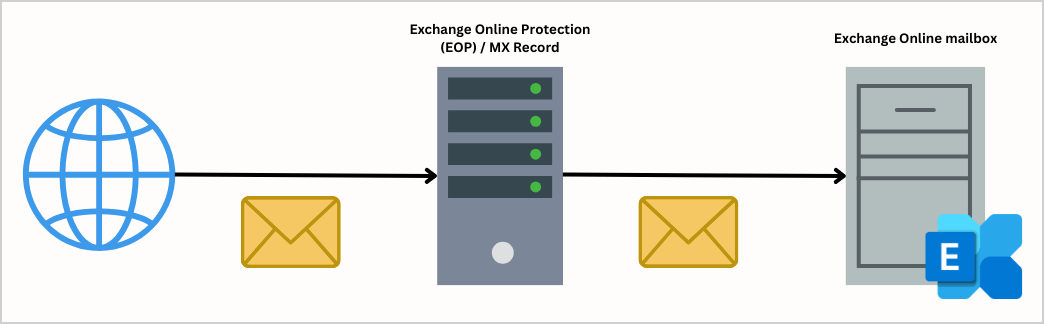
Exchange Online incoming mail flow using third-party cloud service
Let’s say we want to use another mail security gateway, like a third-party filter service for our organization. This means that all incoming mail to our organization must first go through the spam filter before being routed to the Exchange Online mailbox.
In our example, we want every email sent to our organization recipient to first go to the mail security gateway (third-party filter). The mail security gateway implements several security checks. After the security check is completed, the mail security gateway will forward the emails to the Exchange Online mail server.
Note: Some external hosts, like spammers, know the IP address of the Exchange Online mail server or the Microsoft 365 MX record of our hosted domain. These external hosts can bypass our mail security gateway by creating an SMTP session with Exchange Online directly.
To prevent external hosts from addressing your Exchange Online mail server directly, you need to implement a mail flow configuration. The solution is to lock down your Exchange Online organization to accept mail only from your third-party filter service.
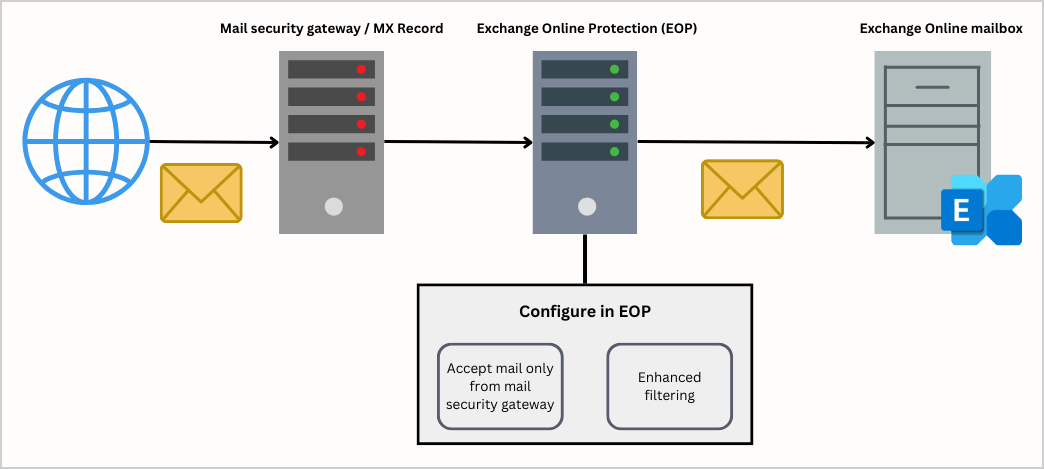
Now that you have a clear understanding of how Exchange Online works with a third-party hygiene solution provider, let’s look at how to configure it in Exchange Online.
Create new Exchange Online incoming mail connector
We want to make a strict Exchange Online incoming mail policy. Therefore, you need to create a new customized Exchange Online incoming mail connector.
