In the current article, we will review how to deal with Spoof E-mail scenario in…
Detect spoof E-mail and add disclaimer using Exchange Online rule |Part 6#12
In the current article, we will review how to deal with Spoof mail by creating an Exchange rule that will identify incoming Spoof E-mail (spoofed sender).
In such scenario, we would like to implement the following sequence of actions:
- Add a disclaimer to the E-mail message.
- Prepend the E-mail subject.
- Generate + send an incident report to a designated recipient.
Table of contents
- Dealing with Spoof mail attack | The business needs
- The Exchange Online Spoofed E-mail rule structure and logic
- Configuring Exchange Online Rule That Will – – add a disclaimer to the E-mail + prepend the E-mail subject
- Verifying That The Exchange Online Spoofed E-Mail Rule Is Working Properly
- The next article in the current article series
In our scenario, we prefer not to delete or block email messages that have the characters of Spoof E-mail and instead, we want to let the “end user” to decide if the particular mail item is a Spoof E-mail or not.
We want to enable the E-mail to reach the organization user mailbox, but at the same time, we want to inform the recipient that the E-mail that he gets, considered as “problematic E-mail.”
The “recipient warning” will be implemented by adding text to the E-mail subject + add a disclaimer to the E-mail.
The information about the possible Spoof E-mail event will be logged and reported by using the Exchange Online rule option named – incident report.
The main characters of the Spoof E-mail attack scenario:
Our company CIO, report that got an E-mail, that sent to him by the company CFO, that asks him to transfer a substantial amount of money to a particular bank account.
After a short inquiry, he discovers that the E-mail is a Spoof mail!
Dealing with Spoof mail attack | The business needs
The business need and the goals that we need to accomplish are as follows:
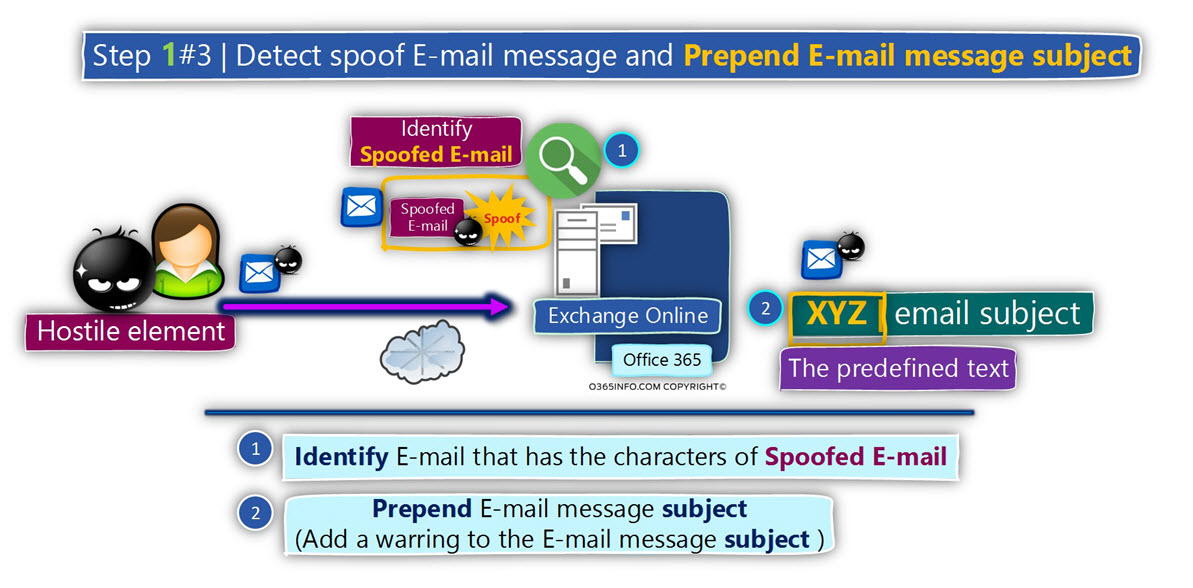
- We want to identify events in which E-mail messages that sent to our organization recipient have a high chance of being spoofed E-mail (spoofed sender).
- We don’t want to intervene in the mail flow. The decision “what to do” with the E-mail message that there is a high chance that the sender spoofs his identity, will be considered as “user decision.”
- Our primary purpose is – to inform the recipient that the E-mail message that sent to him considered as “problematic E-mail.” We want to “warn” the organization recipient by adding a disclaimer to the E-mail + prepend the E-mail subject.
- We want to send information + a sample of the Spoofed E-mail to a designated shared mailbox.
- We want that a designated user (such as the Exchange Online administrator), will be able to access the shared mailbox that stores the incident reports, so, he could inspect and analyze the spoofed E-mail message.
The Exchange Online Spoofed E-mail rule structure and logic
The Exchange Online rule trigger
The “trigger” that will activate the Exchange Online “Spoofed E-mail rule” will be based on the following two conditions (a combination of condition 1 + condition 2):
- An incoming E-mail message that is sent by a non-authenticated recipient (recipient who doesn’t provide user credentials).
- A recipient who presents himself by using an E-mail address that includes our public domain name. In our specific scenario, an E-mail address that includes the domain name –com
The Exchange Online rule response
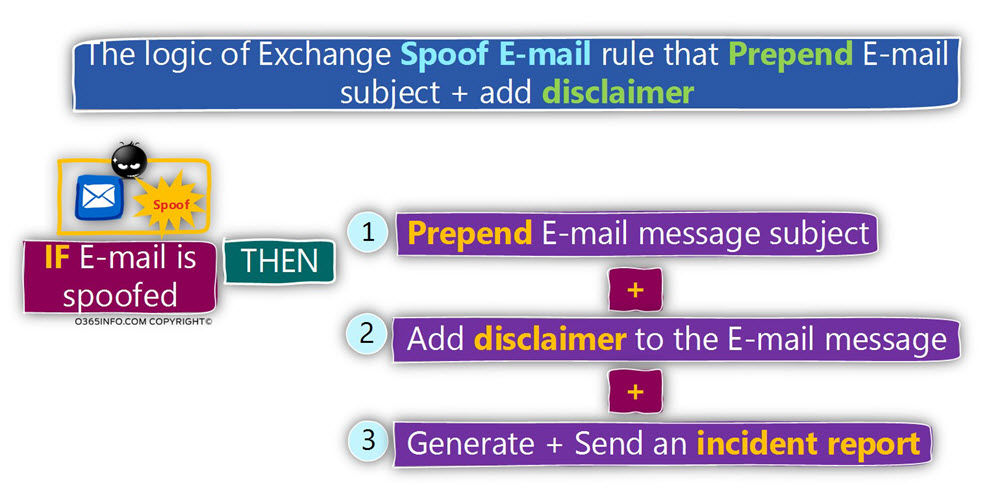
The “action” that will be executed by our Exchange Online “Spoofed E-mail rule” will include the following “parts”:
- Identify E-mail that has the characters of Spoofed E-mail
- Prepend the E-mail subject
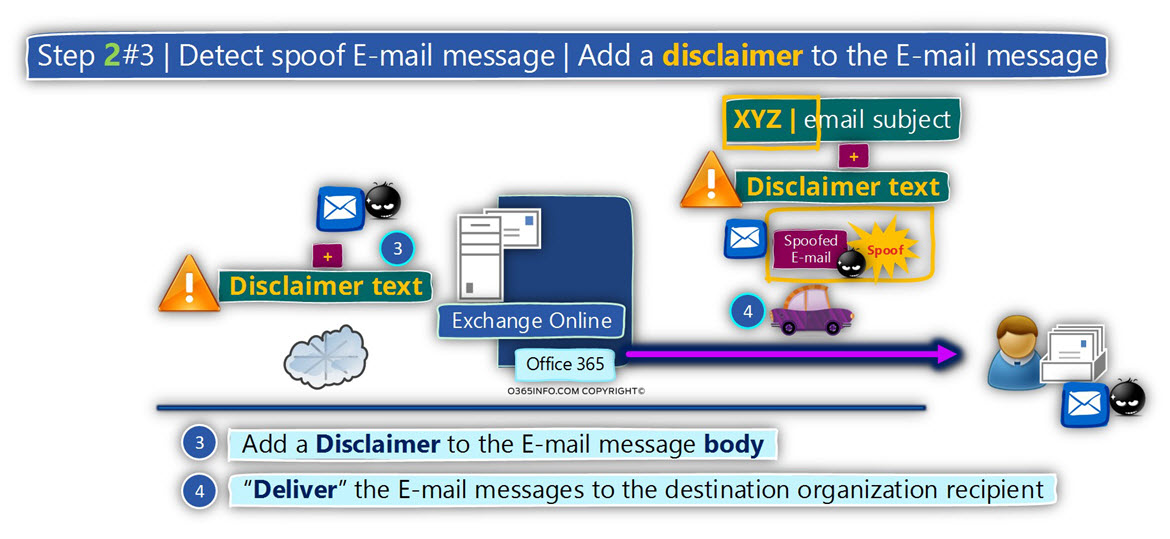
- Add a disclaimer to the E-mail
- Generate an incident report that will be sent to the E-mail address of the designated recipient\s. In our specific scenario, we ask to send the incident report to a designated recipient (shared mailbox named – Spoof E-mail mailbox).
