If you have read all the articles that included in the current article series, you…
How to recognize an event in which Office 365 recipient send spam mail?
One of our Office 365 recipients complains that the E-mail that he sent to an external recipient is blocked or classified as “spam mail”. Our underlying assumption is that the problem is related to “Office 365 infrastructure”, and they should immediately fix the problem!
In the following article, we will learn how to recognize an event, in which Office 365 recipient send spam mail(outbound spam).
Table of contents
- FAQs: Office 365 recipient send spam mail
- Notify designated recipient about the event of outbound spam mail
- Simulating a scenario of outbound spam mail by Office 365 recipient
- Using Exchange Online message trace to get information about a possible event if outbound spam
- Looking for the value of – SFP:1501 in outgoing mail
FAQs: Office 365 recipient send spam mail
Q1: Did you allow yourself, to consider the possibility that mail is indeed “spam mail”?
A1: Technically speaking, there are many “causes” that lead to a scenario in which E-mail that sent by one of our Office 365 recipients classified as spam mail.
Posable cases could be:
- The IP address that represents the network from which the recipient sends his E-mail.
- The IP address that represents the mail server, which delivers the mail to the destination recipient.
- The E-mail content such “marketing content” or E-mail signature that include the URL address of a compromised website.
- A scenario of bulk mail in which specific recipient sends hundreds or thousands of E-mails.
- A domain name that appears on a blacklist.
- A user E-mail address that is listed in a Blacklist.
- Security mail settings that applied to the mail destination infrastructure (the mail server that represents the destination recipient).
- Security mail settings that are used by the destination recipient, such as inbox rule, antivirus and so on.
The bottom line is – that there are many different “causes” that lead to a scenario in which E-mail that is sent by one of our Office 365 recipients are classified as spam mail.

We need to be aware of these difference “cases” and be familiar with troubleshooting methods that will enable us to eliminate some of the “cases” until we find the specific “cause” of the problem.
For example – in a scenario in which E-mail that sent by Office 365 recipients are identified as spam mail by an external recipient.
Q2: Does Office 365 (Exchange Online) enforce “Spam Detection” for mail that is sent by Office 365 recipients?
A2: Yes, Office 365 and Exchange Online serve as a “mail platform” for many companies and organization. For this reason, Exchange Online enforces “spam check” not only for incoming E-mail but also for outgoing E-mail. In simple words – every E-mail that is sent out by Office 365 recipient is sent to spam mail inspection.
Q3: In case that Exchange Online classifies a particular outbound mail as “spam mail” what happened to this “spam mail”?
A3: Most of the time in case that after the “spam inspection” the E-mail that was sent from Office 365 recipient is classified as spam mail, Exchange Online will not block or delete the E-mail.
Instead, Exchange Online will implement two actions:
- Stamp the SCL value of the E-mail using a high number which uses for warning the other side that the E-mail message has a high potential to be a spam mail.
- Send the E-mail via a special Exchange server pool named -“High-Risk Risk Delivery Pool.”
High-Risk Delivery Pool
The term -“High-Risk Risk Delivery Pool” defines a specific Exchange Online that used to send “problematic E-mail” that was sent by Office 365 recipients.
Another point that I would like to emphasize is that when we use the term – “Exchange Online identifies outbound E-mail as a spam mail,” we have no certainty level of 100 percent that this is indeed a spam mail because there is some scenario of false positive in which a legitimate E-mail is mistakenly identified as spam mail.
In most of the scenarios in which Exchange Online spam filter identifies specific E-mail as “spam mail,” there is a real reason for this classification.
Additional reading:
- High Risk Delivery Pool and Exchange Online | Part 9#17
- High Risk Delivery Pool and Exchange Online | Part 10#17
SCL
The term SCL stands for – Spam Confidence Level. In Exchange based environment, Exchange uses the SCL as a method to provide information about the “spam level” of a specific E-mail item. The SCL values range is between -1 and 9.
SCL value of 3 or more indicates that the E-mail has “some issue” that relates to spam mail.
Q4: Is there an option in which I could be notified about such as an event or detect Traces or clues for such as event?
A4: Exchange Online enables us to define an E-mail address of a designated recipient who will be notified in the event in which Exchange Online recognizes E-mail that was sent by Office 365 recipients as “spam mail” and route the E-mail via the-“High Risk Delivery Pool” servers.

Notify designated recipient about the event of outbound spam mail
As mentioned, in Exchange Online based environment every E-mail that is sent by Office 365 recipients are automatically sent to spam filter for further examination.
In case that the spam filter “decide” that the particular E-mail is a spam mail, the E-mail SCL value will be raised, and the E-mail will be forwarded to the -“High-Risk Risk Delivery Pool” servers.
The main issue is that the recipient whom his mail identified as spam and we (Exchange Online administrator) are not aware of this event.
In other words, by default, the recipient will not know about this problem. Only in hindsight, after the E-mail will be sent Outlook to the destination recipient and reach to the junk mail folder or blocked.
The good news is that Exchange Online enables us to configure the following options that relate to outbound spam (spam mail that is sent by our Office 365 recipients).
- Ask from Exchange Online to send a copy of each outgoing E-mail that was identified as spam mail to a designated recipient.
- Ask from Exchange Online to send a notification to a designated recipient about the event in which Exchange Online blocked a particular Office 365 recipients.
The advantage of this setting is that we, receive an early warning about an event of outbound spam.
The disadvantages are that in the current time, Exchange Online doesn’t include the option of sending an incident report to the designated recipient who includes a copy of the “spam mail.”
Instead, Exchange Online sends a copy of the outbound spam mail to the designated recipient.
When the E-mail reaches to the designated recipient, the E-mail is automatically saved in the junk mail folder (because of the high SCL value). Also, from the designated recipient point of view, it’s not easy to understand that the E-mail message that he got was a “copy” that was sent by another Office 365 recipient.
How to configure outbound spam Exchange Online settings
- Sign in to Exchange Online admin portal
- On the left menu bar, select the menu – protection
- On the top-level menu bar, choose the menu – outbound spam.