Time needed: 10 minutes
How to create an incoming mail connector:
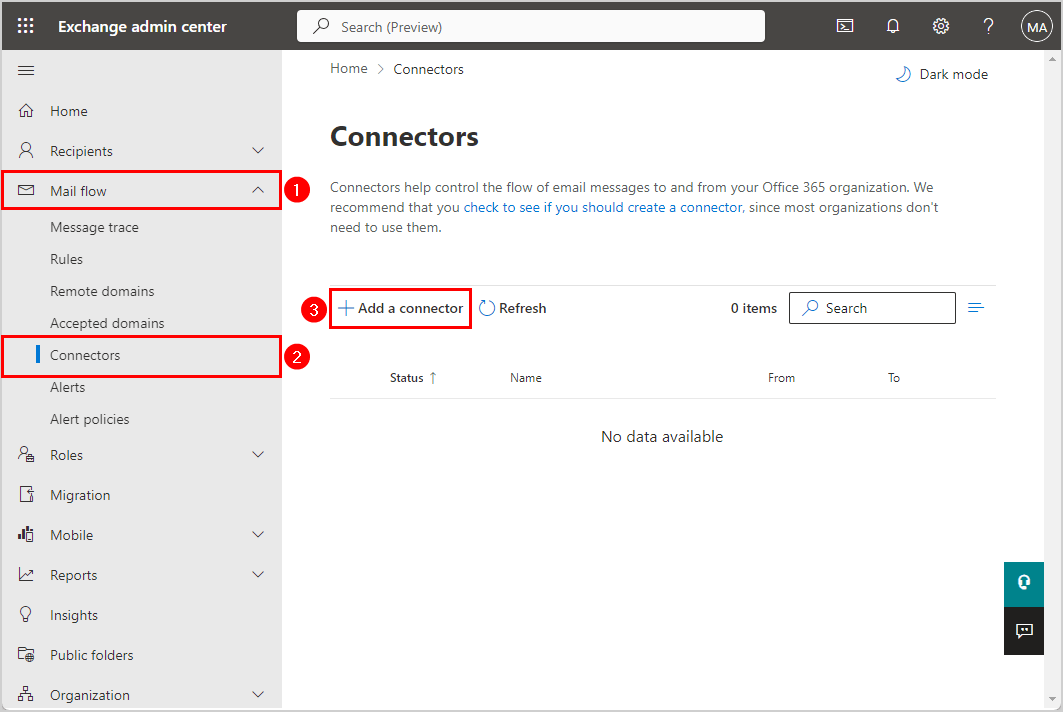
- Go to Exchange admin center.
Sign in with your admin credentials
- Add connector.
Click Mail flow > Connectors
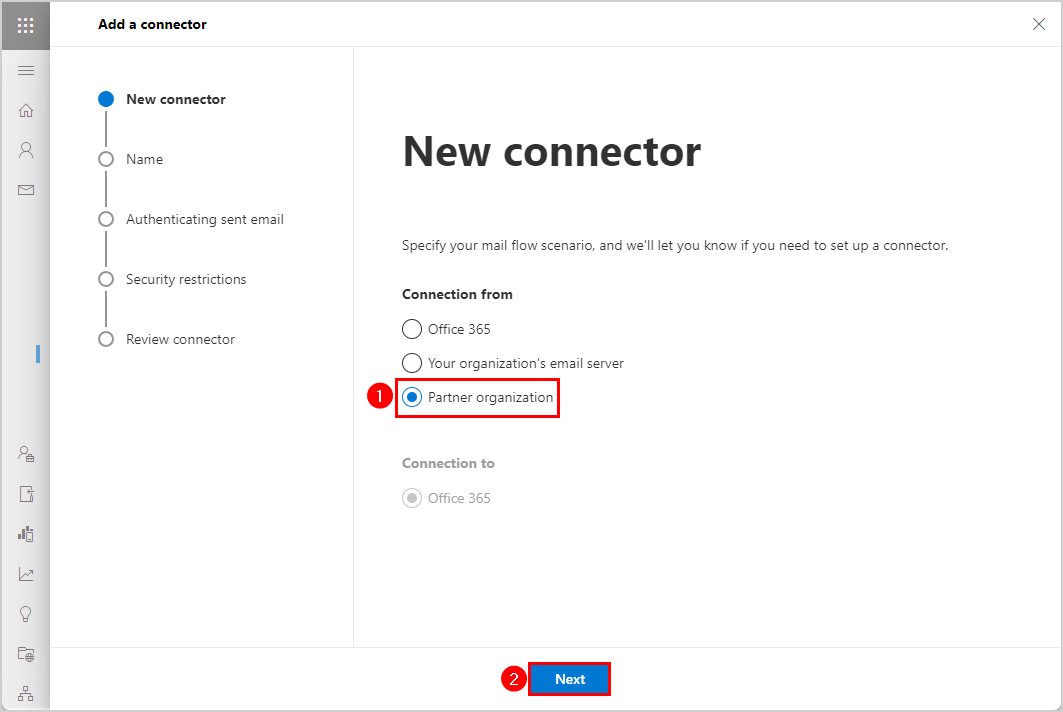
Click Add a connector - New connector.