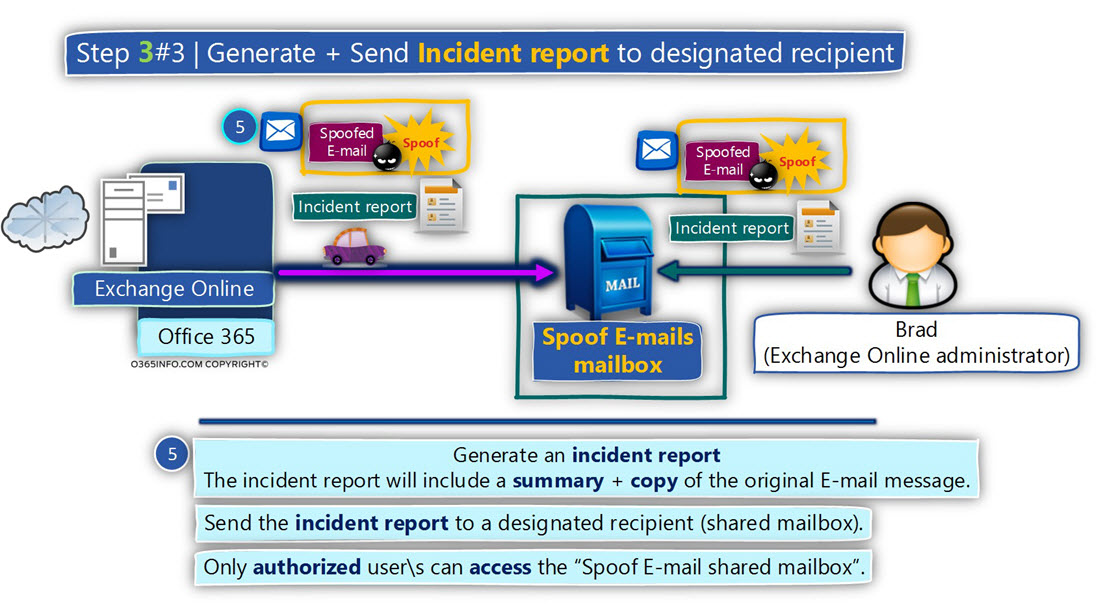
Only authorized user\s can access the “Spoof E-mail shared mailbox”. In our specific scenario Brad (Brad is our Exchange Online administrator) will have access to the shared mailbox.
In the following diagram, we can see the sequence of actions, that will be implemented by the Exchange Online Spoofed E-mail rule:
Note: Although the information in the current article was written about Office 365 (Exchange Online) based environment, most of the information is also relevant to Exchange on-Premises based environment.
Configuring Exchange Online Rule That Will – – add a disclaimer to the E-mail + prepend the E-mail subject
In the following section, we will provide “step by step” instructions for creating the required “Exchange Online Spoofed E-mail rule” that will answer our business needs.
Part 1#2 – configuring the “condition part” of the Exchange Online Spoofed E-mail rule
- Log in to the Exchange admin portal
- On the left menu bar, choose –mail flow
- On the top menu bar, choose –rules
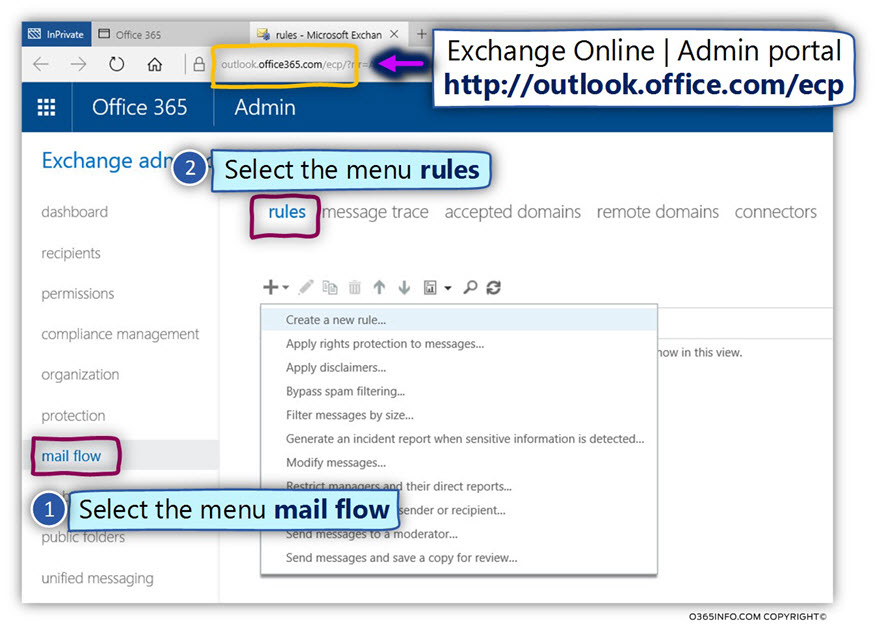
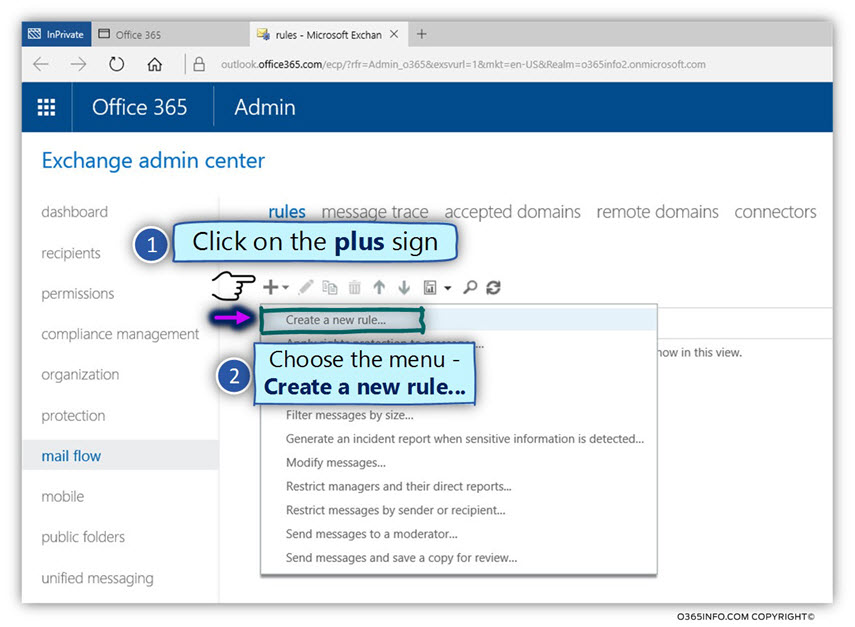
- Click on the plus icon
- Choose – Create a new rule…
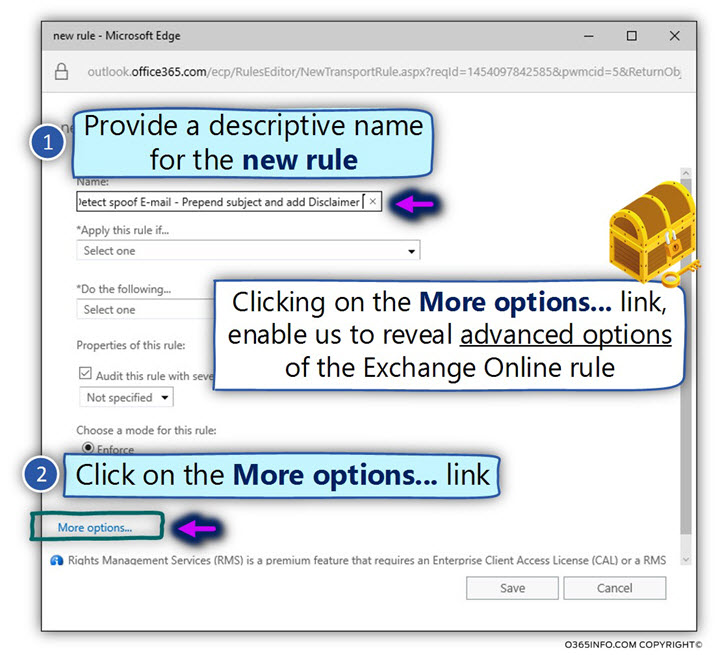
- In the Name: box, add a descriptive name for the new rule.
In our specific scenario, we will name the rule – Detect Spoof E-mail –Prepend subject and add Disclaimer - Click on the –More Options… link (by default, the interface of the Exchange Online rule includes only a limited set of options. To be able to display the additional options, we will need to “activate” the More Options…).