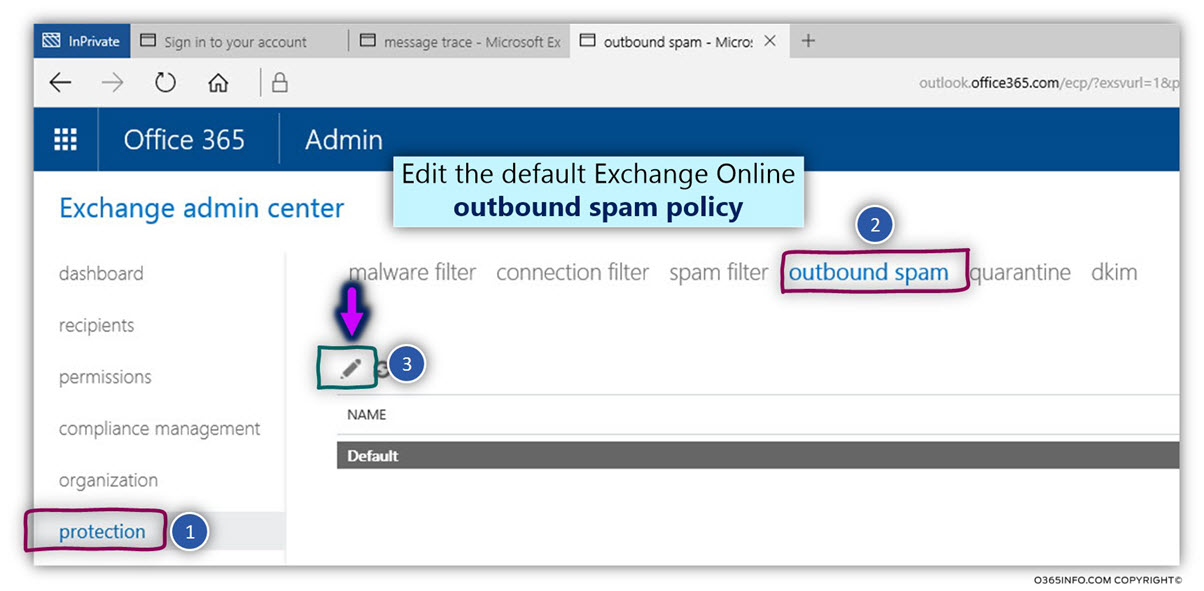
- Select the menu outbound spam preferences
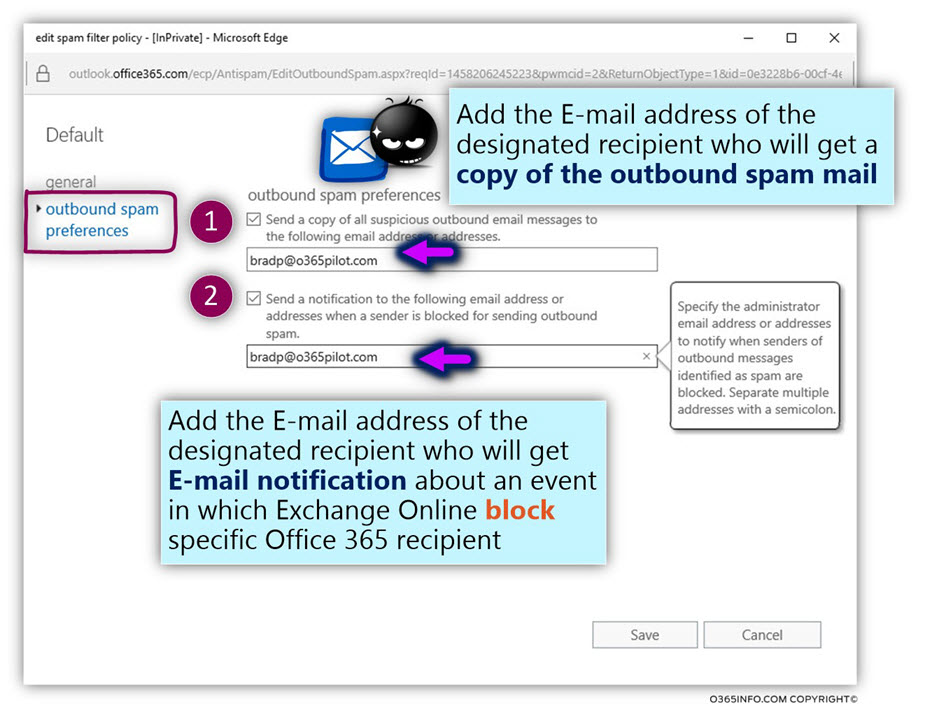
In the outbound spam preferences section, select the following options:
Send a copy of all suspicious outbound email messages to the following email address or addresses.
Specify the E-mail address or addresses of administrators who will receive copies of all suspicious outbound messages. You can separate multiple addresses with a semicolon.
In our example, the Exchange Online administrator is – Brad.
Send a notification to the following email address or addresses when a sender is blocked from sending outbound spam.
Specify the E-mail address or addresses of administrators who will receive E-mail notification about an event in which Exchange Online block particular Office 365 recipient from sending outbound E-mail.
Simulating a scenario of outbound spam mail by Office 365 recipient
In the previous section, we review the process of how to configure the Exchange Online outbound spam settings.
The central question that we have known is – how can we know that this setup is actually working?
In the current section, I would like to show you a little trick, that we can use for simulating spam mail. The trick implemented by sending E-mail that includes a particular text string.
When Exchange Online gets the E-mail with the specific text string, he is configured to identify the E-mail as “spam mail.”
Using this method of – simulating spam mail, enable us to test the Exchange Online outbound spam settings and in addition enable us to understand how Exchange Online “react” to the event of outbound spam mail.
Note: In case that you want to read more information about the process of simulating spam mail, you can read the article How to simulate spam mail?.
Simulating spam mail
In the following example, we will perform the following test
In our scenario, Bob is the Office 365 recipients who send outbound spam mail.
We will be logging into Bob’s mailbox and send a spam mail.
Our expectation is that the Exchange Online spam filter will “capture” this event and as a response, a copy of the outbound spam mail will be sent to our Exchange Online administrator – Brad.