Select Partner organization
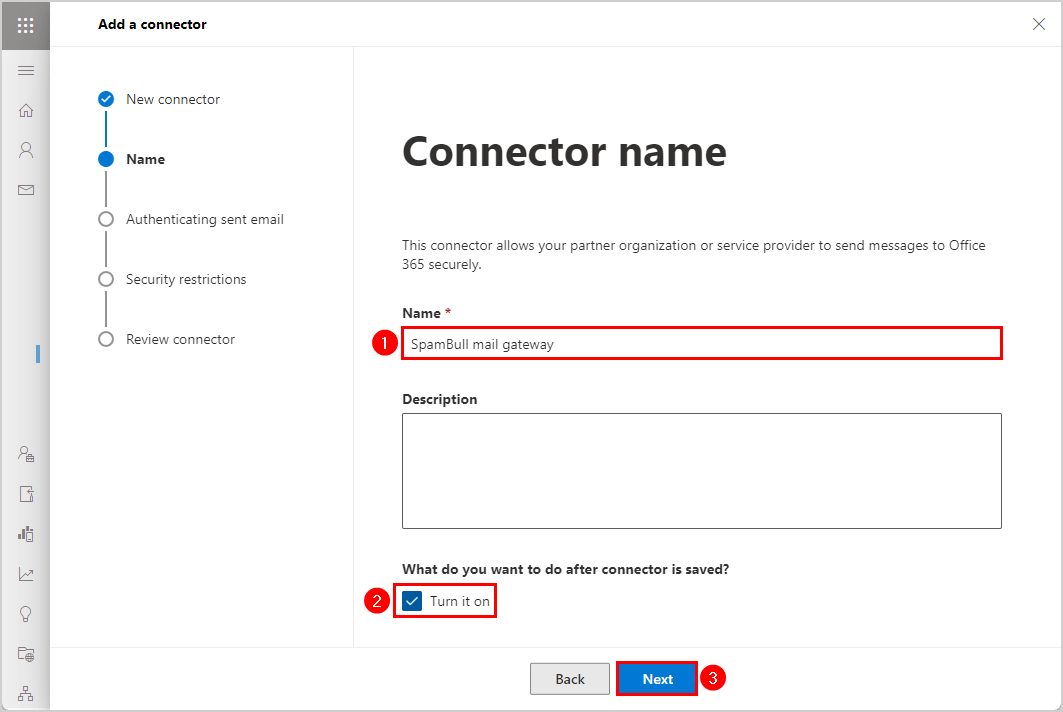
Click Next - Connector name.
Type the Name (Third-party filter service)
Select Turn it on
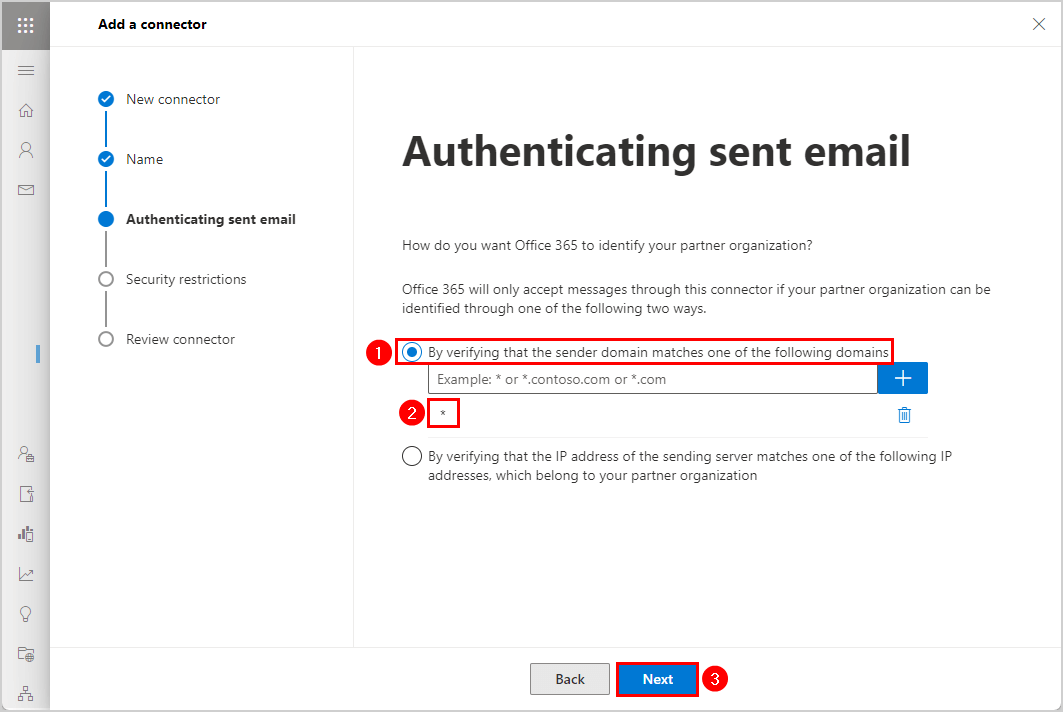
Click Next - Authenticating sent email.