- In the section named –Apply this rule if… click on the small black arrow
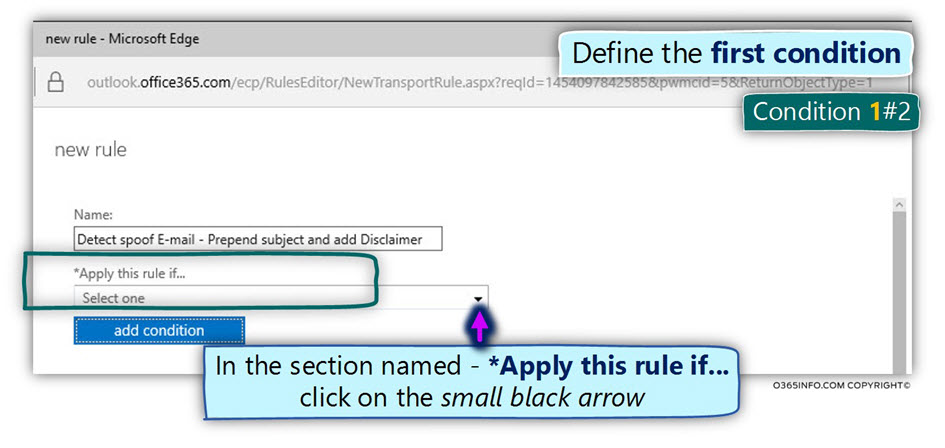
Condition 1#2
- Choose the primary menu –The sender…
- In the submenu, select the option –Is external/internal
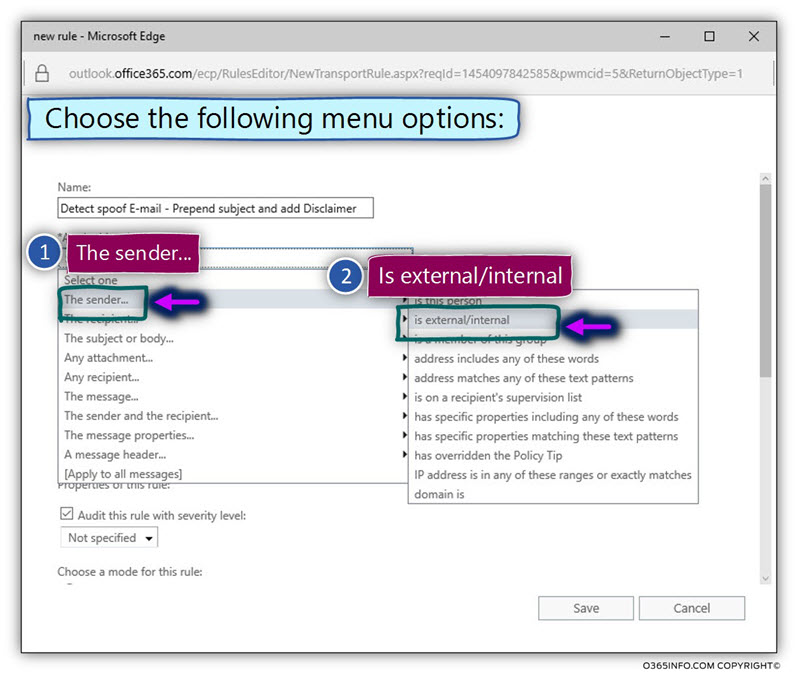
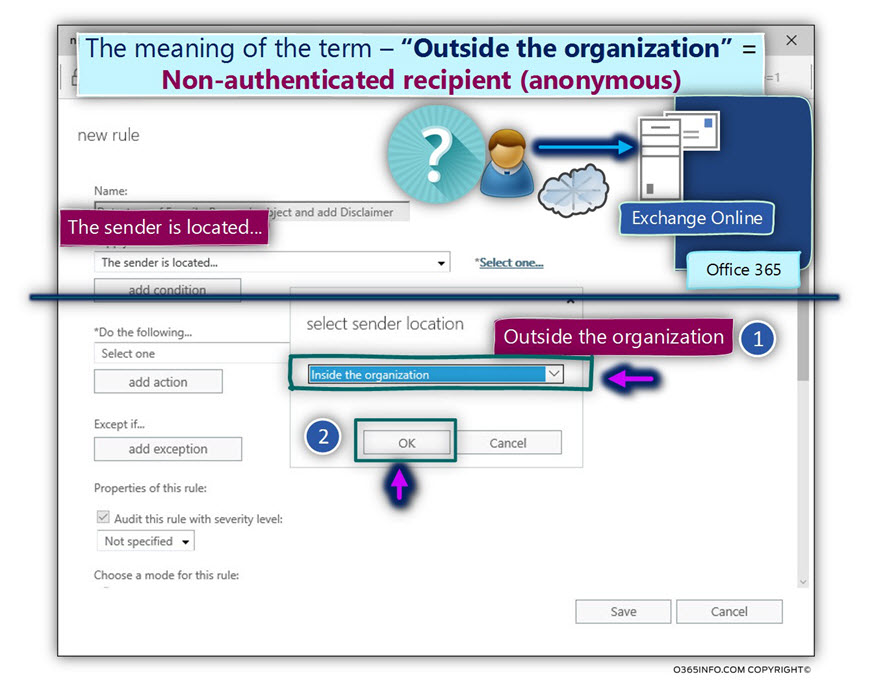
- In the select sender location window, choose the option – Outside the organization.
The meaning of the term “outside the organization”, relates to a un-authenticated recipient, meaning – a recipient that doesn’t provide user credentials to the mail server.
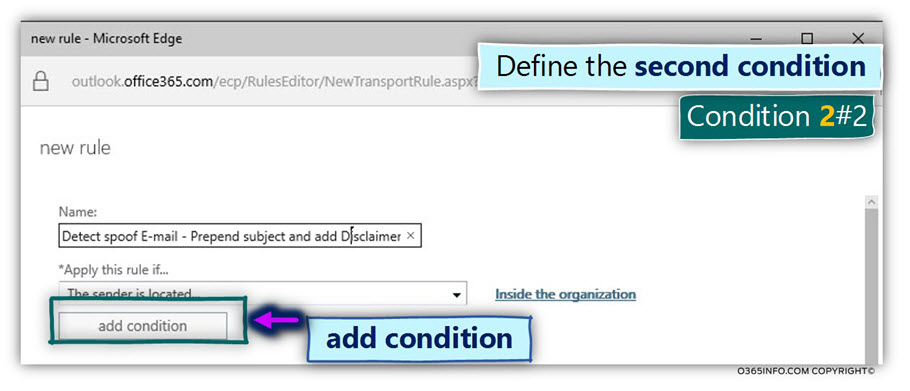
Condition 2#2
Now, we will add an additional “layer” to the “rule condition”, in which we relate to
the recipient who uses an E-mail address that includes our domain name (o365pilot.com in our specific scenario).
If you would like to read more information about the meaning of the Exchange Online terms– “External sender” and “outside the organization“, read the following section: Dealing with an E-mail Spoof Attack in Office 365 based environment | Introduction | Part 1#12
- Click on the – add condition.
- In the section named – and click on the small black arrow.
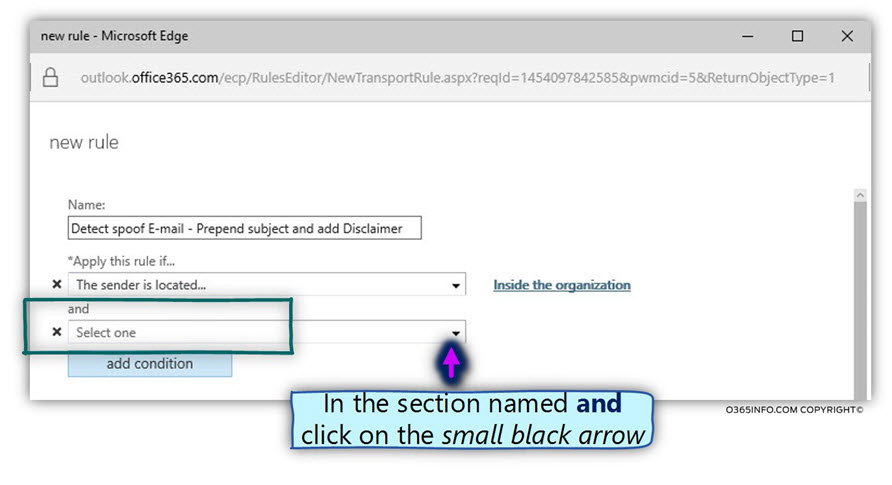
- Choose the primary menu – The sender…
- In the submenu, select the option – domain is
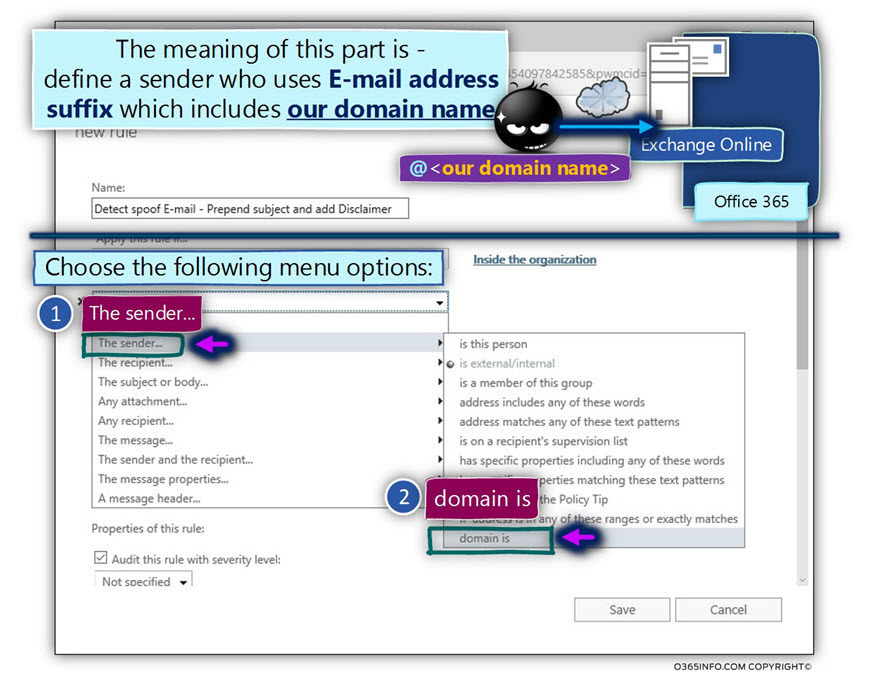
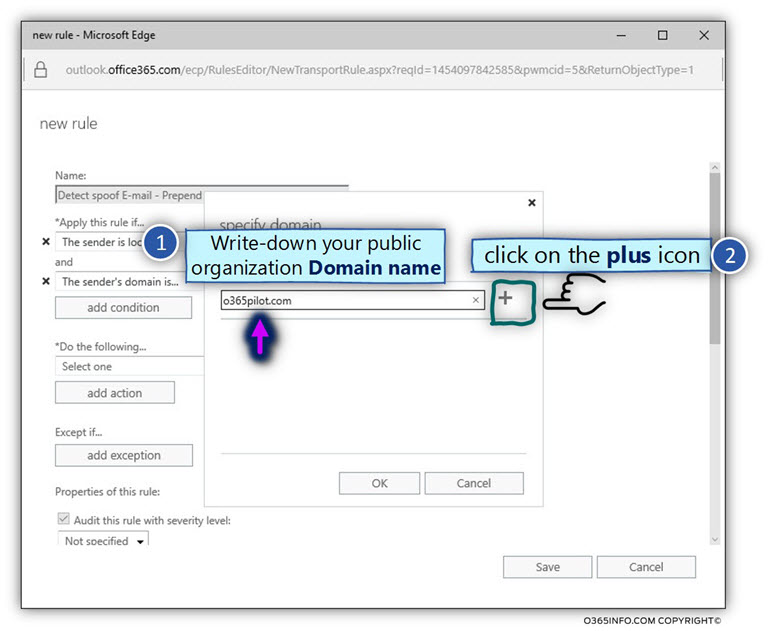
In the specify domain window, add the required domain name that represents your organization.