- Login to Bob’s mailbox
By using Bob mailbox, we create a new E-mail message and add to the E-mail message the following text string
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X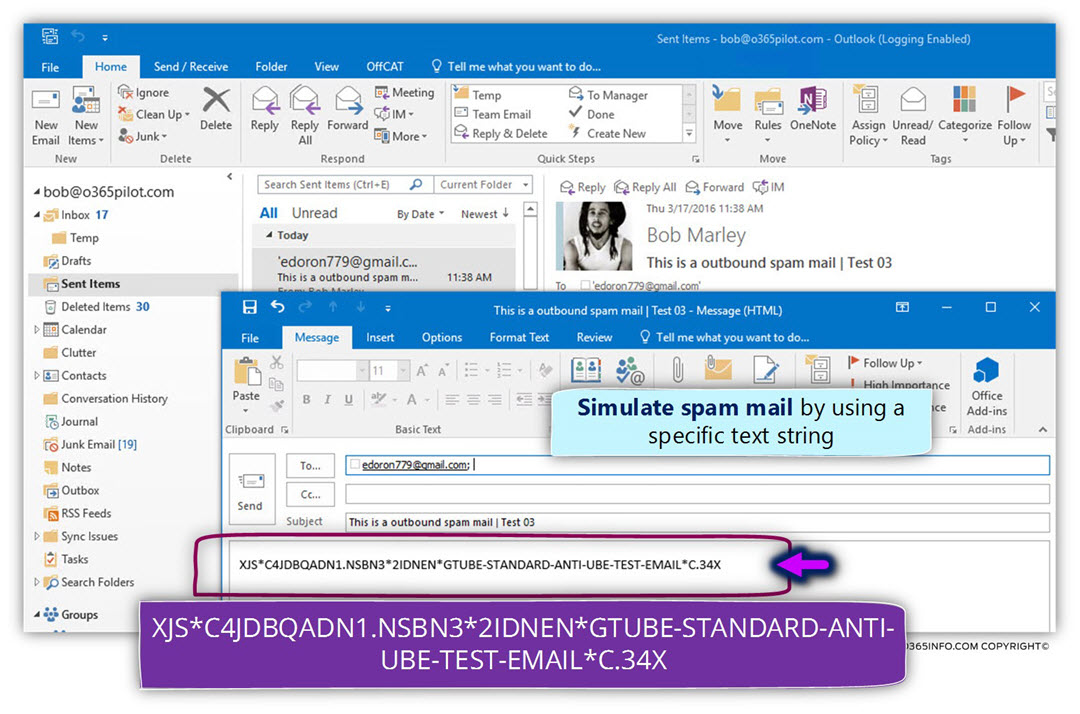
When the E-mail reaches Exchange Online, the E-mail sent to the spam filter for further examination.
The E-mail identified as spam mail.
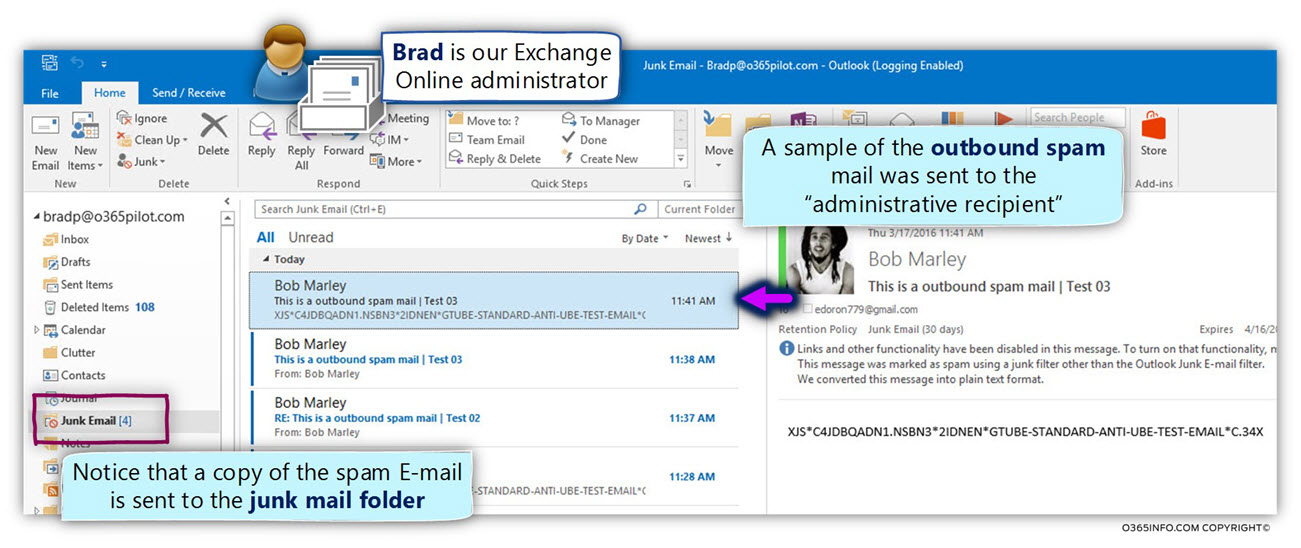
Exchange Online sends a copy of the E-mail to the designated recipient who configured in the previous section – notify the designated recipient about the event of outbound spam.
As a result, a copy of the outbound spam mail was sent to Brad.
Notice that the E-mail sent to the Junk mail folder because the E-mail has a high SCL value.
Using Exchange Online message trace to get information about a possible event if outbound spam
In a scenario in which the Exchange Online identifies a specific outgoing E-mail is “spam mail,” the E-mail will be forwarded to the -“High-Risk Risk Delivery Pool” servers.
The event of “forwarded to E-mail to the -“High-Risk Risk Delivery Pool” server documented in the Exchange Online log file.
In other words, in case that outgoing E-mail was sent via the – “High-Risk Risk Delivery Pool,” we can follow the trail of the particular E-mail message by using the Exchange. Online message trace.
Our scenario characters
In our scenario, we suspect that one of our users named Bob (that uses the E-mail address bob@o365pilot.com), sends E-mail that is recognized by Exchange Online as spam mail (outbound spam).
For this reason, the E-mail is “routed” to the -“High-Risk Risk Delivery Pool” servers.
Also, we have already configured the Exchange Online outbound spam policy to send a copy of such as E-mail to a designated recipient – Brad (our Exchange Online administrator).
To be able to demonstrate- how this “outbound spam event” is documented in the Exchange Online log, we will perform the following steps:
- Simulate an event of an outbound spam mail – we will send from Bob’s mailbox, an E-mail that includes a particular text string that will identify by Exchange Online as “spam mail.”
- Using Exchange Online message trace – we will use the Exchange Online message to trace to look at the Exchange Online log file and find more detailed information about this specific event.