Select By verifying that the sender domain matches one of the following domains
Type * (asterisk), meaning every sender domain
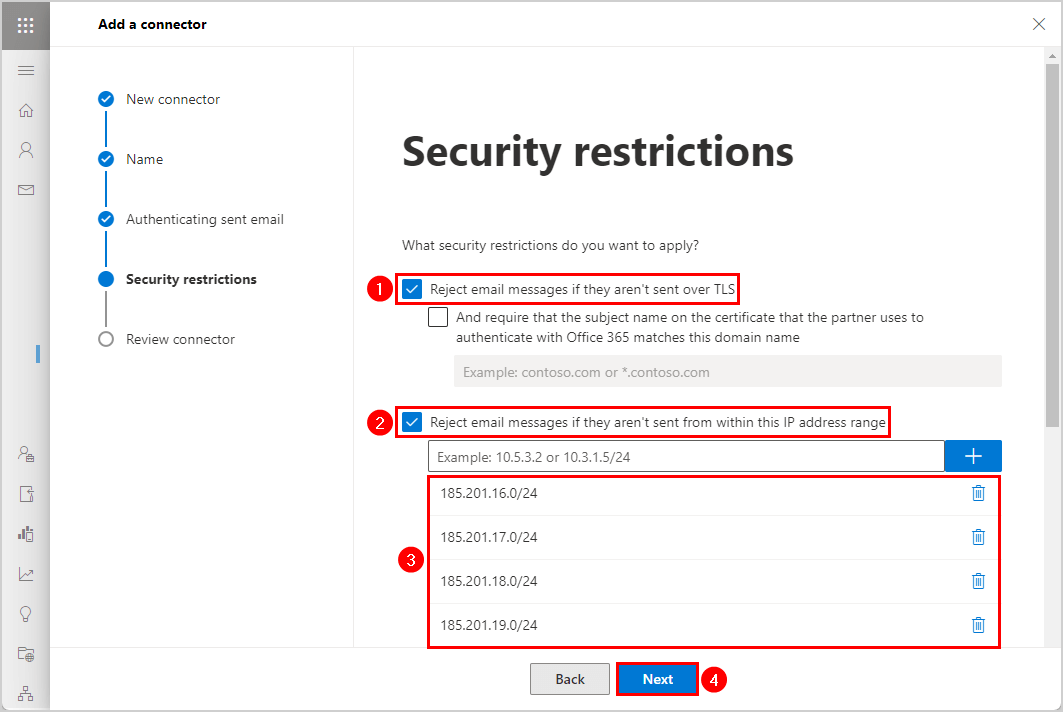
Click Next - Security restrictions.
Select Reject email messages if they aren’t sent over TLS
Select Reject email messages if they aren‘t sent from within this IP address range
Add the third-party filter service IP addresses
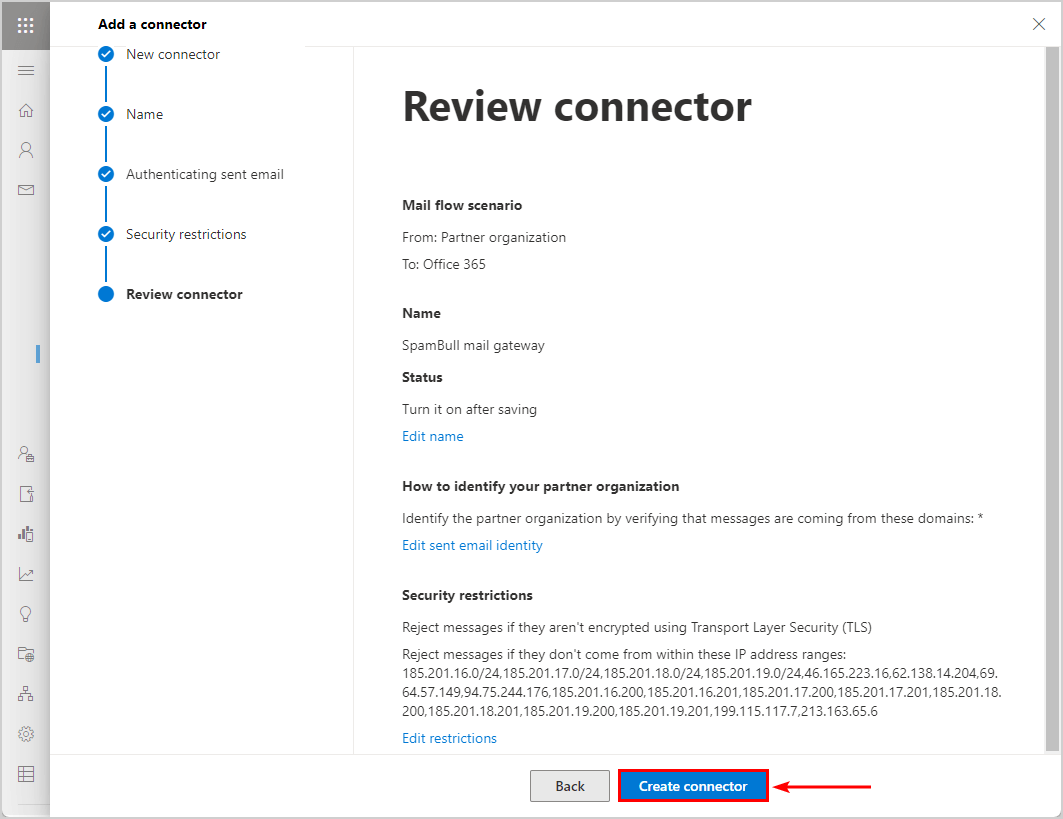
Click Next - Review connector.