In our specific scenario, the public domain name is – o365pilot.com
Note – Don’t forget to click on the plus icon to add the domain name.
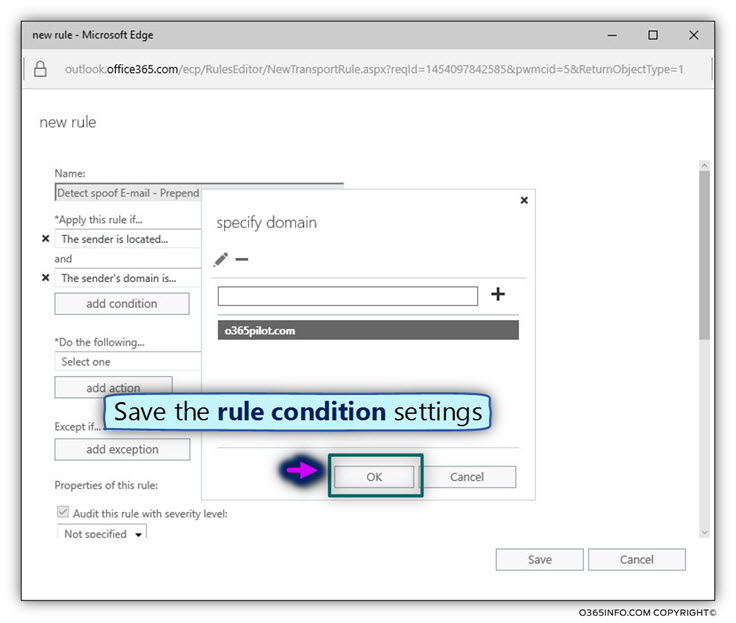
Click on the OK option to save the Exchange Online rule settings.
Part 2#2 – Configuring the “action part” of the Exchange Online Spoofed E-mail rule
In this phase, we will configure the “second part” of the Exchange Online rule, in which we define the required Exchange response (action) to a scenario of spoofed E-mail that sent to one of our organization recipients.
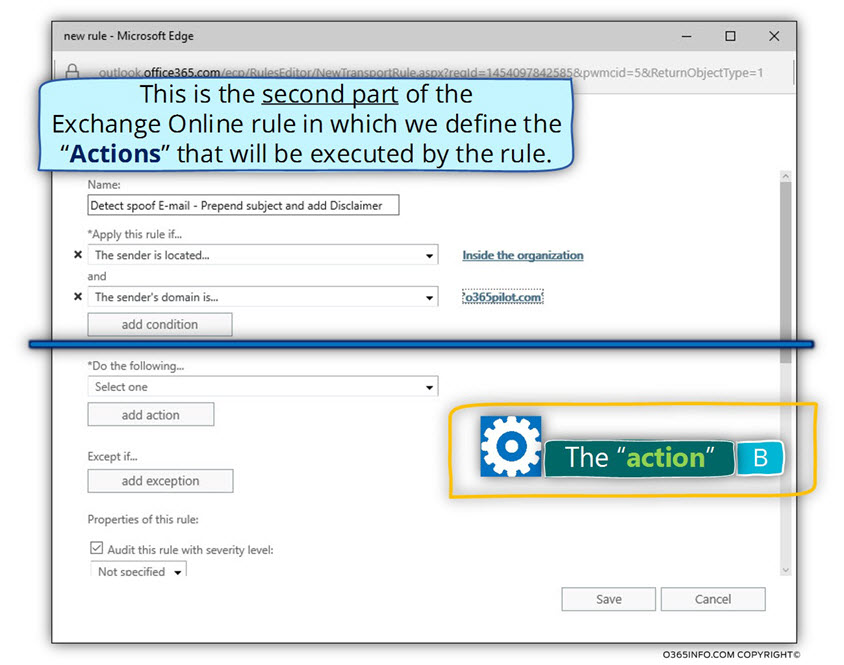
In our situation, we wish to instruct Exchange Online to respond to the event in which
E-mail identified as Spoof E-mail by implementing the following actions
Action 1#3 – Prepend E-mail message subject.
- In the section named – Do the following… click on the small black arrow
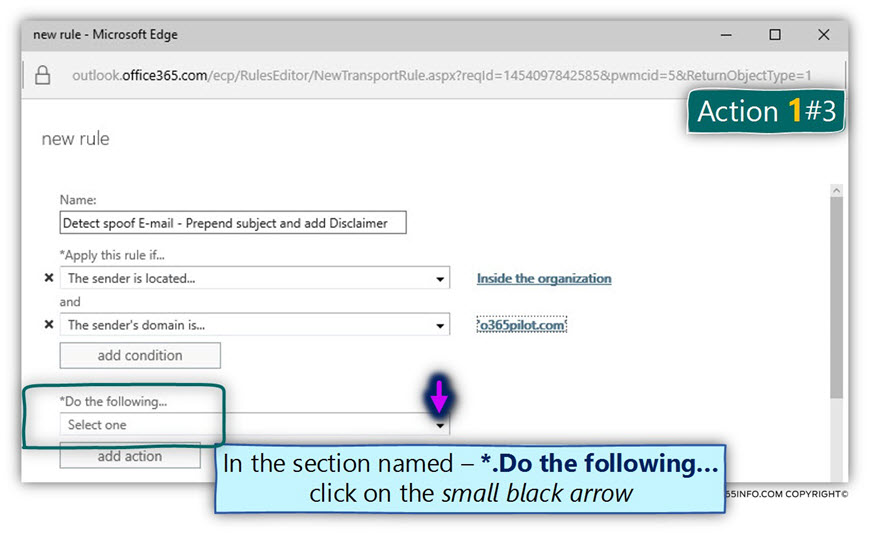
- Choose the menu option – Prepend the subject of the message with…
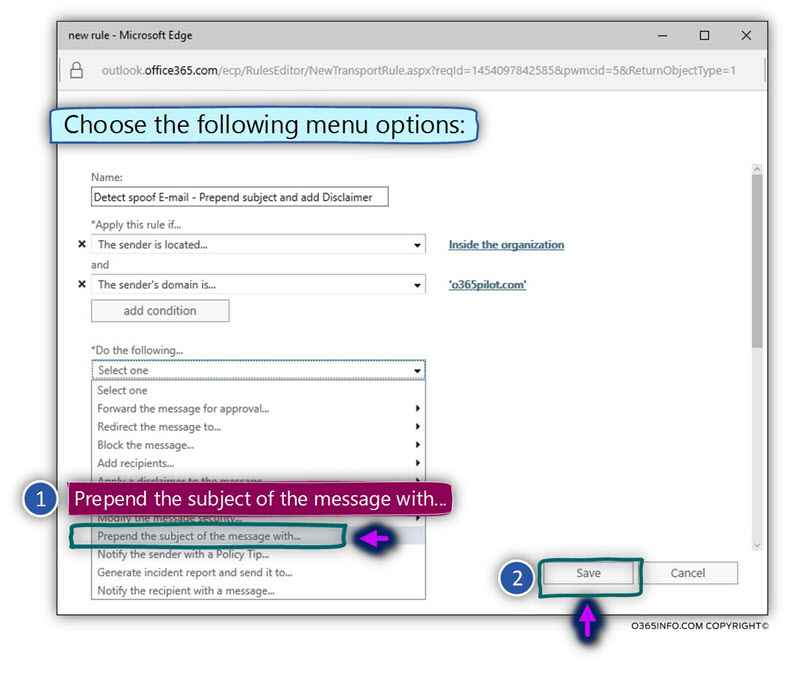
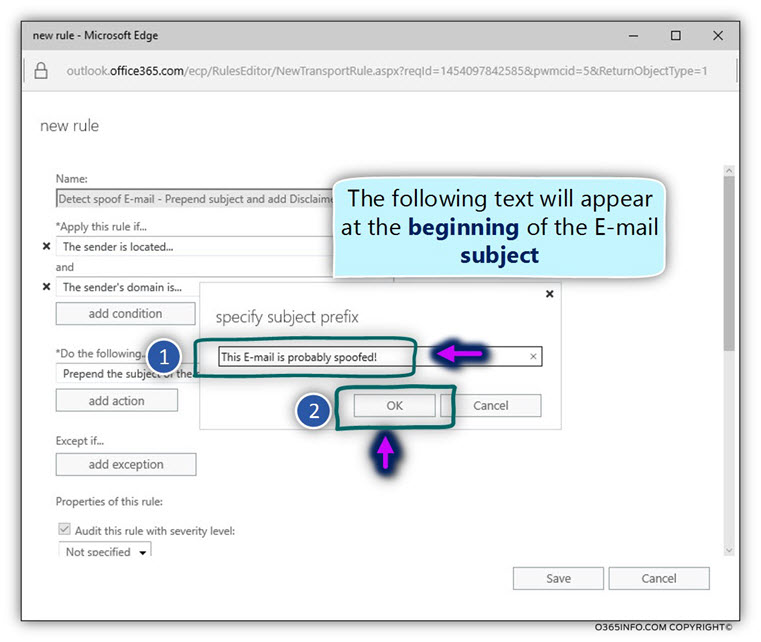
In the text box – specify subject prefix, add the required prefix.