Using the Exchange Online message trace
- Sign in to Exchange Online admin center
- On the left menu bar, select the menu – mail flow
- On the top menu bar, select the menu – message trace
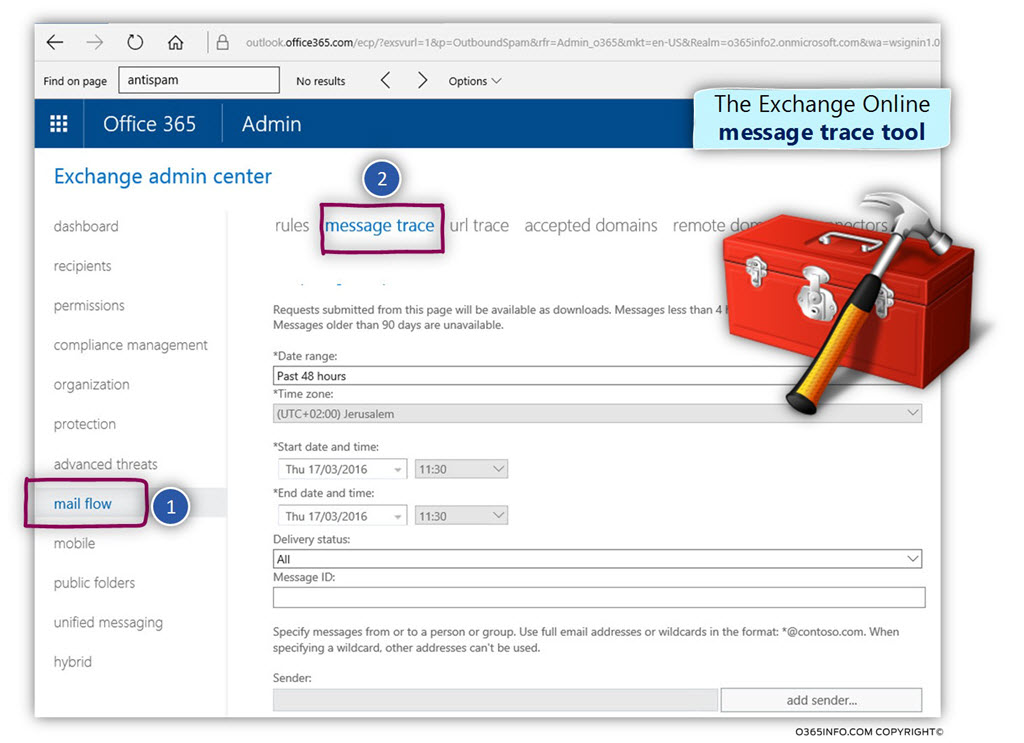
In our specific scenario, we would like to get more information about E-mail messages that was sent by Bob.
- Select the option – add sender…
- Select the specific recipient name (bob@o365pilot.com in our scenario).
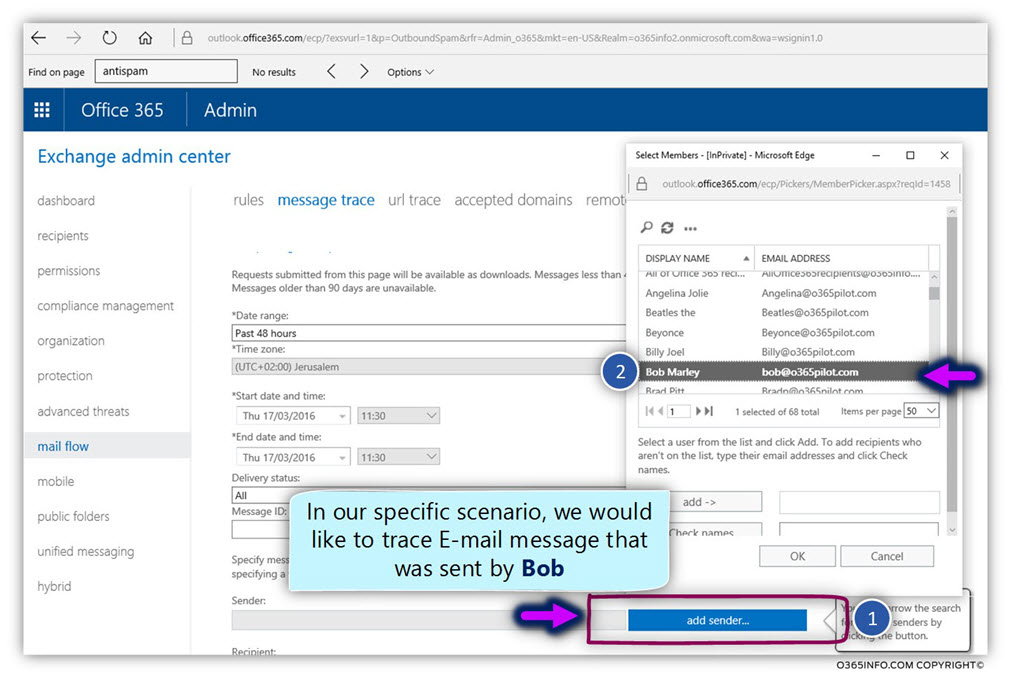
- Select the option – add ->
- Select the option – OK
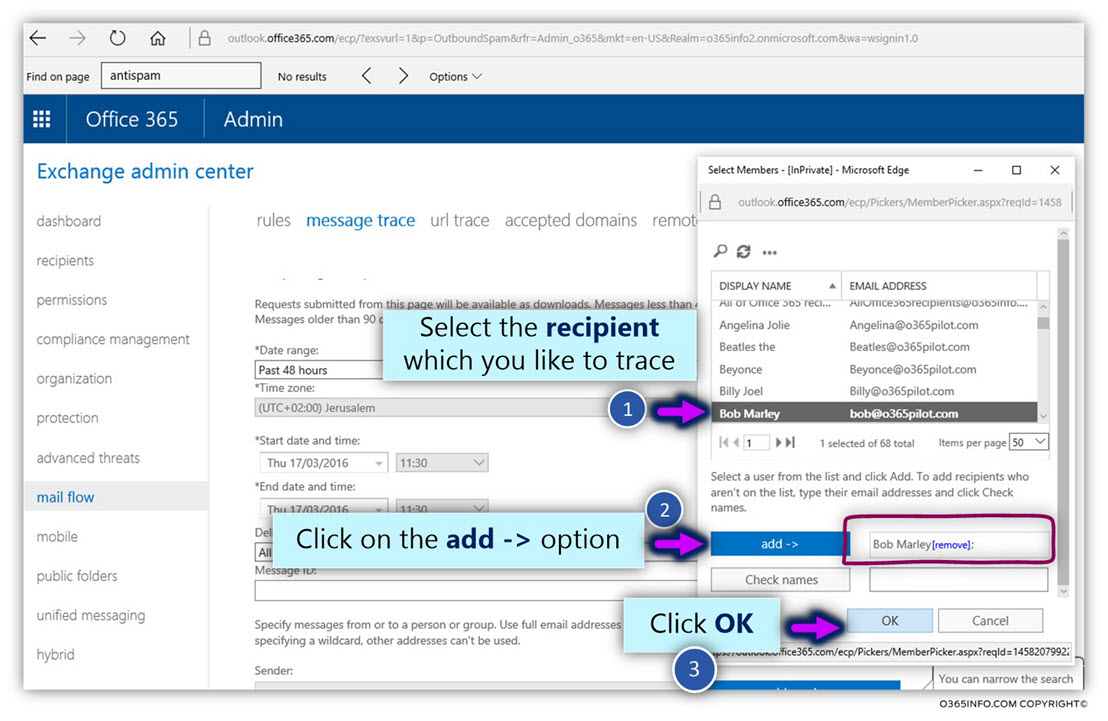
- Select the option – search
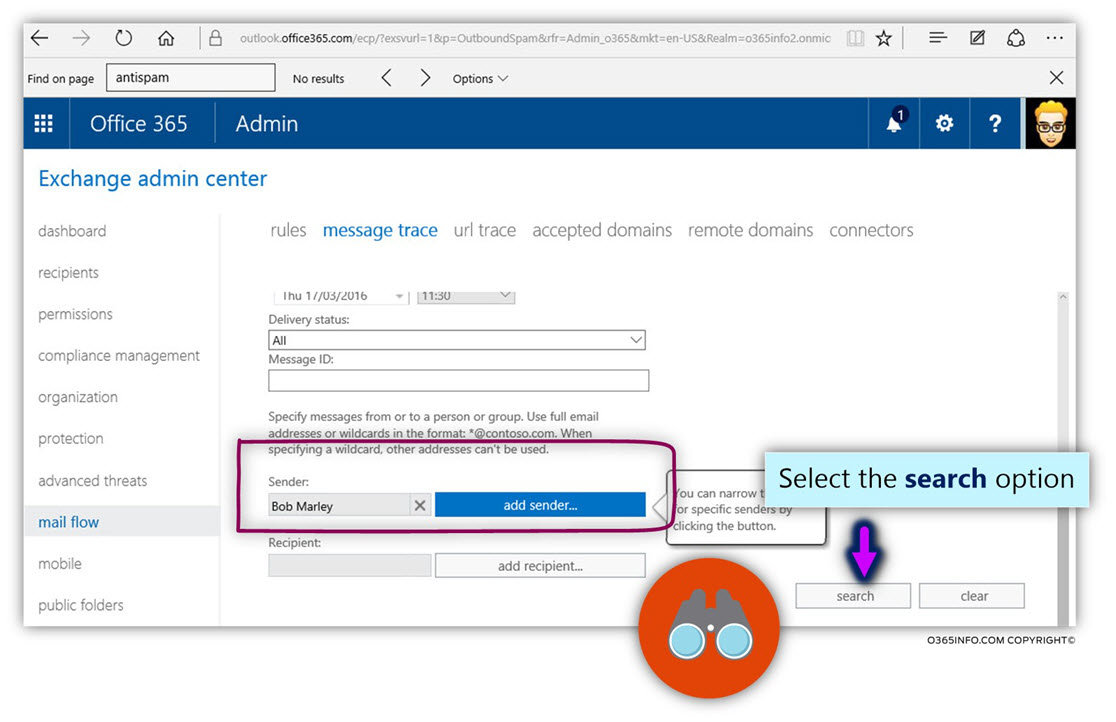
In our scenario, we have configured the outbound spam preference to send a copy of the E-mail that was identified as outbound spam E-mail, to a designated recipient (Brad, our Exchange Online administrator), each time the Exchange Online capture an event of internal spoof mail.
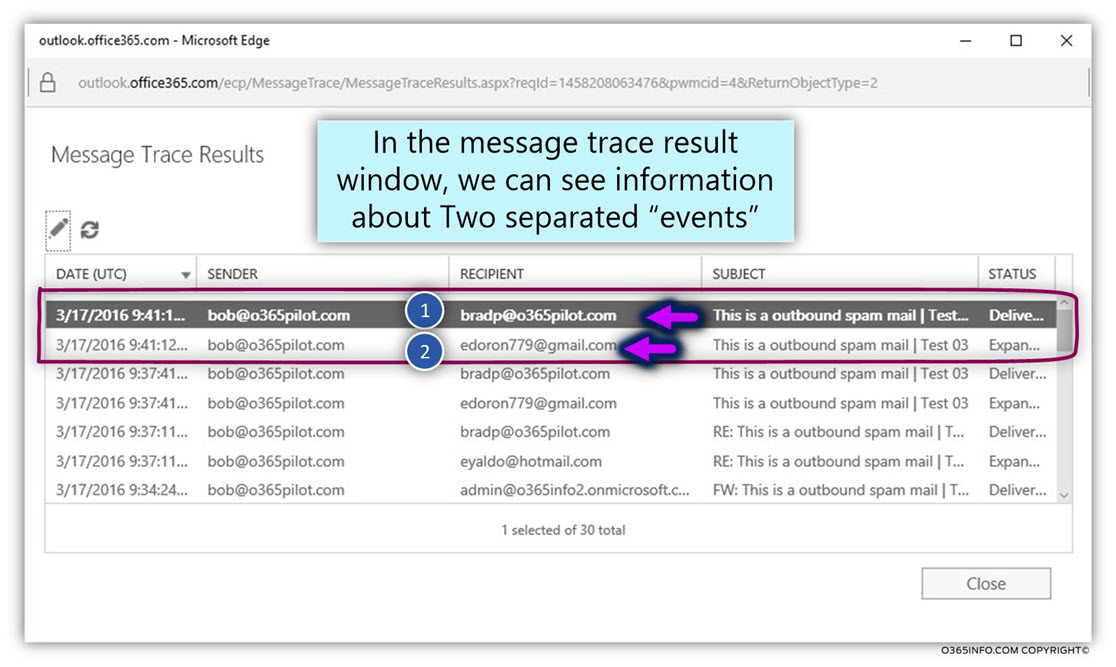
In the following screenshot, we can see the result of our search.
When the Office 365 recipient sent an “outgoing spam mail” to the destination recipient (edoron779@gmail.com), the event was recorded in saved to the Exchange Online log file.
We can see that there are two separate events.
When the Exchange Online spam filter identifies the E-mail that was sent by Bob as “spam E-mail,” two different events take place alongside:
- Send the E-mail to the destination recipient (number 1).
- Send a copy of the E-mail to the designated recipient, in our scenario – Brad (number 2).
One of the most distinct advantages of the Exchange Online log file and the Exchange Online message trace is that we have the ability to get a very detailed information about each of mail transactions that were recorded.
In our example, we would like to get more information about the event in which Exchange Online sends Bob’s E-mail to the destination recipient (the external Gmail recipient).