Check and click Create connector
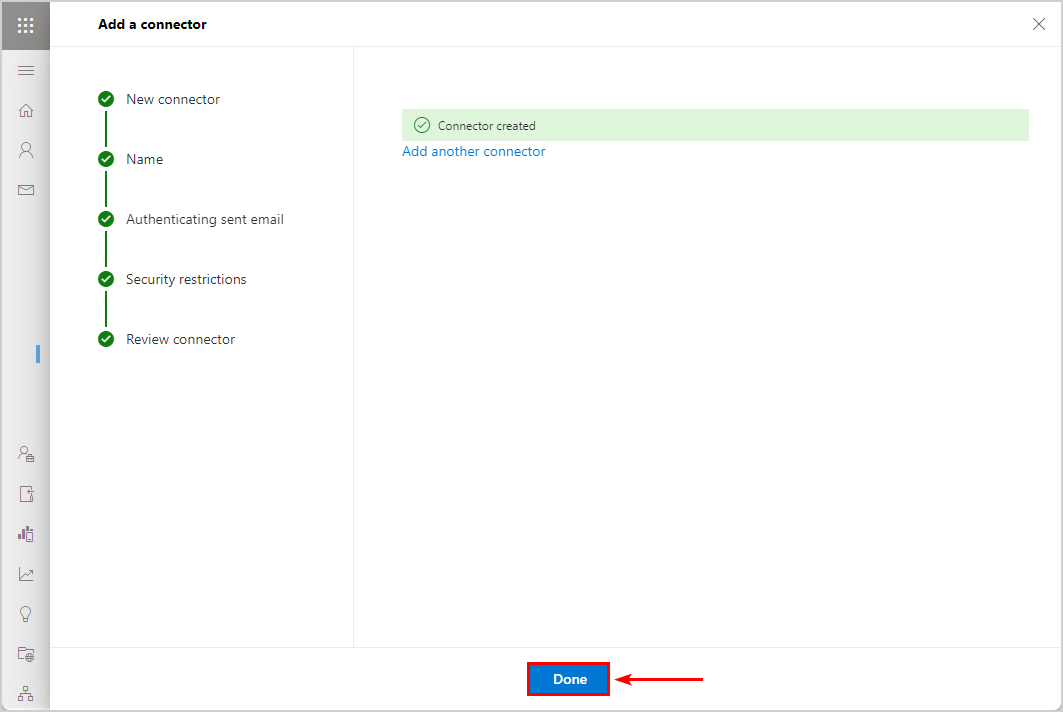
- Connector created.
Click Done
- New Connector added.
The inbound connector is created in the list
In the next step, we will configure enhanced filtering for the connecter we created.
Configure enhanced filtering for connector
This is an important step most people overlook. You need to enable enhanced filtering for the newly created connector, also known as skip listing.
Follow the below steps to enhance filtering for the connector:
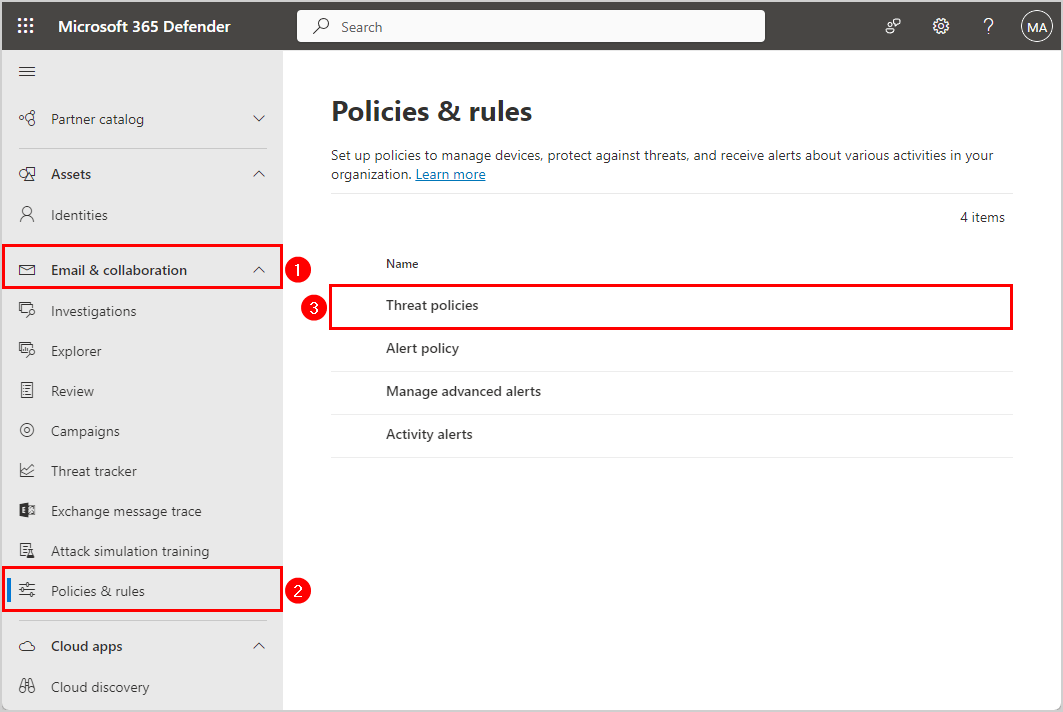
- Sign into Microsoft 365 Defender portal
- Expand Email & collaboration