In our specific scenario, we will add the prefix – This E-mail is probably spoofed!
Note: There is a limitation for the maximum number of Characters.
The estimation is 32~ characters
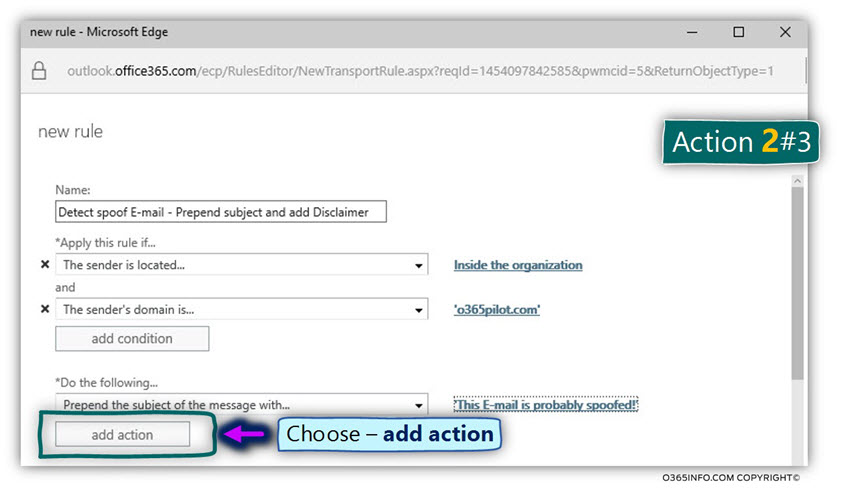
Action 2#3 – Add a disclaimer to the E-mail message.
In this phase, we will add the “second action” in which we add a disclaimer to the E-mail message that identified as Spoof email.
- Click on the add action option
In the section named – and click on the small black arrow
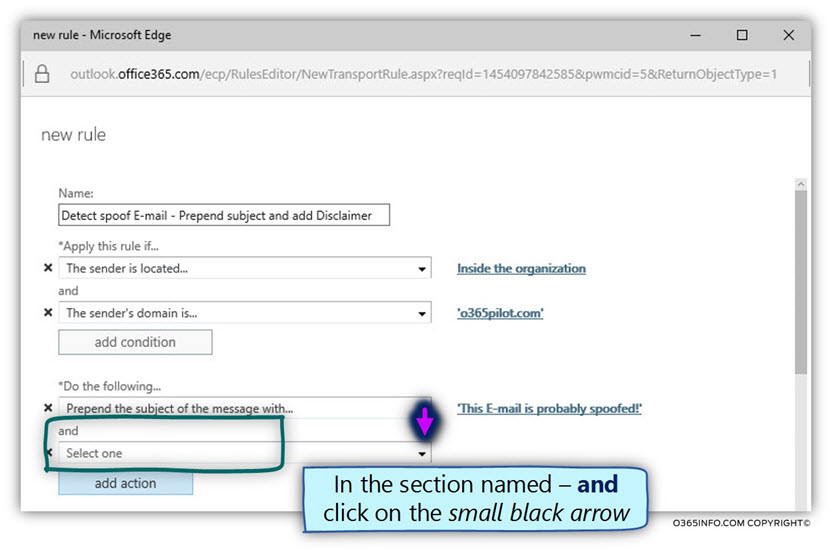
- Choose the menu option of – Apply a disclaimer to the message…
- In the submenu, choose the option – append to disclaimer
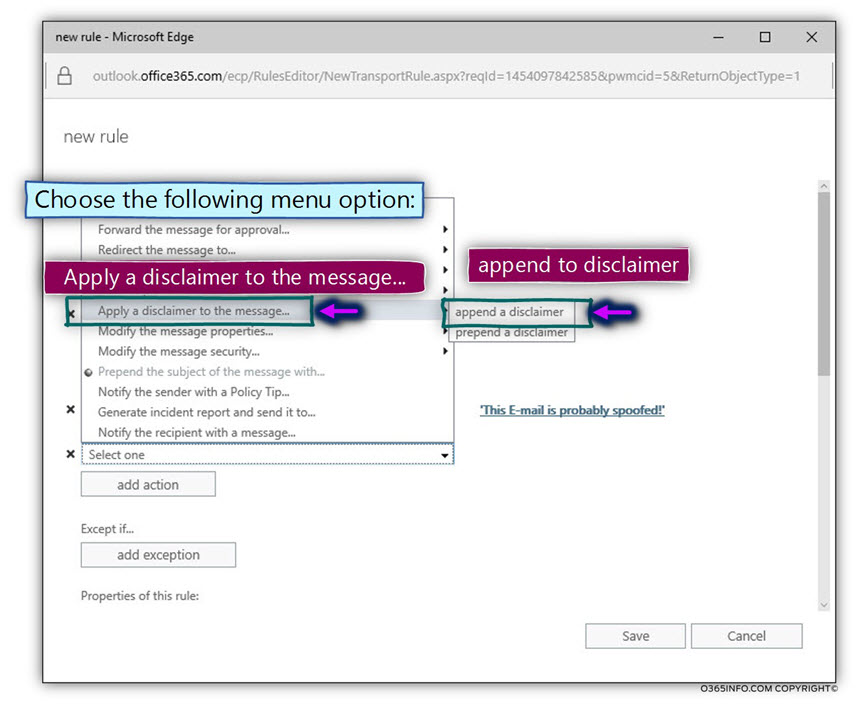
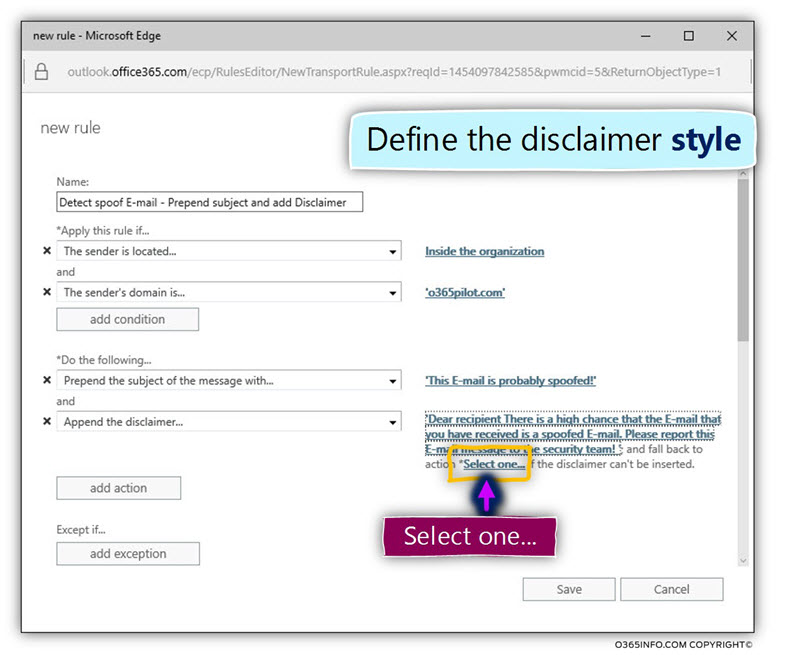
The configuration of the disclaimer includes two elements:
- The disclaimer text
- The fallback action
- To add the required disclaimer message, click on the Enter text… link
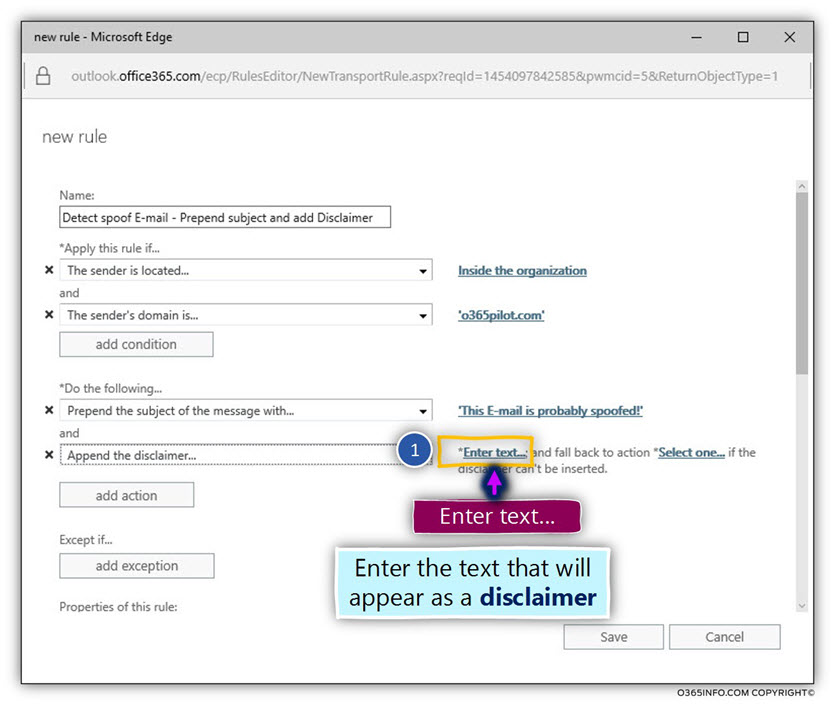
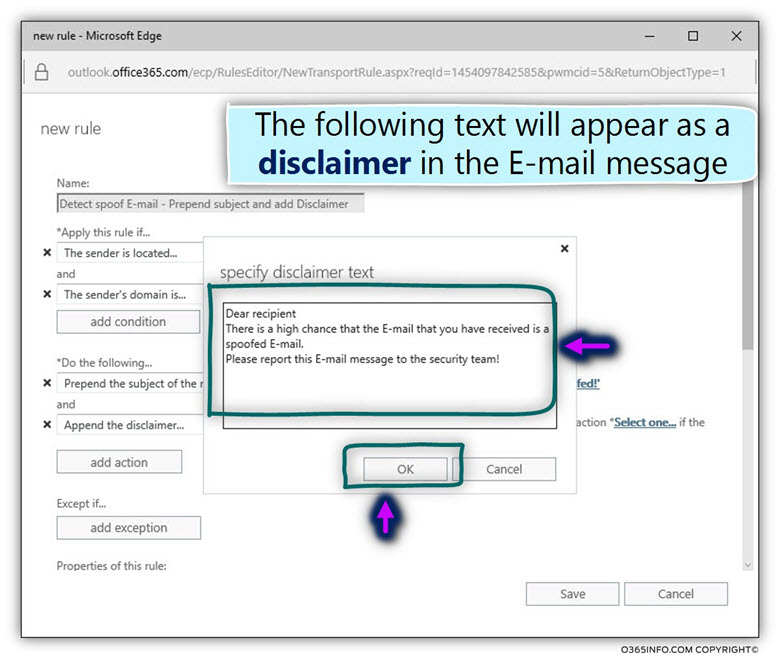
In our scenario, the disclaimer text is:
Dear recipient
There is a high chance that the E-mail that you have received is a spoofed E-mail.