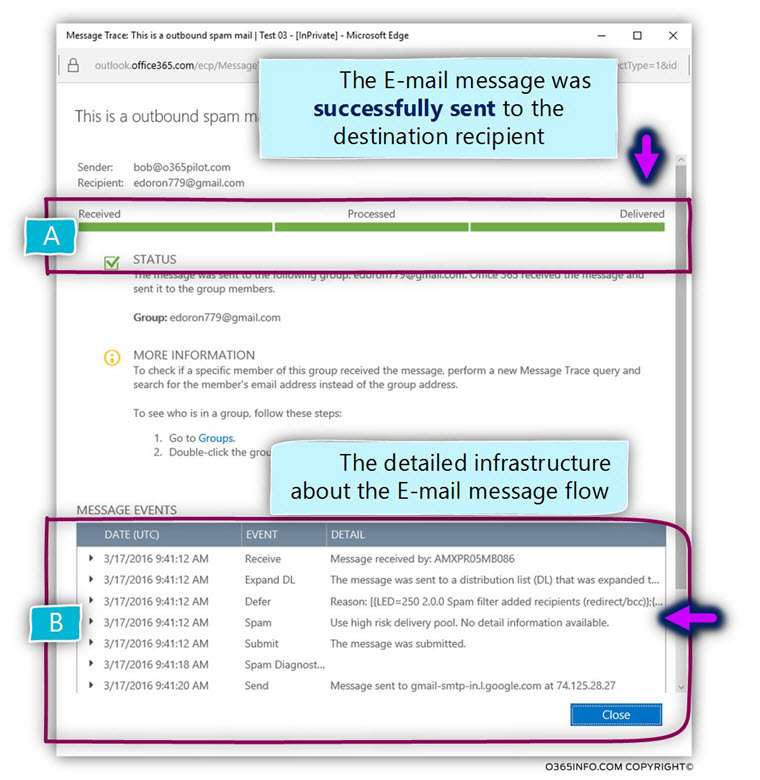
When we double-click on the Log row that includes information about the E-mail that was sent by Bob to the external recipient, we can see the following details:
The first detailed that I would like to emphasize is that the “spam E-mail”, was successfully sent to the destination recipient (A).
As mentioned, Exchange Online will not delete or block E-mail message that identified as outbound spam mail, but instead, will route the E-mail to the -“High-Risk Risk Delivery Pool.”
At the bottom part of the information window, we can see more details about the specific E-mail transaction (B).
Event 1 – send a copy of the outbound spam E-mail to a designated recipient
In our scenario, we configure the default Exchange Online outbound spam policy to send a copy of the E-mail that was identified spam to a designated recipient (Brad).
This event was registered in the Exchange Online log file as:
Reason: [{LED=250 2.0.0 Spam filter added recipients ?(redirect/bcc)?};{MSG=};{FQDN=};{IP=};{LRT=}]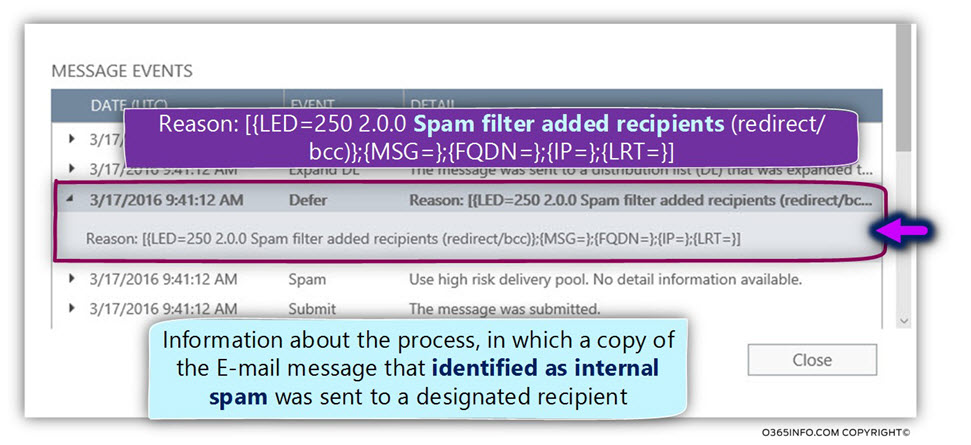
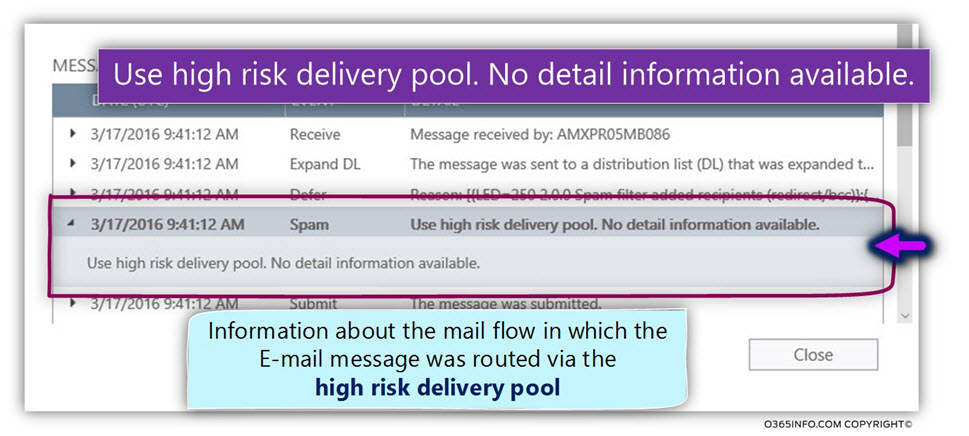
Event 2 – Routing the outbound spam mail to the -“High-Risk Risk Delivery Pool” servers.
Because the E-mail classified as “problematic E-mail” Exchange Online will not delete the E-mail but instead, send the E-mail to the – High-Risk Delivery Pool servers.
Looking for the value of – SFP:1501 in outgoing mail
In this section, we review an additional interesting “evidence” for a scenario in which Exchange Online identifies a specific outgoing E-mail as a “spam mail” and for this reason, route the E-mail to the -“High-Risk Risk Delivery Pool” servers.
For example, let’s go back to the original scenario – one of our Office 365 recipients complained that the E-mail that he sent to the external recipient is blocked or classified as a “spam mail.”
How can we know what the real cause of this problem was?
- Did the mail server of the destination recipient decide to classify the E-mail as spam mail?
- Did the destination recipient antivirus decide to classify the E-mail as spam mail?
- Maybe the E-mail that sent by our Office 365 recipients are indeed a spam mail?
In case that we are dealing with a scenario in which the Exchange Online spam filter scan the outgoing E-mail that was sent by our Office 365 recipient and decides to classify the E-mail as “spam mail,” the E-mail will be sent via the -“High-Risk Risk Delivery Pool” servers.
Also, Exchange Online will add the following information to the E-mail header.