- Click Policies & rules > Threat policies
- Scroll down and click Enhanced filtering
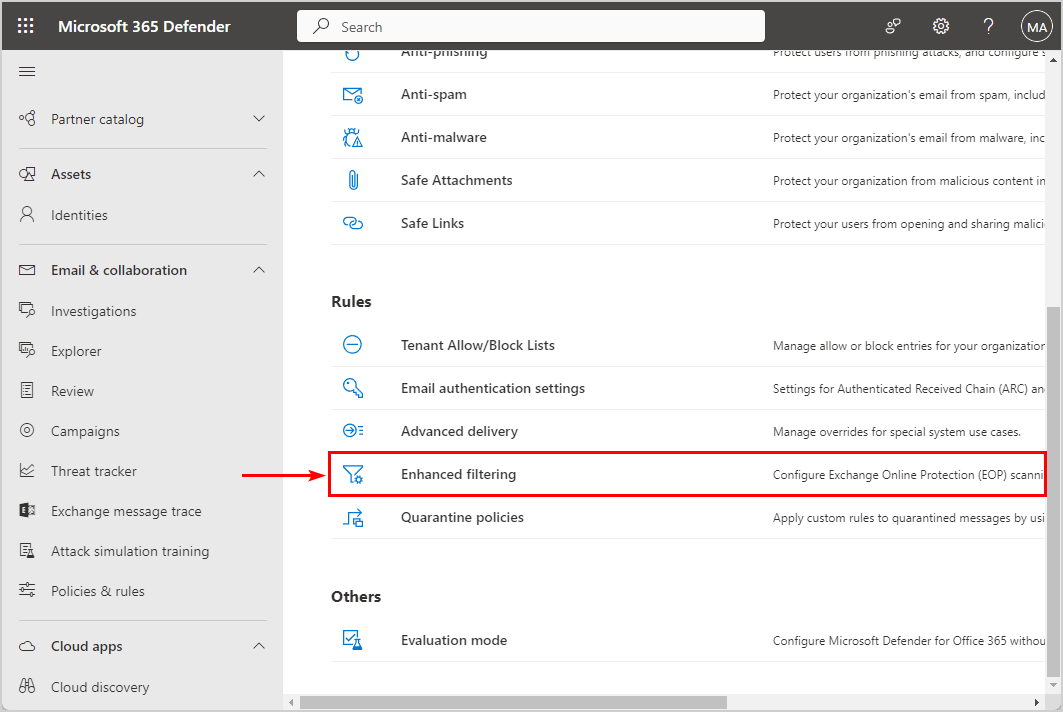
- Click your connector name SpamBull mail gateway
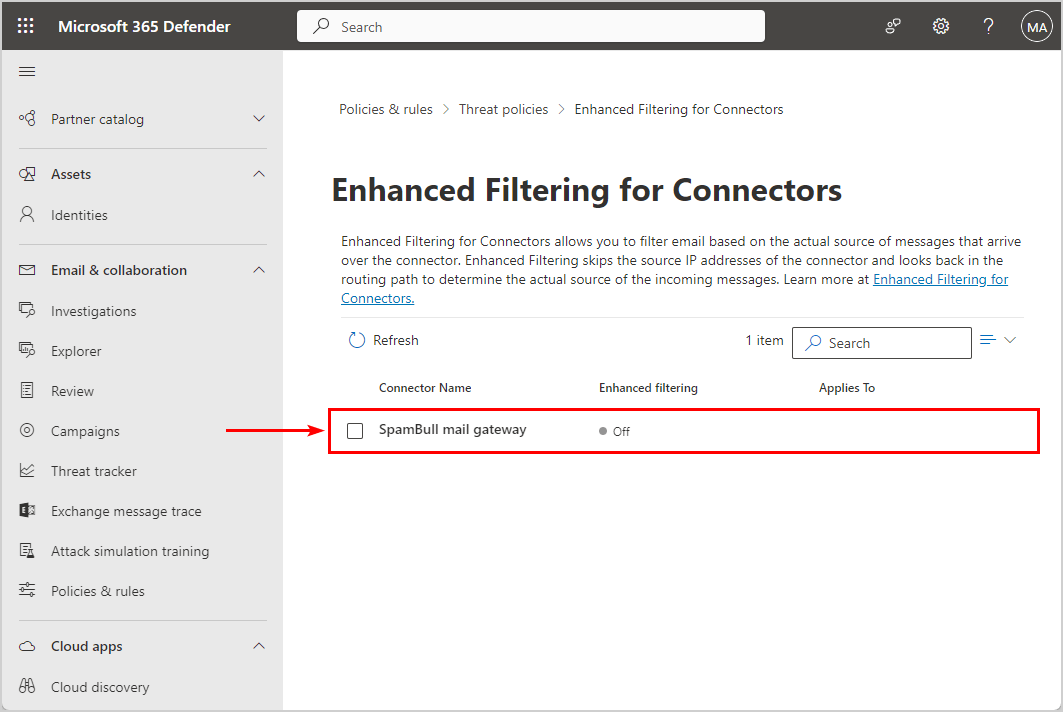
- Enable Skip these IP addresses that are associated with the connector
- Add the third-party service IP addresses
- Select Apply to entire organization
- Click Save
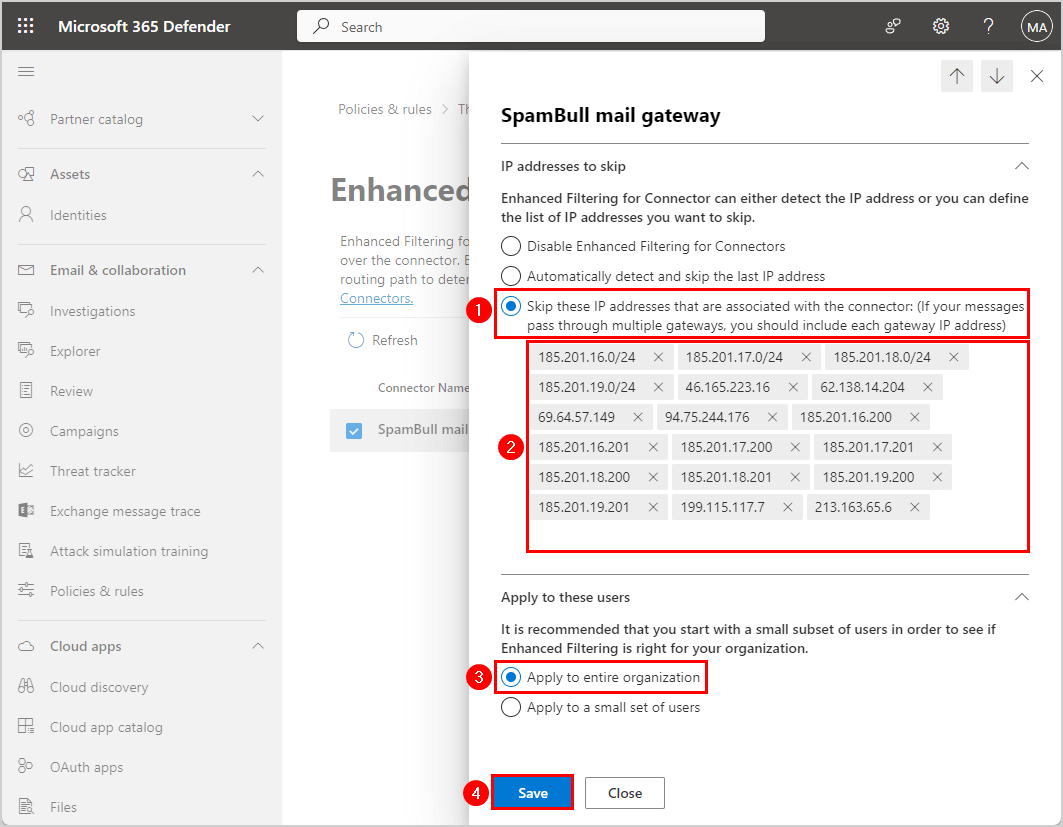
- The connector shows the enhanced filtering status On
The configuration is set up correctly, and the last step is to verify our work.
Test Exchange Online incoming mail flow only from third-party cloud service
To verify that we managed to implement the required Exchange Online incoming mail flow connector and enhanced filtering, we need to send an email test.
In our example, the domain is m365info.com. The Exchange Online that hosts the Microsoft 365 domain is m365info-com.mail.protection.outlook.com. If you need information about the Exchange Online MX record for a specific domain, read how to find the Microsoft MX record.
We want to verify the Exchange Online mail server that represents your domain name is willing to accept SMTP connection requests only from an approved entity.