Please report this E-mail message to the security team!
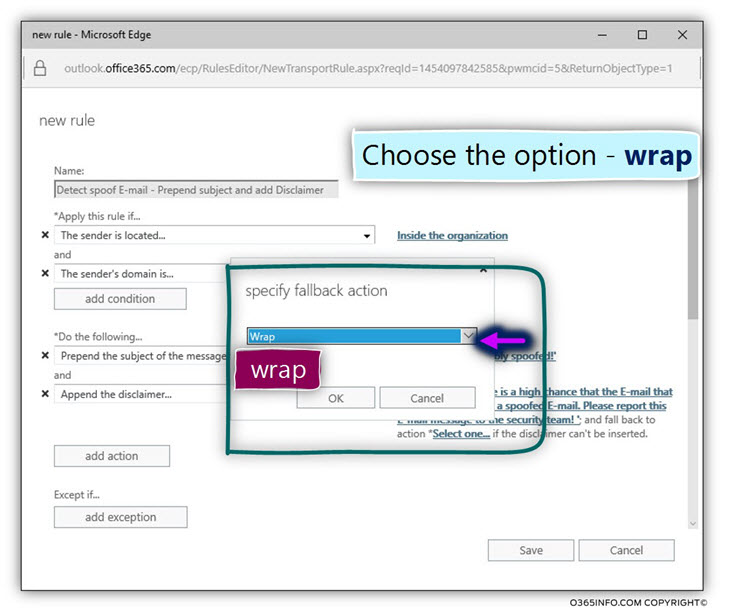
- To select the required fallback action, click on the link named – *Select one…
In our specific scenario, we choose the option of – wrap
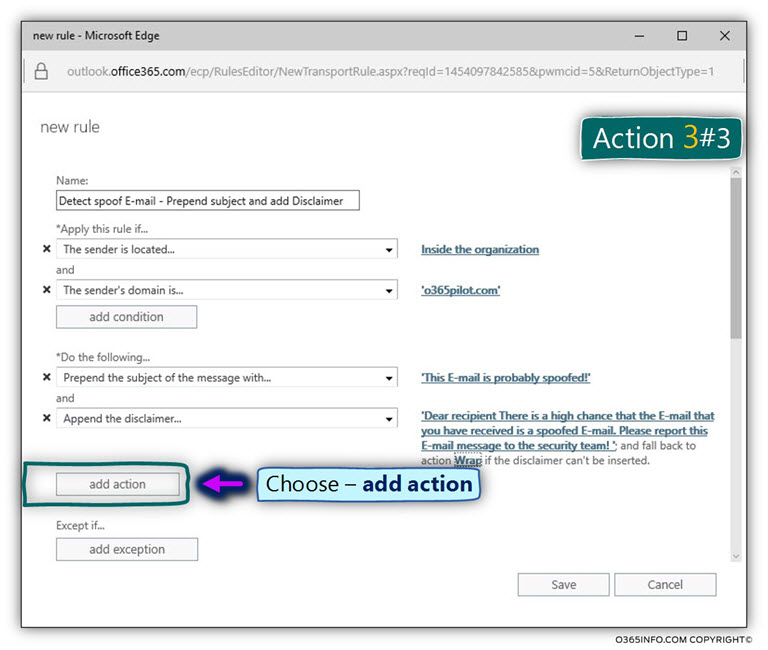
Action 3#3 – Create an incident report and send it to a designated recipient.
- Click on the option – add action
- In the section named – *.and… click on the small black arrow.
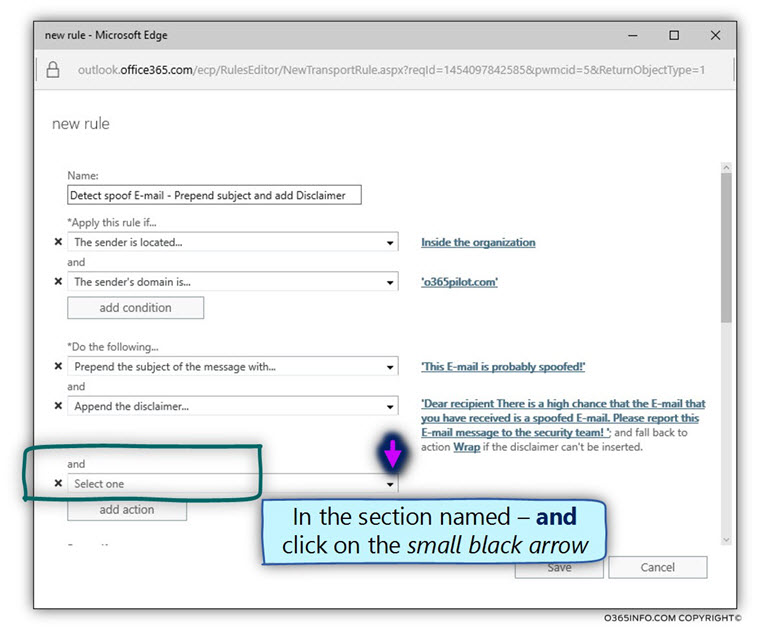
- Choose the menu option – Generate incident report and send it to…
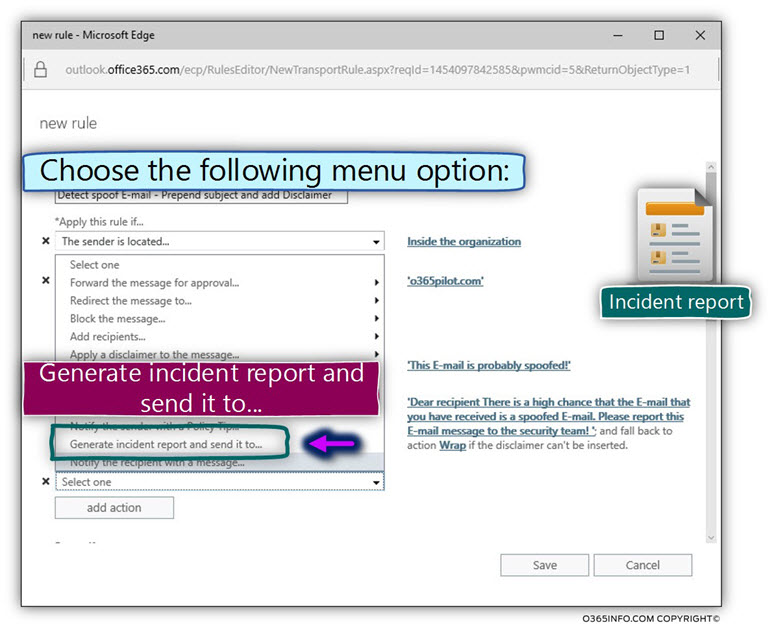
The settings of the incident report include two parameters:
- The name of the “destination recipient” which will get the incident report.
- The information fields that will be included within the incident report.
- To add the required “destination recipient” name, click on the link – Select one…
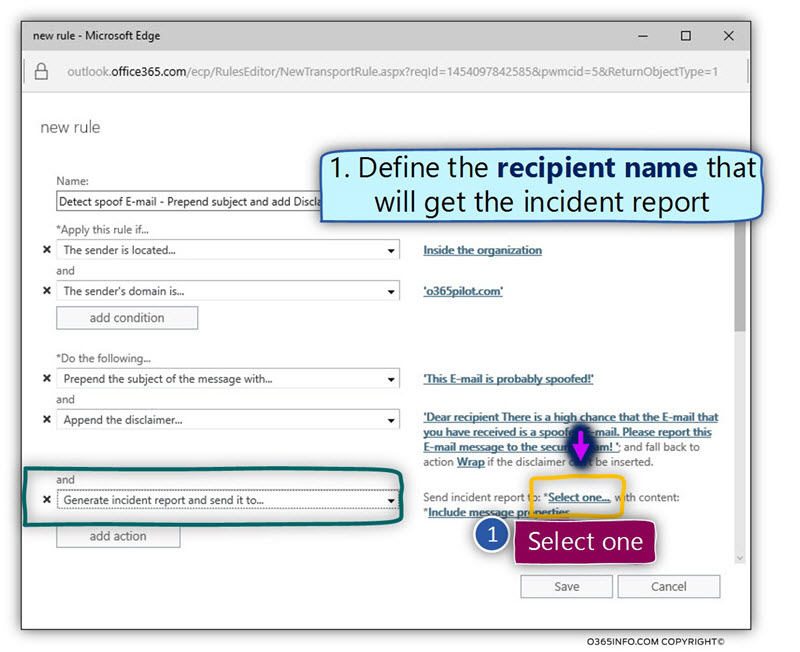
- In our specific scenario, the recipient who will get the incident report is Spoof E-mails mailbox.