- The value of the SCL – Exchange Online will raise the SCL value to a value in the
range 2-9 (the specific number is added based on the “spam level” of the specific E-mail). - Exchange adds the following value – SFP:1501 , to the specific E-mail
header named – X-Forefront-Antispam-Report
An interesting observation regarding the – SFP:1501 value
The interesting thing is that at the current time, there is not much information about this “Exchange Online vale” and detailed description about what this value represents.
Given that we will be able to get a copy of the E-mail message that was sent to the destination recipient, by analyzing the information that appears in the E-mail header, we can find traces for such as event, and in case that we don’t find such traces, we can assume that the E-mail was classified as spam by another element.
To be able to look at the “hidden information” that saved in the E-mail header, we will use the Microsoft web-based tool – Exchange Remote Connectivity Analyzer.
Scenario description
To be able to demonstrate such an event we will use the following scenario:
We will use Bob’s mailbox (an Office 365 recipient) for sending E-mail that will be identified by Exchange spam filter as “outbound spam mail.”
Our expectation is that the Exchange Online spam filter will “capture” this event and will implement the following procedure:
- Reroute the E-mail message to the -“High-Risk Risk Delivery Pool” servers.
- Raise the SCL value of the specific E-mail
- Add the following value – SFP:1501 , to the E-mail header
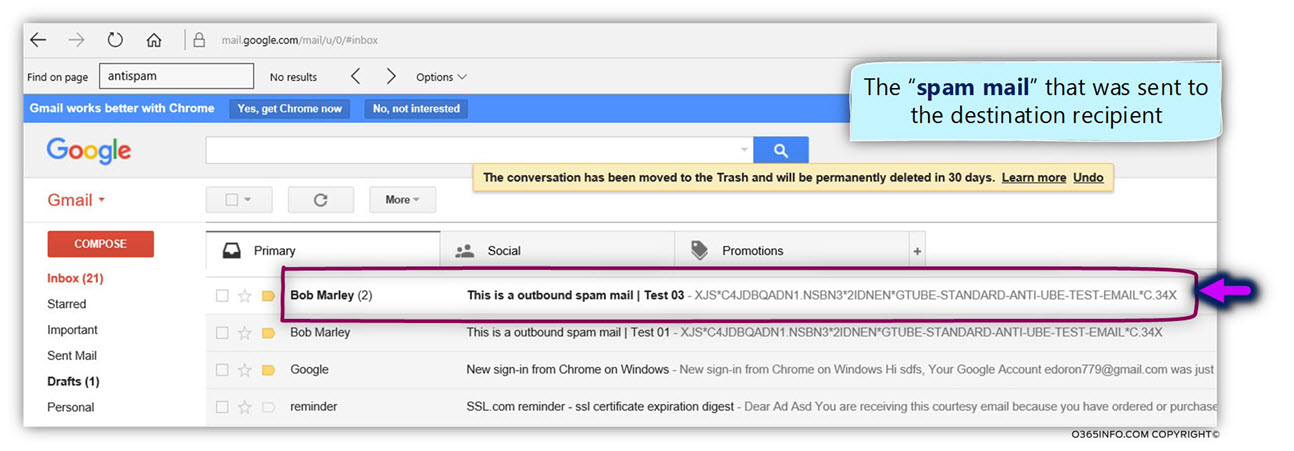
In our scenario, Bob sends the “spam mail” to a Gmail recipient.
In the following screenshot, we can see that the E-mail successfully sent to the Gmail destination recipient.
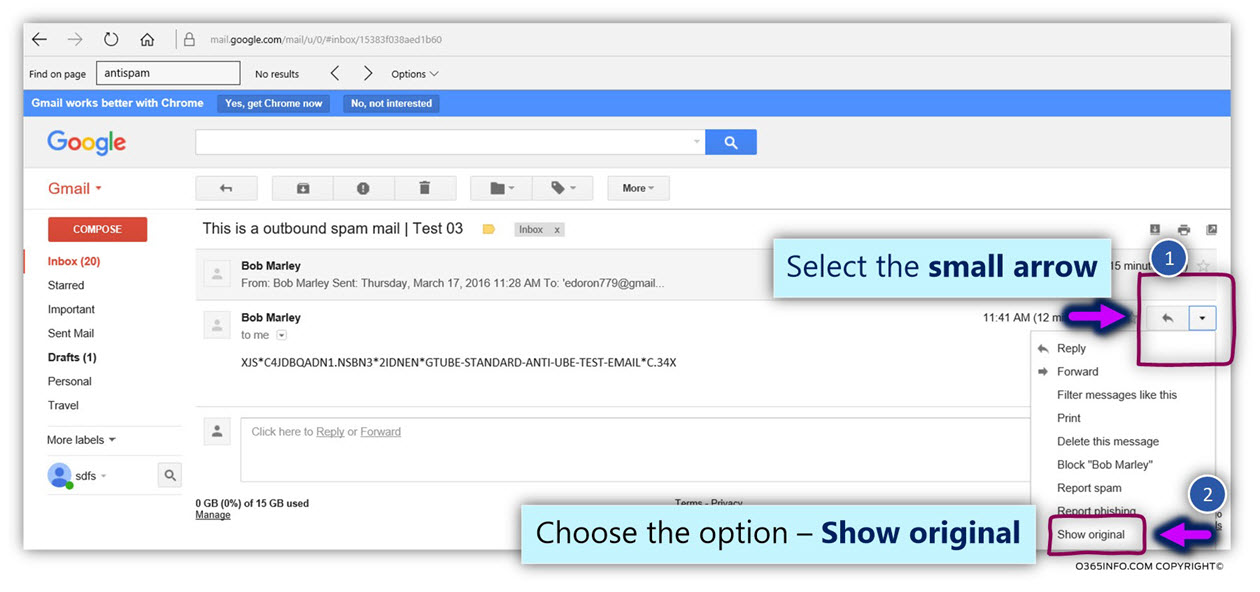
To be able to analyze the E-mail header when using a Gmail account, will need to use the following steps:
- On the “right part” of the E-mail, click on the small arrow
- Select the menu – Show original
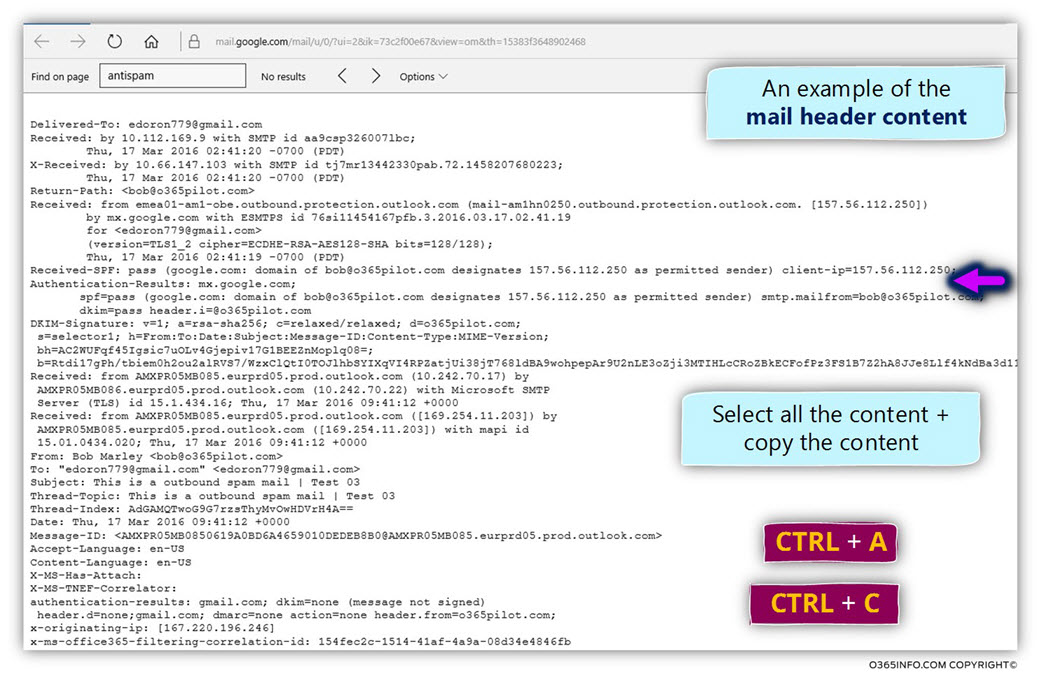
In the following screenshot, we can see the content of the E-mail header.