Note: Wait 15 minutes before you test the mail filtering because it needs time to make the changes in the Microsoft cloud servers.
Send an email test SMTP session to your MX record. We will use an external SMTP test tool named Wormly.
How to send email to Microsoft 365 MX record hostname:
- Go to the Wormly SMTP test tool
- Type the Hostname
- Type a user Email address
- Type 25 in TCP port
- Select Yes under Send SMTP test email
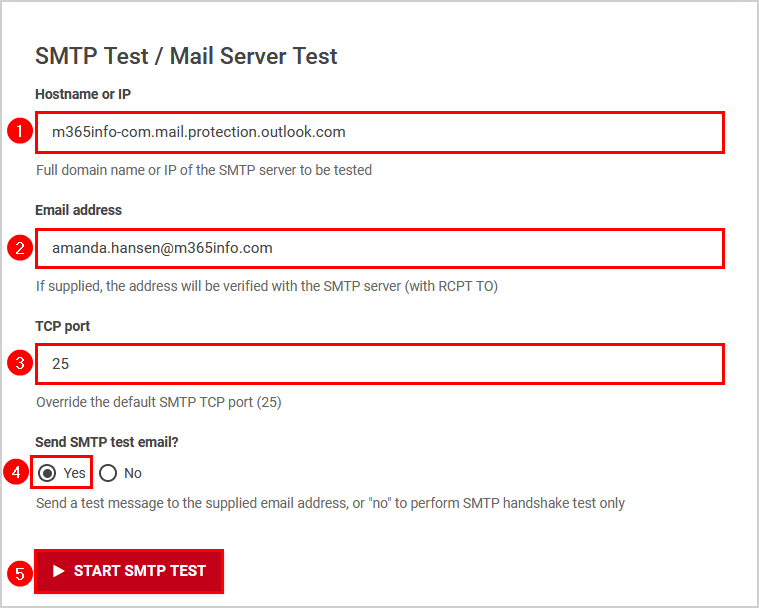
The result we want is that Exchange Online will reject the request for an SMTP session from a host whose IP address was not added to the incoming Exchange Online mail connector.
The SMTP test failed, so the below error is good.
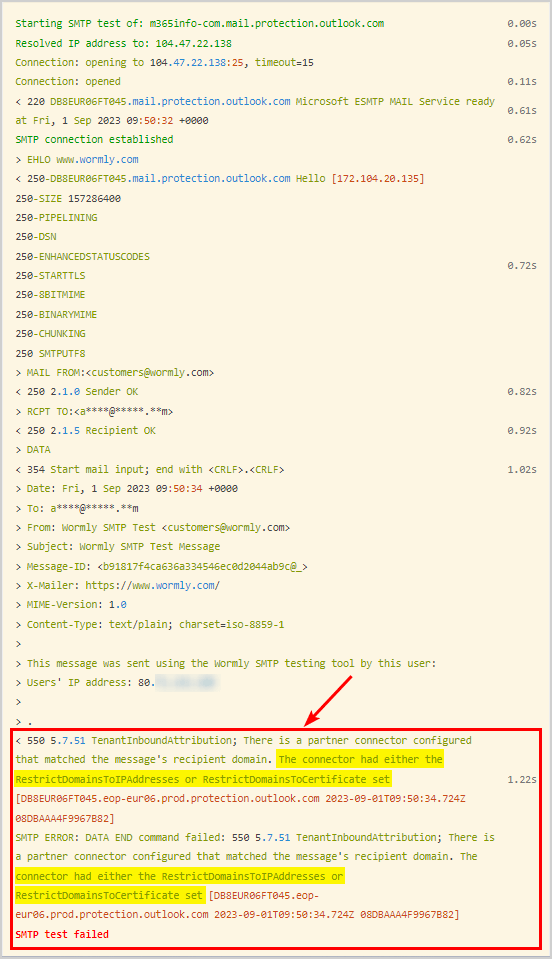
You successfully locked down the inbound email flow in Exchange Online to only accept emails from your third-party filter service.
Read more: How to configure SPF DKIM and DMARC for Microsoft 365 »
Conclusion
You learned how to configure Exchange Online to accept SMTP connection only from a specific mail security gateway. After you implement a mail flow configuration, spammers can’t bypass the MX record and deliver mail directly to Exchange Online. All messages will first go through the mail security gateway (third-party service) as expected.
Did you enjoy this article? You may also like How to simulate spam mail. Don’t forget to follow us and share this article.


I’ve read and heard reports of restricting to specific IP’s on a connector causing issues with other internal traffic to Exchange (specifically calendar invites). For example, forwarding a calendar invite from an external user, to another internal user, treats it as an external message and it gets blocked.
Are you aware of any issues like this that might affect internal routing, or other automated messages from 365 (maybe bookings or something) that wouldn’t use a third party gateway/smart host?
Thanks