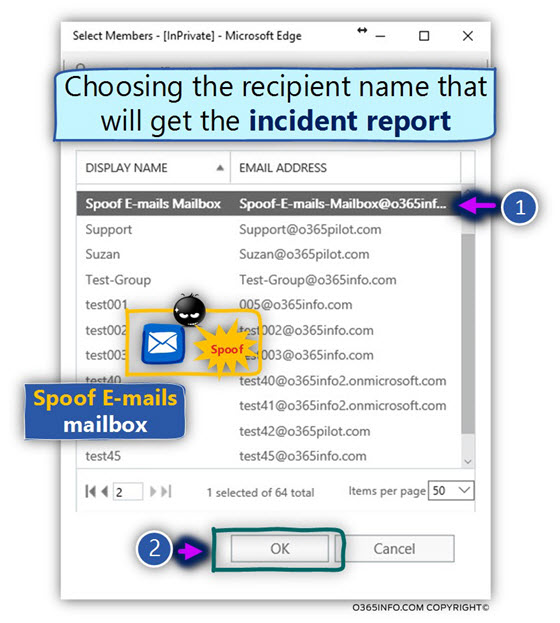
To select the information that will be included within the incident report, click on the link named-*include message properties
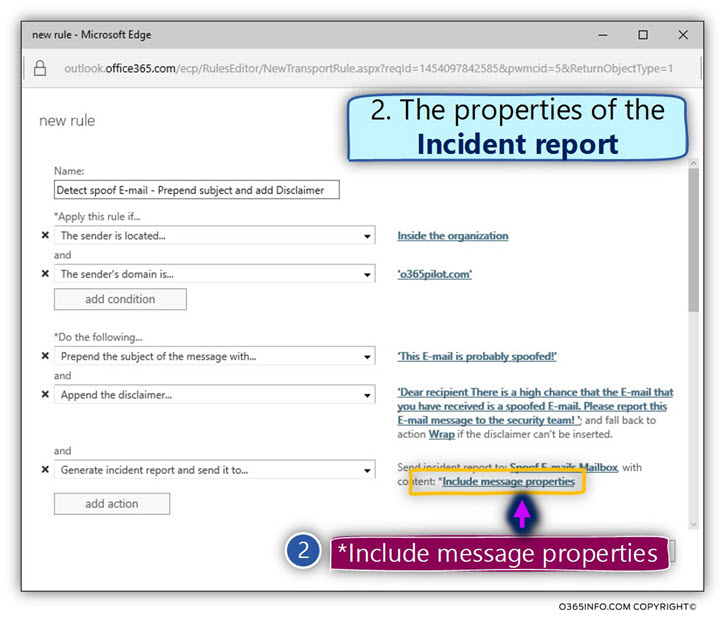
In our scenario, we will choose to include all the available message properties in the summary report + a copy of the “original Spoof E-mail message”.
- Select the option – Select all
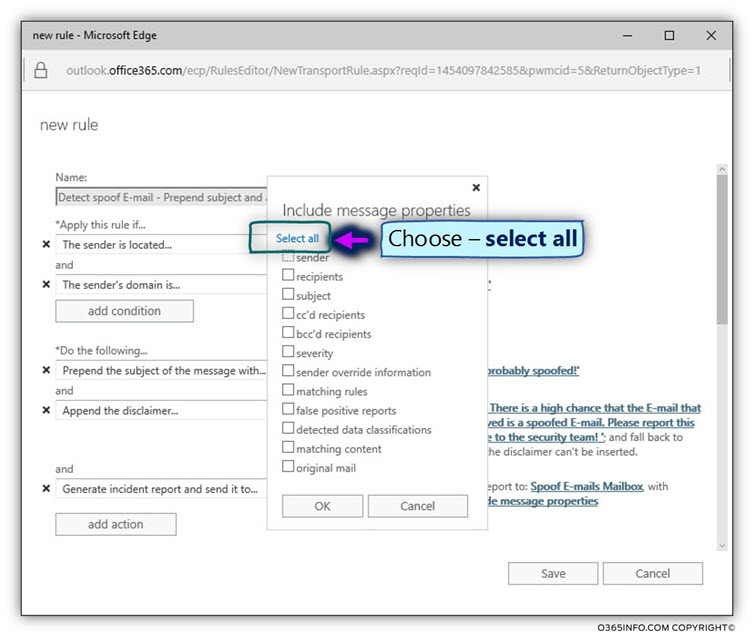
In the following screenshot, we can view the available options:
- Part A – relates to the info that will appear in the incident report summary.
- Part B – relates to the option of “attaching” copy of the original E-mail message to the incident report.
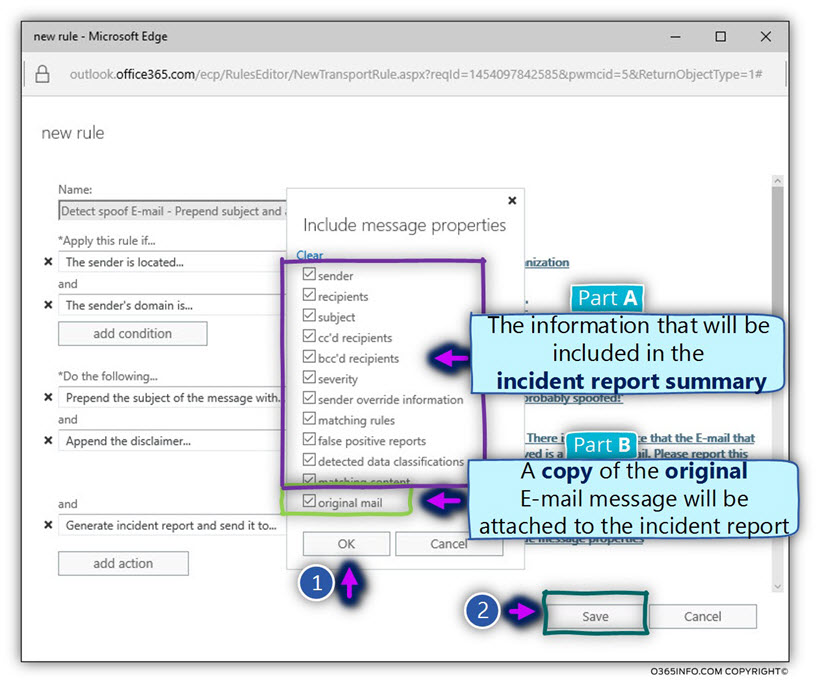
In the following screenshot, we can see the “final result” – the Exchange Online Spoof email that includes the two parts:
- The condition part
- The action part
Verifying That The Exchange Online Spoofed E-Mail Rule Is Working Properly
In this phase, we would like to test the Exchange Online Spoof E-mail rule that was created in the previous step, and verify that the rule is working properly.
The required results from the Exchange Online Spoofed E-mail rule
Our desired expectations are – when Exchange Online identifies events in which E-mail messages that sent to our organization recipient have a high chance of being spoofed E-mail (spoofed sender), the Exchange Online Spoof E-mail rule will execute that following sequence of actions:
- Prepend the E-mail subject.
- Add a disclaimer to the E-mail.
- Generate an incident report, that will be sent to the E-mail address of the designated recipient\s. In our specific scenario, we ask to send the incident report to a designated recipient (shared mailbox named – Spoof E-mail mailbox).
Simulate a Spoof E-mail attack | Scenario characters
To be able to ensure that the Exchange Online Spoof E-mail rule is working properly, we will simulate a spoof E-mail attack that has the following characters:
- A “hostile element” is trying to spoof the identity of a legitimate organization recipient named –Suzan using the E-mail address – Suzan@o365pilot.com
- The spoofed E-mail message will be sent to a legitimate organization user named Bob, which uses the E-mail address – Bob@o365pilot.com
If you like to learn about the way that we use for simulating the E-mail spoof attack, you can read the article – How to Simulate E-mail Spoof Attack |Part 11#12
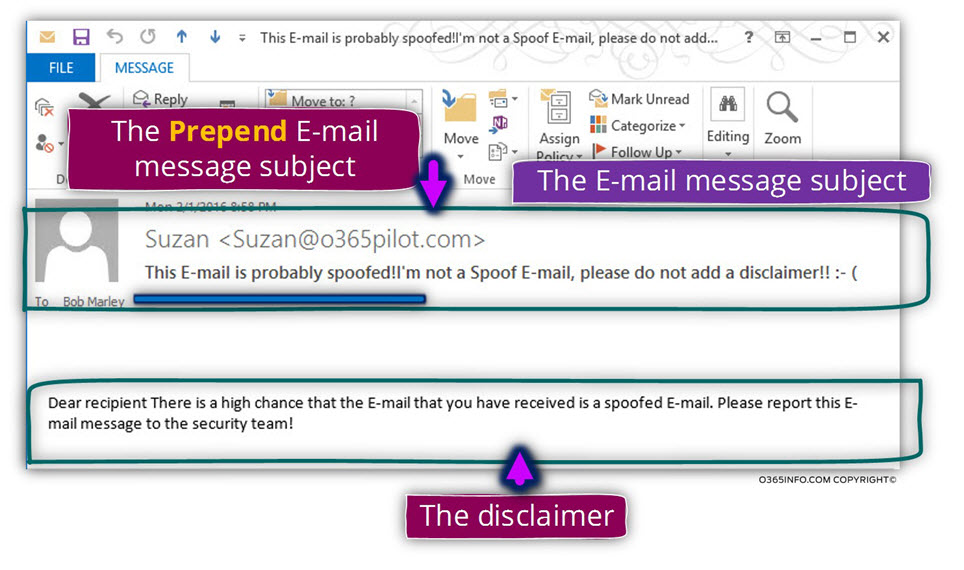
Step 1#2 – verifying that the spoofed E-mail subject was prepended + include a disclaimer.