We will need to copy the substance of the E-mail header.
- Select the Keyboard key combination – CTRL + A (Select All)
- Select the Keyboard key combination – CTRL + C (Copy)
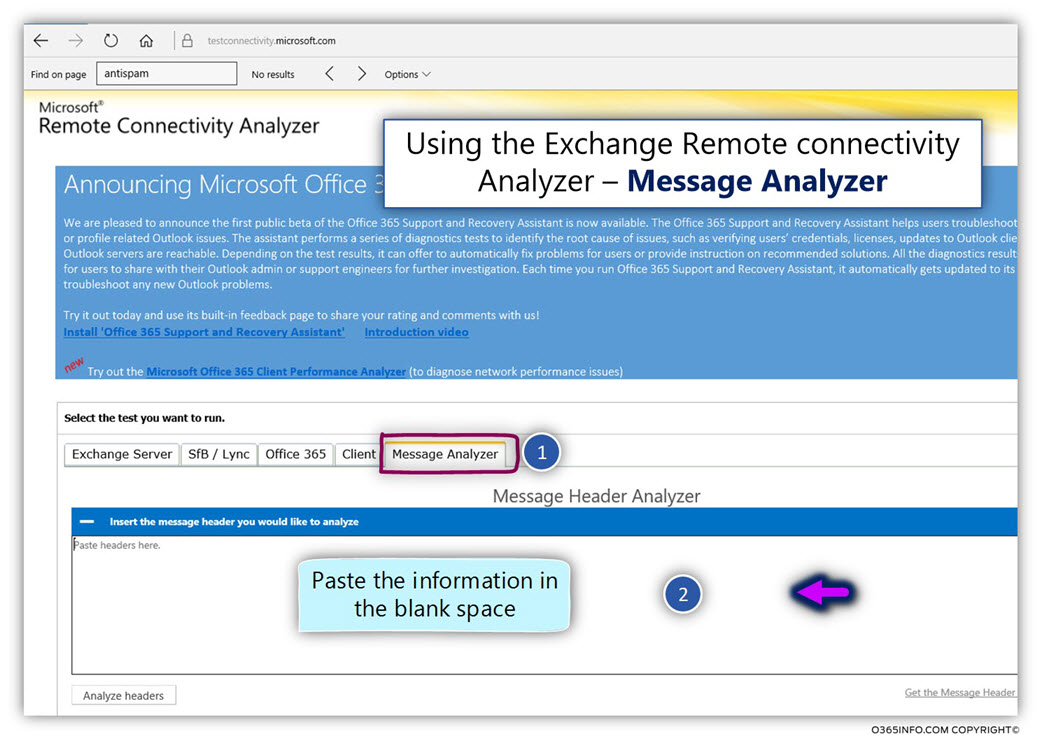
In this step, we will use the Microsoft web-based tool – Exchange Remote Connectivity Analyzer, to analyze the information from the E-mail header.
- Access the Exchange Remote Connectivity Analyzer
- Select the tab – Message Analyzer
- Paste the information copied in the previous step (the E-mail header content).
- Click on – Analyze headers
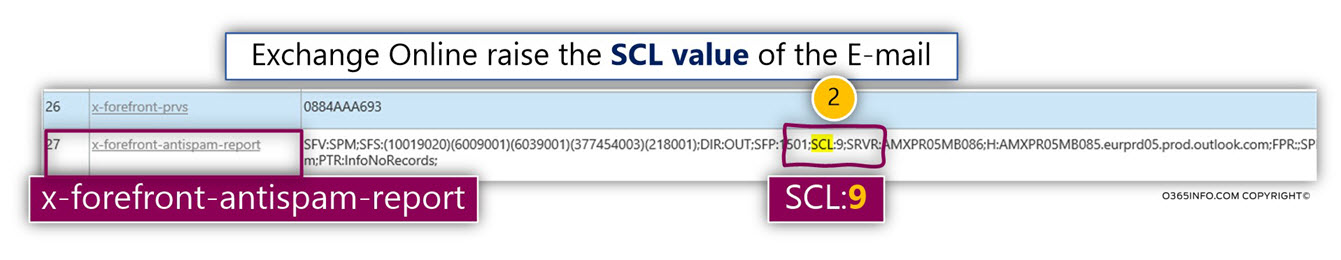
In the following screenshot, we can see the content of the mail header named x-forefront-antispam-report.
The value of SPF:150 “tells us” that the specific E-mail message was routed via the “High-Risk Risk Delivery Pool” servers.

Also, we can see that the SCL value of the E-mail message is – 9.
In case you like to test your Exchange Online infrastructure by simulating a scenario in which Office 365 send spam mail, and verify the flow of events, you can read the article How to simulate spam mail?
In case that you like to read more information about the subject of – “High Risk Delivery Pool and Exchange Online”, you can read the articles:


Hi,
I did all the mentioned steps over here and when i Checked the Test Analyzer this is what I found for x-forefront-antispam-report:
SFP:;SCL:-1.
Can, anyone suggest me what needs to be done in this case?