In the following screenshot, we can see an example to a Spoof email that sent to Bob by “Suzan.”
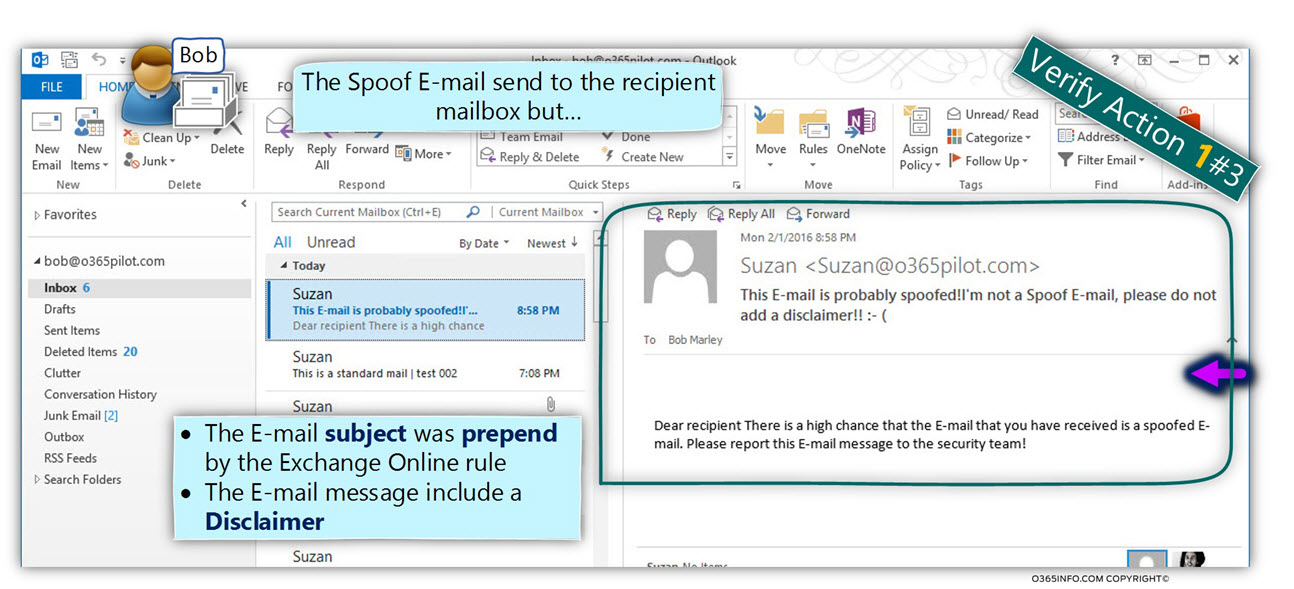
When looking at the E-mail message content, we can the E-mail subject that includes the “original subject text” (in our particular example – “Hello Bob, it’s me, the company CEO, send me your bank account”), and the prepend text – “This E-mail probably spoofed! “
The E-mail message body includes the disclaimer that configured in the Exchange Online Spoof email rule.
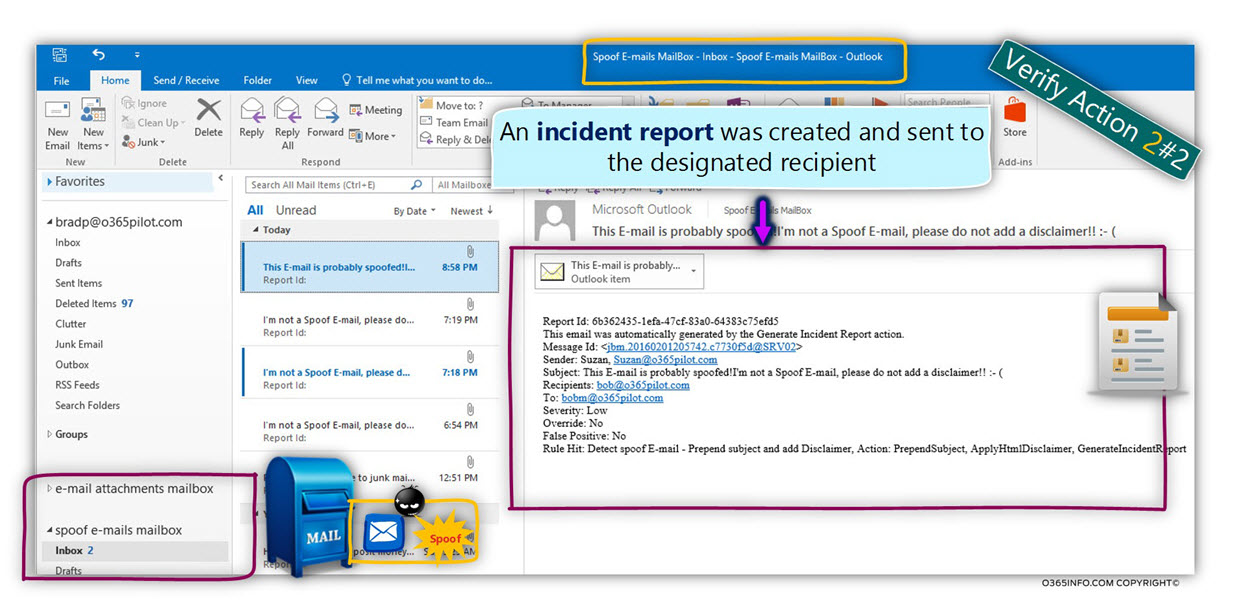
2#2 – verifying that an incident report sent to the designated recipient.
We can see that Exchange Online rule “capture” an event of Spoof E-mail.
As a result, an incident report was sent to the recipient name (Spoof E-mails mailbox) that configured in the Exchange Online rule.
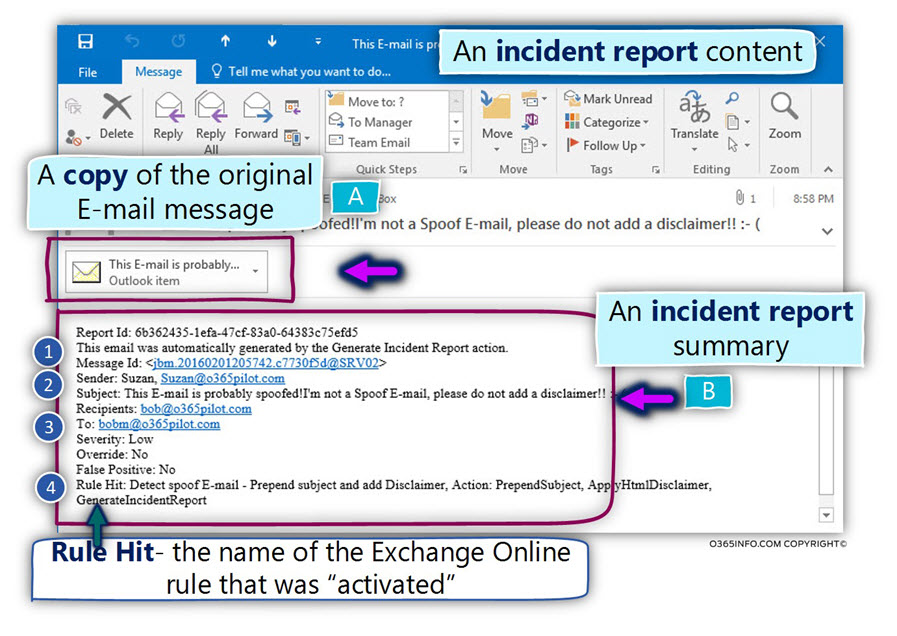
In the following screenshot, we can see an example of the incident report E-mail.
When we look into the incident report, we can see that the incident report includes two parts:
- The copy of the original E-mail message (A).
- The incident report summary (B).
The incident report summary includes details such as:
- Information about the generator of the incident report E-mail message – “This email was automatically generated by the Generate Incident Report action” (number 1).
- Sender – the sender (the “source recipient”) that claim to be a legitimate organization recipient named –Suzan@o365pilot.com (number 2).
- To – the recipients (the destination recipient) is –Bob@o365pilot.com (number 3)
- Rule Hit – the Exchange Online rule the “capture” the spoof E-mail event, and the action that was executed by the Exchange Online rule –”Detect spoof E-mail – Prepend subject and add Disclaimer, Action: PrependSubject, ApplyHtmlDisclaimer, GenerateIncidentReport” (number 4).
Check our video: Detect spoof E-mail and add disclaimer using Exchange Online rule | 4#7
The next article in the current article series
In the next article – Detect Spoof E-mail And Send The Spoof E-mail To Administrative Quarantine Using Exchange Online Rule |Part 7#11, we will review how to create an Exchange Online rule that will identify events of spoofed E-mail and as a response, will – send the spoof E-mail to administrative quarantine.



How do you handle outbound messages that now have “external” in the subject when replying? Do you strip “external” string?